Information Security's Historical Foundations
Introduction
Information technology and information security are becoming the integral elements of modern life. The use of information is said to permeate key aspects of the private lives and businesses at the same time. Most of the organizations are in need of the information systems for them to survive as well as prosper. However, most of them are unaware of possible repercussions that come along with information insecurity and the need to protect the information assets. At some point, the human incorporated behaviour seen through negligence as well as lack of knowledge has contributed to dominant cases of information insecurity. Based on the vast concept of information security, this context reflects on the Babington Plot and the entire view of the information security perspective. History has it that on 8th February, 1587, Mary Stuart, sometimes known as Mary Queen of Scots, faced execution for her attempt of assassinating Queen Elizabeth 1st of England. The evidence in place is said to have been in form of letter between Antony Babington and Mary Stuart, which later materialized into what is referred to as the Babington Plot. The letters are said to have been intercepted as well as decoded by the Spymaster known as Sir Francis Walsingham. Based on this, the discussion will establish the information security techniques applied by Antony Babington and Mary Stuart in protecting their communications, interception by the Nation States, description of the technology used in ensuring confidentiality and integrity of attachments and messages and the convenient use of the Thunderbird email client that is installed on the Ubuntu VMS. The discussion conforms to theoretical arguments, the evidence provided, the evidence of IT growth and progress, as well as the value of changes that have occurred overtime.
Information security techniques used
In the course of imprisonment of Mary, history states that a number of techniques as well as channels could be used for communication. The Babington Plot constituted the conspirators who worked on alternatives after Queen Elizabeth blocked all communications from Mary (Pollen1922). Upon establishing a new communication line, Mary could receive the information that was delivered as diplomatic packages from the French ambassador to England. The packages could be passed to Gifford who handed them to Walsingham. The latter would then engage Phelippe, a cryptanalyst, to decipher as well as copy the entire letters before resealing them and return to Gifford (Meyer 2016). The letters would then be handed to a local brewer before smuggling them to the imprisoned Mary. The flow of information questions the nature of the information security techniques that were used in the course of delivering the message to Mary. The key technique that was used to ensure information security is known cipher, which is commonly referred to as encryption in the modern day (Gamble 1991). The cipher was said to be unbreakable and impossible to many people apart from few figures such as Thomas Phelippes.
Continue your exploration of Introduction to VoIP Security Risks with our related content.
Across the cipher, the nomenclature applied by Babington and Queen Mary comprised of the abstract alphabets, word symbols and null, which masqueraded the details shared between the henchmen and the Queen. The incident that occurred on 7th July 1586 showcases the meaningful use of the cipher in the Babington letter that was sent to Mary. The latter further responded in a code with an order to assassinate Queen Elizabeth. However, the letter was deciphered and used against her during her execution after submissions from her secretaries Curle and Nau. However, it should also be noted that the applicable nomenclature cipher in the course of ensuring confidential communication was improvised by Walsingham (Hutchinson 2007). The nomenclature cipher was quite common and dominated the better part of the 16th century for the purposes of securing communications. Common characteristics of this type of encryption included the homophonic substitutions for the purposes of achieving three key goals, which include availability, confidentiality as well as integrity. In the course of the communications between Mary and Babington, it is stated that Queen Mary’s complacency that appeared in her writing paved way for weak encryption, which must have been the cause of her execution (Evans 2016). It should also be noted that previous letters shared between Mary and Babington could not clearly be decoded.

At the beginning of 1586, Gifford is said to have received a letter of introduction from Thomas Morgan. The letter was meant to introduce Queen Mary to Gifford. The latter became more significant as he played a focal role in organizing the encrypted communications to be put in a beer barrel cork before reaching the imprisoned Mary (Shukla and Kumar 2012). There are several reasons as to why making use of nomenclature cipher between cipher and Mary never met the objective. First, making use of double agents must have failed the mission of ensuring information security. Gifford, a trusted confidant of Thomas Morgan and Queen Mary, who organized how the encrypted messages would be transferred from Babington to Mary, was a double agent who worked for Walsingham, the Spymaster. Gilbert Gifford was introduced in the Walsingham service towards the end of the year 1585 and he accounts for the larger part of the interception, intermissions and interference to the flow of communication between Babington and Queen Mary (Griffin 1997). He could intercept the letters before passing them to Phelippes who would then decrypt the message before the letters could be resealed and passed on to Mary.
Secondly, there were so many spies who could not be suspected or identified in the course of communication. The spies included Robert Poley and Thomas Phelippes who doubled as the cryptanalyst. The diplomatic packets could be passed to Chateauneuf who would pass the same to Gifford before they could reach Walsingham (Meyer 2016). The packets could later be confided to Phelippes before he could encode the entire letters. In the final letter, Phelippes deciphered it and decided to keep the original as he sent a copy which additionally requested addition of names of all the conspirators. The copy must have been the cause of turbulence in the Mary’s camp leading to the arrest, conviction and execution of the conspirators (Holmes 1987). A relook at the three stages of an encrypted message reveals the following.
Confidentiality: The key device deployed by Mary and Babington, among other conspirators, was to address the idea of confidentiality in the encoded letters that applied the nomenclature cipher. The message was to be understood between the two parties, which involved the senders, including Babington and conspirators, and the receiver, the imprisoned Mary (Meyer 2016). However, vulnerabilities could still be detected in the course of their communication and the subsequent designs. The secrecy and confidentiality of the cipher was in the due course compromised, which means all the communications could be decoded as well as recorded for reference purposes. In addition, only a single and common cipher was applied, which means that once the cipher is being decrypted by the interceptor, the rest could follow suit and rendered insecure (Swain 2013). Lastly, it was difficult to verify the secrecy and confidentiality of the cipher. This can be justified by the fact that no mechanisms were introduced to detect possible leakages.
Integrity: Across the scope of information security, integrity would commonly refer to the course of maintaining consistency, trustworthiness as well as accuracy of data. This means that information should not be changed in the course of transit and the packets should not land in the hands of the authorized persons. In this context, no mechanism was applied in confirming the integrity of the messages (Singh 2016). The communication chain was frequently intercepted by Walsingham with the help of his aids men. In the authorization request behind the assassination plan, Walsingham hijacked and kept the original letter and a duplicate letter was later forged with instructions set to reveal the co-conspirators as well as their roles in the entire assassination plan.
Availability: From the modern information security point of view, minimal considerations were adopted in confirming the availability of the significant messages. The evident meandering routes seen in all communications as well as the long distances confirm the missing or absence of the high-speed data transmission technique (Meyer 2016). However, Walsingham ensured a steady communication between the conspirators and the imprisoned Mary, which created loopholes in the communication cycle.
Interception by Nation States
From the above section, it is evident that Walsingham intercepted the letters from Babington to the imprisoned Queen Mary. Given that he was a spymaster, Walsingham was one of the government officials who ensured that Queen Elizabeth 1st had the most deserving powers as the head of state. The mission set out and executed by Walsingham can be argued alongside the interceptions and spy-missions conducted by government agencies within the Nation States (Fitsanakis 2003). Many reasons have been floated by different Nation States as to why such interceptions are necessary in the interest of the security of state. Most states believe that it is impossible to organize a crime without communicating through the public networks (Riley et al. 2005). Most of these networks can easily be intercepted for the purposes of exploiting the weaknesses noted with the criminal structure. The first reason for interception revolves around the need to conduct an investigation of a serious crime, which can be lethal to the National interest. In the year 1998, over 2031 interception warrants are said to have been issues by the Home Secretary, as well as the Secretary of State for Scotland. The warrants encapsulated serious crime incidents, which are defined as an act of violence that involves a network of persons that are in pursuit of a common goal or purpose, which has negative repercussions to the general republic (Schuster et al. 2017).
Secondly, integration of modern technologies has been considered for the purpose of maintaining national security. For this case, interceptions are legitimized with the central purposes of achieving criminal justice as referred to the technological progress and novel science. This means that interception of the phone calls and other audio recordings cannot be considered as part of the violation of privacy with reference to prescribed regulations and laws. In most of the Arabic states, any form of interception stands justifiable grounds as far as conclusion of the judgment is required. Overtime, interceptions are being legalized as it is the case of the Interception of Communications Act 1985 (Cameron 1986). Challenges behind IOCA have been defended over the period as it is the case of Strasbourg. In the Campbell v. United Kingdom cases in 1994, the Applicant is said to have been the General Secretary of Scottish Trades Union Congress. Powers to intercept were justified with the degree of certainty as the commission abided by the cases of Hewitt and Harman and Esbester (Sutherland 2013). However, interceptions posit risks to individuals and commerce as far as protection of parties is put into consideration. The fear of interception via wiretapping may become the ultimate procedure across the investigation process, which subsequently influences the beliefs of judges while rendering other pieces of evidences inconsequential (Mountz 2004). The adverse reliance on interception can equally deteriorate the presumption of innocence doctrine, which has been set out the principle in international conventions.
Secure Email
The frequent interception and disruption of the communication cycle means that the cipher used between Babington and Queen Mary never achieved the intended mission. However, an alternative use of the modern day email would have changed the cycle as messages would become more protected compared to nomenclature cipher, which could easily be decrypted by Phelippes. Common modern-day techniques that would achieve the required level of protection include the Thunderbird email client with the help of Ubuntu VMs, inadvisable network layout, demilitarized zone, mail gateways, and the intrusion detection system (Gramm et al. 2012). Before discussing the Thunderbird email at length, it is good to discuss briefly other methods that would protect the emails if they were to be used by Babington and Queen Mary. First, the demilitarized zone constitutes a host or sometimes a network segment that is commonly introduced as a neutral zone between the internet, and the organization’s private network. It bars users of the mail server from having a direct access to the internal network of the organization (Poddebniak et al. 2018). However, it has commonly been regarded as a compromise solution, which offers significant benefits with minimum amount of risks associated with the organization. On the other hand, the mail gateways are used to protect the mail server by introducing an additional making it hard to launch any attack. The key role played by the mail gateway includes breaking the line of communication between the mail server and internet. However, the most practical method includes making use of Thunderbird email client that has the Enigmail installed on the Ubuntu VMs (Ermoshina et al. 2016). This method is regarded as online encryption for the Linux users. It uses the simple open source tools, which include the GNU PGP, Enigmail, and Mozilla Thunderbird (Poddebniak et al. 2018). The installation starts with installing the GPG. The GNU project always plays a critical role of generating the encryption keys, which are likely to be in the distro’s repositories. Now, the platform is ready for Thunderbird which is easy for the email clients on Linux. After this, the Enigmail can be installed, which is regarded as an add-on for the Thunderbird. One would always be required to open the Thunderbird menu before selecting the add-ons. Eventually, the client will be required to set up the key pair before one can start to encrypt the emails. Enigmail is commonly designed to facilitate the accessible encryption via the Thunderbird. This limits the lengthy configurations as well as complex commands. Before anyone can send or receive the GPG Encrypted email, one is required to exchange the public keys to persons that need to receive or send a message (Ermoshina et al. 2016). To achieve this, the use of Thunderbird with Enigmail can be explored in the following ways.
How to establish trust in the identities of the communicating parties
By use of the Thunderbird with Enigmail, it is possible for one to establish trust identities linked to the communicating parties. This can be achieved through viewing as well as managing the key properties. One can easily generate the key paper and manage the properties by clicking on the Thunderbird menu before selecting Enigmail and Key Management (Zimmermann et al. 2017). Double clicking the key pair will display the following details.
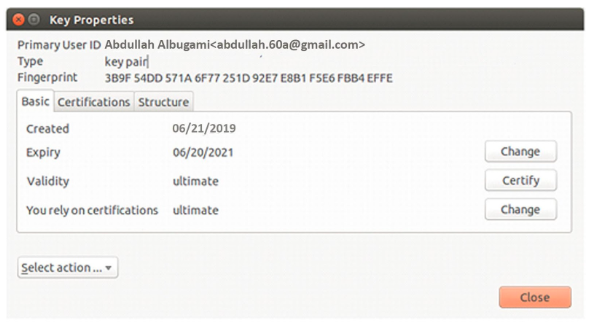
The window will display the public key ID and the fingerprint as well. The expiration date of the key pair can equally be displayed at this stage. Public Keys can be shared with others to allow them to send the encrypted emails. The full fingerprint should also be shared for the correspondents to justify and verify the public key while confirming the parties. In addition, before sending the encrypted email, the sending party and the correspondents are needed to exchange the public keys. Before the identities are fully confirmed, one is needed to conduct the correspondent via a channel that would assure the first person develops confidence and is sure that the receiving end constitutes the intended and the right person (Poddebniak et al. 2018). Personal meetings are strongly advised. However, both the voice as well as the voice conversations can still be allowed in case one is in a position to take the appearance or the voice. In this case, the public key fingerprints can be exchanged between the trusted parties. The fingerprints need to be verified by opening the key properties of the Enigmail window.
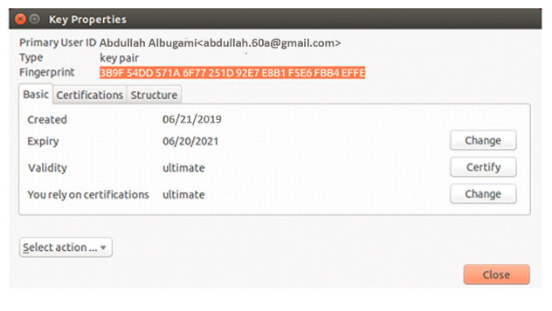
From the window, one can easily see the fingerprint, which can prompt the user to read the entire fingerprint to the correspondent. The user should also ensure that the correspondent can verify the fingerprint as the one that matches the public key the user told the correspondent. In addition, the correspondent should read out the fingerprint for the key pair before closing the verification.
How to ensure that the message and the attachments were sent by the right party
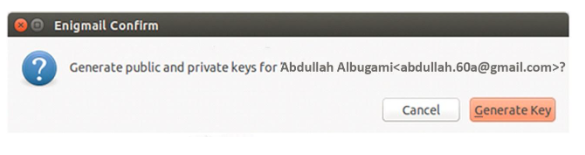
It is good for one to confirm that either message or the attachments or both are from the intended party. While using the Thunderbird email with Enigmail, the GnuPG will depend on the public-key cryptography, which calls for the user to generate a pair of keys. The pair of keys is normally used in encrypting, decrypting as well as signing the digital content as it is the case with the email messages. The pair includes the private and the public key. The private key is thought to be too sensitive and anyone who manages to have a copy stands a chance of reading the encrypted content that is meant for him or her (Mibey 2018). Messages can be signed if and only if they come from the intended party or the right person. Strong paraphrases are commonly chosen for disallowing the unintended party from accessing the key pair. On the other hand, the public key is supposed to be shared and may not be used in reading the encrypted message. However, the moment one has a correspondent public key, it is possible to send as well as receive the encrypted messages. The user is only allowed to decrypt the messages sent to him or her because he or she has access to the right private key, which matches the public key used in encrypting the messages and the attachment. For example, the figure shows the pop up for generation of keys (Securityinabox 2016).
Upon receiving an email, the correspondents are supposed to attach their public keys for the purposes of confirming the source.
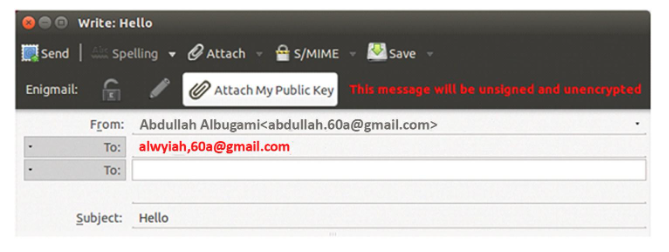
Upon receiving the email from an authentic correspondent, the user is expected to import the public key, which is commonly attached at the lower left corner of the sent email.
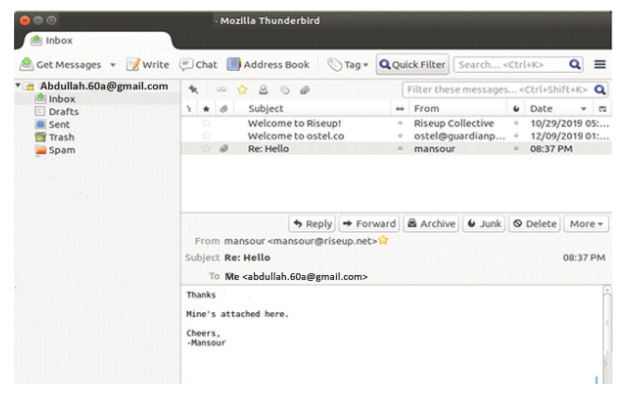
Now, the user can be allowed to right click on the attachment, which prompts him or her to import the OpenPGP key. The Enigmail screen should now indicate the public key from the correspondent before the Thunderbird menu is activated. Once the public key is validated, the user can confirm that the email was send by a legit correspondent and the message not intercepted by any other third party.
How to ensure that the message and attachments have not been altered
The Thunderbird normally has the built-in scam detection tools, or what is commonly referred to as the automatic scam filtering. This is part of the junk filtering functions that would detect the altered messages and classify them as scam (Securityinabox 2016). This happens when the message characteristics are linked to numerical server names such as http://127.0.0.1/. Secondly, when the links do not match the name of the server where the message may indicate https://securelink.com but the link is directed to http://phishingnow.com. Most of the phishers would attempt to intercept and alter the incoming message by using their own site. The legitimate mailing might list the redirectors with the reason of conducting investigations (Kiefer et al. 2012). Upon detection of altered message or scam, Thunderbird will notify the user of a possible attack from a malicious source, which tries to mimic the correspondent. Secondly, Thunderbird will be able to indicate a warning that bars or prevents the user not to click on the link that might have been sent by a malicious person. Most of the illegitimate messages will pile up in the junk folder awaiting confirmation from the user.

The assumption of the junk function tools embedded in the Thunderbird is that the original message and the altered message will automatically showcase different sources. In this regard, the altered message would be directed to the junk folder due to malicious reasons that are detected upon reception of the email. In this case, the user is protected from receiving altered messages. Secondly, the malicious source may capture the message and decrypt it using different tools but fail to confirm the key. Upon delivery to the intended source, Thunderbird may detect key failure, which might lead to suspicions (Hu et al. 2006). Lastly, it can presumed that strong paraphrasing is more convenient in making sure that the user and the correspondent are safe from third parties , who may have or express interests in the message or attachment. In this, strong paraphrasing keeps the knowledge of the transaction between the two parties who may easily feel disruptions from other parties when transactions are not complete. However, there are instances where Thunderbird would categorize a legitimate message as being a fraud. Notably, the Thunderbird’s detection algorithm may not be that perfect and may fail to learn the email flags. Despite the setback, Thunderbird with Enigmail can be an effective tool in protecting the user from receiving altered messages from unintended parties.
How to protect the message and attachments against Interception
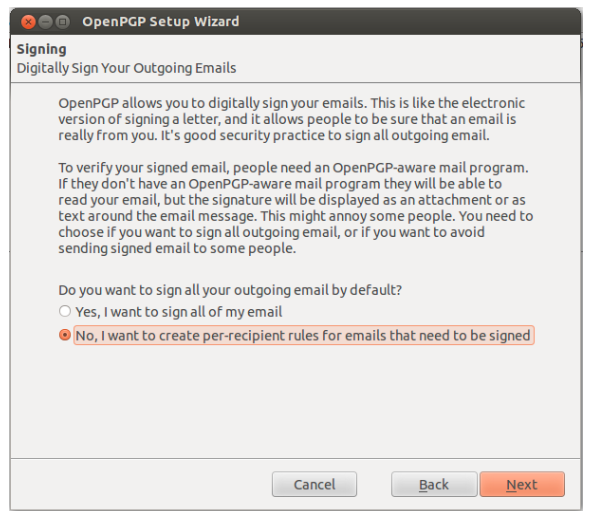
The surest way Thunderbird can secure messages as well as attachments against interceptions is through digitally signing the messages. The GPG feature allows one to sign the messages for the purposes of avoiding corrupted messages, or the ones that have been intercepted in the course of the transmission. Signing the messages also allows the user or the correspondent to verify the sign. This goes alongside confirmation of the fact that the signer of the given message must have used the accepted and legit secret key, which can be verified by the public key shared between the user and the correspondent in the first place (Securityinabox 2016). This further confirms that the secret key was never compromised in the first place. Digital signing of the messages is based on the assumption that almost everyone knows the public key, which means that any person can encrypt the message using it. Based on this, either the user or the correspondent is advised to avoid the unsigned encrypted communications. When using Thunderbird with Enigmail, it is always advisable that one should configure automatic signing (Congleton 2017). By default, the Enigmail never signs the encrypted emails automatically. However, to achieve this, it is advisable that the user or the correspondent finds the correct settings, which are sometimes hidden especially where configurations are to be achieved. First, the user or the correspondent should start making the settings visible by accessing the menu items Enigmail>>Preferences>>Display expert settings. After this, the user can compose an email and click on the “Write” button. In the same window, pick on the top menu bar item written Enigmail>>Default Composition Options>>Encryption options/Signing. Eventually, accept or click ok after checking the default box of the sign encrypted messages. The following figures show the stepwise configurations that would eliminate any interceptions, which are evident in the letters sent between Babington and Queen Mary.
The next step is very simple. The user or the correspondent will be required to configure signing the outgoing emails. However, the configuration paves for electronic signing of the letters, which brings in a confirmation of legitimacy of the source on the sending end.
Conclusions and Recommendations
History has an interesting version of the instances and events that surrounded the Babington plot. The mission was surrounded by spies and double agents who brought down the conspirators and dismissed the ambitions of Queen Mary in assassinating Queen Elizabeth 1st. Apart from the composition of the mission and key figures; it is worth noting that the key area of concern revolved around information security. Perhaps, Queen Mary’s complacency and the spy network set out by Walsingham largely contributed to her execution. As far as Babington made use of the nomenclature cipher, most of the letters could easily be decrypted or deciphered by Thomas Phelippes, who was also one of the spies in the Walsingham spy network. Frequent interceptions and betrayal by double agents within the transmission path prompted a discussion on establishing safer means of communicating between two intended parties. The exploration of email technology and such technique like Thunderbird led to the recommendable use of safer transmission paths as it is with case of Enigmail on Ubuntu VMs. The discussion has indicated different means through which altered messages can be detected, how interceptions can be avoided and how legit users and correspondents can be confirmed. Therefore, Thunderbird is latest recommendable technology that can achieve safer communication.
References
Pollen, J.H. ed., 1922. Mary queen of Scots and the Babington plot (Vol. 3). T. and A. Constable.
Hutchinson, R., 2007. Elizabeth's spymaster: Francis Walsingham and the secret war that saved England. Macmillan.
Griffin, B., 1997. 'Locrine'and the Babington Plot. Notes and Queries, 44(1), pp.37-41.
Gamble, G.Y., 1991. Power Play: Elizabeth I And" The Misfortunes Of Arthur". Quondam et Futurus, 1(2), pp.59-69.
Evans, M., 2016. ‘By the queen’: Collaborative authorship in scribal correspondence of Queen Elizabeth I. In Women and Epistolary Agency in Early Modern Culture, 1450–1690 (pp. 52-70). Routledge.
Shukla, A.K. and Kumar, A., 2012. Steganography for Invisible Communication: A Review. International Journal of Advanced Research in Computer Science, 3(6).
Fitsanakis, J., 2003. State-sponsored communications interception facilitating illegality. Information Communication & Society, 6(3), pp.404-429.
Riley, K.J., Treverton, G.F., Wilson, J.M. and Davis, L.M., 2005. State and local intelligence in the war on terrorism. Rand Corporation.
Schuster, S., van den Berg, M., Larrucea, X., Slewe, T. and Ide-Kostic, P., 2017. Mass surveillance and technological policy options: improving security of private communications. Computer Standards & Interfaces, 50, pp.76-82.
Mountz, A., 2004. Embodying the nation-state: Canada’s response to human smuggling. Political geography, 23(3), pp.323-345.
Sutherland, E., 2013. Independence and the regulatory state—Telecommunications in Scotland and the rest of the United Kingdom. Telecommunications Policy, 37(11), pp.1046-1059.
Gramm, A., Hornung, M. and Witten, H., 2012, November. Email for you (only?): design and implementation of a context-based learning process on internetworking and cryptography. In Proceedings of the 7th Workshop in Primary and Secondary Computing Education (pp. 116-124). ACM.
Poddebniak, D., Dresen, C., Müller, J., Ising, F., Schinzel, S., Friedberger, S., Somorovsky, J. and Schwenk, J., 2018. Efail: breaking S/MIME and OpenPGP email encryption using Exfiltration channels. In 27th {USENIX} Security Symposium ({USENIX} Security 18) (pp. 549-566).
Ermoshina, K., Musiani, F. and Halpin, H., 2016, September. End-to-end encrypted messaging protocols: An overview. In International Conference on Internet Science (pp. 244-254). Springer, Cham.
Zimmermann, V., Henhapl, B., Gerber, N. and Enzmann, M., 2017. Promoting Secure Email Communication and Authentication. Mensch und Computer 2017-Workshopband.
Kiefer, F., Wiesmaier, A. and Fritz, C., 2012. Practical Security in E-Mail Applications. In Proceedings of the International Conference on Security and Management (SAM) (p. 1). The Steering Committee of The World Congress in Computer Science, Computer Engineering and Applied Computing (WorldComp).
- 24/7 Customer Support
- 100% Customer Satisfaction
- No Privacy Violation
- Quick Services
- Subject Experts



