Introducing VideoOnDemand Service
VideoOnDemand is a new subscription-based service for online video library. There are Three types of users for VideoOnDemand:
1. Standard users;
2. Premium users;
3. Maintainers.
Standard and Premium users are able to log in, renew their subscriptions, search and have access to the standard video library. In addition, Premier users have access to the latest release library. Maintainers are able to log in, add videos, modify user’s subscriptions, search for any type of videos, and read the audit log involving users’ activities. An unregistered individual can obtain access to the system via an automatic procedure involving the payment of the subscription through the DBTI bank: such a procedure can be audited by maintainers.
The external dependencies are presented in Table 1.
1. Decompose the application using data flow diagrams and system architecture diagrams: Every assumption made not grounded in Table 1 must be clearly stated. Failure to do so will incur in a penalty, see Criteria for Assessment;
Answer: The data flow diagram for VideoOnDemand System is given below:

The system architecture diagram for VideoOnDemand system is given below:


Continue your exploration of The Future of Telecommunications with our related content.
2. Determine 3 threats to the system using the STRIDE model and threat trees: they must refer to distinct classes of the STRIDE model. Failure to do so will incur in a penalty, see Criteria for Assessment. Moreover, every assumption made not grounded in Table 1 or in the data flow diagrams or system architecture diagrams must be clearly stated. Failure to do so will incur in a penalty, see Criteria for Assessment.
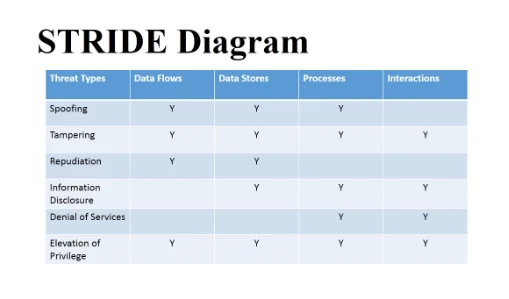
Answer: STRIDE stands for Spoofing, Tampering, Repudiation, Information disclosure, Denial of Service and elevation of privilege. The threats for system by using STRIDE model is given below. Ideally, it helps the users and participants to determine potential problems in application by brainstorming threats classified under six classes.
Spoofing: Spoofing means impersonate the system or violate authentication of system so it is the one important threat which needs to be handled while designing system.
Tampering: Tempering is one of dangerous threat in which data or code is modified by using malicious programs.
Repudiation: Repudiation is an attack in which hacker get entrance into internal part of system hence system is manipulated and spread malicious messages and perform actions.
Information Disclosure: In this threat the important information about system is disclosed by someone. Due to interrupted connection to the server for host or system.
Denial of Services (DoS): When denial of service attack occur then the system is not available for its service.
Elevation of privilege: Elevation of privilege is gain of authorization without given any privilege by admin.
The STRIDE model for VideoOnDemand system is given below:

The threat tree for VideoOnDemand video system is given below:
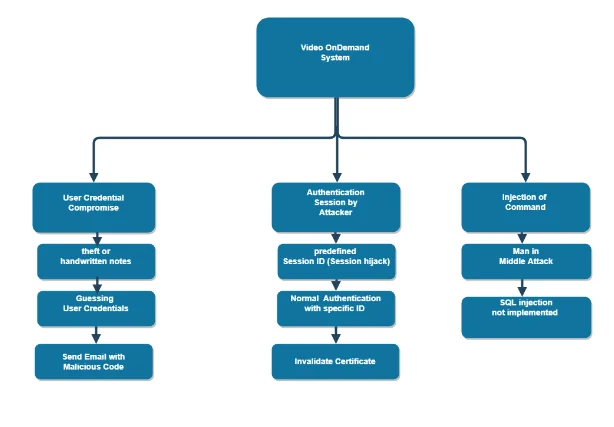
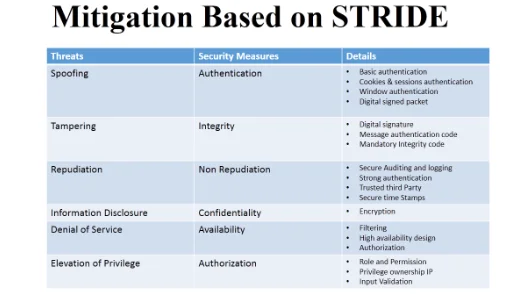
3. Choose techniques to mitigate the threats.
Answer: The mitigate techniques are mentioned in following figure:
- 24/7 Customer Support
- 100% Customer Satisfaction
- No Privacy Violation
- Quick Services
- Subject Experts



