Healthcare Data Breaches: A Growing Threat
Introduction
Many state-of-the-art Electronic Health Record (EHR) systems are unreliable, resulting in compromising patients’ privacy [1] [2]. In 2015 alone, data breaches in healthcare exceeded 112 million records [3]. Many researchers and policy acts have also addressed and emphasized the privacy of patients EHR [4] [5] [6] [3] [7] [1] [8] [9]. In a research [8] illustrate that there is a lack of security in the current EHR frameworks, a lack of privacy for patients, and an unreliable method of transmitting their health data, especially in urgent situations. Developing a safe health data sharing environment has drawn a lot of interest in healthcare sector. The state-of-the-art literature has highlighted newly evolved tactics used to overcome the privacy, security and authentication of electronically stored MHR data [5] [10]. In 2018, a survey by IBM and the Ponemon Institute revealed health information violations as the most expensive among other industries, in an average cost of $380 per record [8]. The same survey mentioned, 25 million of statutory authorizations have been breached in United States for the release of health information per year. In the US between 2013-2017, nearly 85% of medical data over their health information systems has been breached because of multiple hacking attempts. In May 2017, the largest cyberattack impacted the National Health Service (NHS) system in UK and reported 35% of UK hospitals in which 8% of doctors were affected which resulted in an expense of £92 million. Similar to US and UK health systems, many data breaches have been encountered in the MHR system in Australia over the last several years.
Our contributions
In this research, our goal is to implement a centralised privacy-preserving model, named CPMM, which can complement the MHR system. The Health Insurance Portability and Accountability Act (HIPAA) and the Health Information Technology for Economic and Clinical Health (HITECH) have implemented many EHR safety protections in US [6]. The EU General Data Protection Regulation (GDPR) guidelines have been implemented to ensure data protection and subsequent rights to EU citizens [11]. In Australia, thirteen privacy principles have been implemented in relation to the use, disclose and sharing personal information [12]. Despite having local and international privacy policies, the EHR systems have encountered many data breaches which resulted in lack of trust on using existing health record systems. (C1): Centralised privacy-preserving MHR model (CPMM): In this research we will deal with privacy and security issues in the Australian MHR environment. For this, privacy and security models will be introduced and we will build a framework architecture for the centralized privacy-preserving MHR model, named CPMM, so that different healthcare stakeholders can use this as a general standard. The framework will be evaluated on the basis of statistics and case studies through different quantitative and/or qualitative analysis.
Paper Outline
The rest of this article is organized as follows. The research motivation including motivation scenarios are discussed in section 2. The proposed privacy model, implementation of privacy model and evaluation are mentioned in sections 3,4 and 5 respectively. Section 6 contains Related Work, and the Conclusion and Future Research is discussed in section 7. References are mentioned at the end in section 8.
RESEARCH MOTIVATION AND GENERAL REQUIREMENTS
The motivation of this research is twofold. It first plans to analyse the existing Australian MHR system with the help of multiple scenarios [13], hence emphasising the implementation of a CPMM framework to ensure data privacy, which is one of the barriers to people’s acceptance of HER [14]. Then, the associated research challenges have been identified from the analysis of these scenarios.
Motivating scenario
Privacy is one of the core cybersecurity challenges nowadays. Users (as patients) should have control over their health-related data and this data should be maintained by some EHR privacy and security policies at the national and global levels. This must include actions for compensation for those whose data is at risk to breach. By doing this the protection from social or economic discrimination and building trust in the health care system can be achieved. However, it is needed to ensure that critical health data remains accessible at the point of care, and systems must be in place to manage privacy protection. Patients’ control of their own data requires appropriate privacy preserving system which may also help to track who has viewed a record and to whom it has been transmitted to. As per information privacy, it is a patient’s right to be aware of the collected data and the use of their personal (health) data. During hospital/clinics visits it is also needed to inform patients about the reasons for processing their collected data, data holding periods and with whom it will be shared [15]. According to NHS England, the health information has to be centralized at national level. Whenever a GP update patient registration information on his/her own clinical systems, Primary Care Support England (PCSE) uses that information to update the National Health Application and Infrastructure Services (NHAIS) which holds the National Patient Register. But NHAIS is different to GP clinical systems and PCSE cannot see the data on the systems that GPs operate due to privacy concerns [16]. The Royal Australian College of General Practitioners (RACGP) have also created a sample registration for new patients. For ensuring the privacy of health information as required by federal and state privacy laws, the form complies with the RACGP Standards for general practices (5th edition) [17]. If the patients have any privacy concern they may discuss with their GP and leave the form blank. But this is not considered a good practice to let the patient leave the form blank as the information may be required at any phase of their treatment and such missing data may lead to false treatment as well. Another challenge to the EHR and its privacy is the information variability for example data format (text, number, images) and its source(s) (patient, provider, medical device). In case of patient, information may come from clinical applications (studies, sensors, etc.) and may be generated by healthcare providers, or also and increasingly by the patients themselves. Here the primary data is generated when a healthcare provider is in contact with the patient and the input of this data is made in real time by the same provider who is performing this task. The information recorded in the system by persons different from those who performed the activity that generated the information is considered the secondary data. Primary data allows the source (in this case the patient) to be in front of the documenter and therefore, originates from a more accurate source of information. Patients also generate huge amounts of data from their personal devices, which must be taken in account. Hence the EHR systems must be prepared to support this kind of data, organize its storage, and provide an easy way to visualise and aggregate the data with privacy controls.

While dealing with EHR various individuals or groups of people may involve which can be health and non-health stakeholders. Depending on stakeholders’ role in dealing with EHR they can be categorized as broader stakeholders and the general public, engaged stakeholders, decision makers, and key influencers [18].
Government committees are part of the decision-makers group, responsible for vision and strategic direction. Academics and senior executives in health, funding and investment organizations are part of the group of key influencers, advising key decision-makers/Influencers. Healthcare executives (private, public, vendors, industry), health practitioners and professionals, allied health professions, managers and administrators, attorneys, IT and administration staff, insurers, and patients’ associations are engaged stakeholders, because they will be impacted directly by the implementation. Individuals, caregivers, families, and community groups make up the broader stakeholders and general public group, interested in the potential impacts that EHR might have on them.
Data referring to particular individuals must be accurately combined from these various sources, aggregated, and made available (and understandable) for use. We will try to cover some of these stakeholders one by one with respect to their interaction with the electronic health data of patients and the privacy concern.
Scenario 1: Clinic Receptionist
PersonA is a young man who happily got engaged with his colleague and preparing for his wedding after one month. PersonA was diagnosed with diabetes in his adolescence but from last few days he got worried about his vision because of having trouble in reading and writing. He was rather frightened due to this condition because he actually inherited diabetes from maternal side and his grandmother lose her vision due to diabetic retinopathy. He plans to book an appointment in a local health clinic. Due to COVID-19 situation the clinic setup online services for registration prior to visit. PersonA get himself registered by filling in the online registration form which contained a number of fields. Relevant Stakeholders - Receptionist (who will receive the online submitted form first), Patient. Different Levels of Health Information contained in the registration form:
Private health record
Contact Details: Home, Work, Mobile, Email
Any previous illness, allergy, diagnosis
Residential Address: Street, Suburb, Town, State, Postcode, Country
Postal Address: Street, Suburb, Town, State, Postcode, Country
Personal health information record
Name, Family name, Title (Mr, Mrs, Ms, Miss, Prof, Dr etc.), Date of birth, Occupation
Emergency Contact: Name, Phone no., Relationship
Sensitive health information record
Medicare no. and expiry date (if any), Pension/ Health Care Card (HCC) no. and expiry date (if any), Department of Veterans’ Affairs (DVA) no. and expiry date (if any), Student no. and expiry date (if any)
General Practitioner: Name, Phone no., Address, Suburb, Town, State, Postcode, Country
Other types of health record
having private health cover or not, Health Insurance Fund, Membership no., having hospital cover or not, having extras cover or not.
Carer's Contact: Name, Phone no., Relationship
Use-Case Diagram for Receptionist:

Scenario Analysis:
It can be seen from the mentioned scenario that PersonA has some public and some private health information. He wanted to write his fiancée’s name in emergency contact no. but he was concerned about few things:
He did not want his fiancée to get notified about any serious health condition if may occur like diabetic retinopathy. He has a DVA no. due to his father who was a veteran but his mother never let him disclose this thing to anyone due to some personal family matters and legal issues.
Such circumstances require privacy of digital health data. But it cannot be achieved in the current MHR setup where user privileges are unevenly defined, causing vulnerabilities such as potential misuse of data within the organisation by the people who are authenticated, leading to patient’s privacy compromise [19].
Research Challenges:
Based on the APP 6 [12], the personal information only can be disclosed for a specified purposes, for example, for a primary purpose it can be disclosed such as treatment or daily care purpose. The personal health information is also can be disclosed for a secondary if an exception applies. However, this is really a research challenge as the purposes are not clear from the state-of-the-art EHR literature. Same applies for sensitive health information as well. The APP principles are very generic and applicable to any domains. It is quite challenging to identify and apply those generic principles in the health information domain.
Scenario 2: Triage Nurse
PersonB (male) was not on good terms with his father and was arguing with him on phone while driving on the way back home from work. Unfortunately, he had a car accident and got seriously injured. Ambulance took him to hospital in a heavily bleeding and unconscious state, where he was initially taken to the emergency department (ED) for urgent treatment. Triage nurse was the first person to interact with in ED who use to evaluate the data collected during clinical assessment for determining the appropriate urgently required treatment [20]. The nurse found a Medicare card [21] in personB’s pocket which she felt would be helpful during his stay in ED for various details like basic demography, medical bills claims and registration data, payment source, previous medical records like inpatient discharge etc.
Different Levels of Health Information:
Private health record
Medicare card [22]: authenticating beneficiary and provider presence at the point of care, electronically exchanging beneficiary medical information, and electronically conveying beneficiary identity and insurance information to providers
Public health information record
Basic demographics: name, gender, age, blood group
Sensitive health information record
Medical history, observing vital signs, allergy information, pain score, physiological/clinical assessment and disposition.
Any urgent surgery required, lab tests, assessment of the clinical history and physiological assessment
Other types of health record
Medication administration
Athering radiographic and/or pathology investigations, current vascular access, last oral consumption, height, wound screening
Use-Case Diagram for Nurse:

Scenario Analysis:
In the above scenario there may arise various contradictions. PersonB was unconscious and did not had any medical identity number neither enrolled in health record system (i.e. MHR), which initially leads to difficulty in patient handling.
From the data retrieved by medicare card the nurse was able to see personB’s previous visits to any healthcare. This helped the nurse in taking few decisions in treatment. Due to excessive blood loss, it was urgently required to have blood transfusion. A person known to personB was also called from the last call record made from his mobile phone which was of his father. His father, after reaching ED was informed about personB’s details accessed from his medicare card. In addition, he was also told about Acquired Immunodeficiency syndrome (AIDS) being just identified by his son’s laboratory reports.
Research Challenges:
Well, the information about medicare logs and some private health identifications needed to be passed on with personB’s consent, like to whom it should be disclosed. Therefore, when personB regained consciousness, he was shocked to see his father which let him into another trauma. The nurse also referred personB to a medicare registered neurosurgeon for a detailed examination of his head injury. But he denied to go to that surgeon and get angry at the nurse for taking account of this action. Hereby, according to article5-1f [11] the accessed data must be processed in a manner that ensures appropriate security of the personal data, including protection against unauthorised or unlawful processing and against accidental loss, destruction or damage, using appropriate technical or organisational measures. As per principle6.1a [12], the personal data would only be shared/accessed if the individual has consented to the use or disclosure of the information.
Scenario 3: GP / Doctor
PersonC is an eighty-five years old woman whose husband died twenty years ago. She lives with her son who have three children. PersonC is deeply attached with her grandchildren, and she considered them the only charm of her life. Due to the sudden death of her youngest grandson which occurred right in front of her because of food choking, she gets so depressed. She started declining both physically and mentally but feel reluctant to discuss this with her son. PersonC also started behaving in a strange manner like being paranoid or delusional. This thing became worrisome for her son too, who is her only caretaker. Therefore, he takes personC to a doctor and the doctor referred personC to a psychologist or psychiatrist after detailed examination.
Different Levels of Health Information:
Private health record
Any previous illness, allergy, diagnosis
Personal health information record
Name, Date of birth, Occupation
Sensitive health information record
Medical history, observing vital signs, allergy information, pain score, physiological/clinical assessment and disposition, physical examination
Other types of health record
Referred to a specialist (psychologist or psychiatrist)
History of recent visits to health providers
Carer's Contact: Name, Phone no., Relationship
Use-Case Diagram for GP / Doctor:

Scenario Analysis:
In the given scenario there are multiple concerns of patient data. Foremost is the mental health issue which may or may not be disclosed with the family (son). People at this age also become reluctant to disclose their data especially when it is required multiple times. Afterwards the 85 years old personC must be aware of the data collection and its processing for various purposes, for example, specialist, laboratories etc.
Research Challenges:
It is mentioned in article30-4 [11] that the record can be made available to the supervisory authority on request. But article32-1a [11] and principle2 [12] emphasis on the pseudonymisation and encryption of personal data. Further consent must be taken by personC because its written in artice7-1 [11] that the controller shall be able to demonstrate that the data subject has consented to processing of his or her personal data.
Scenario 4: Referred doctor / Specialist
PersonC (from the Scenario 3) was taken to the specialist doctor who was an experienced psychologist. The specialist did not belong to the same clinic as of the GP. Therefore, the son was worried about the whole previous visits and health record of his mother PersonC, that is, personal data, previous examination details and lab tests reports.
Levels of Health Information:
Private health record
Previous illness, allergy, diagnosis
Personal health information record
Name, date of birth, occupation
Sensitive health information record
Medical history, observing vital signs, allergy information, pain score, physiological/clinical assessment and disposition, physical examination
Diagnostic tests (X-rays, blood tests)
Any urgent surgery required, lab tests, assessment of the clinical history and physiological assessment
Other types of health record
Referred to a psychologist or psychiatrist
History of recent visits to health providers
Review of test results by specialist in different systems such as hospital EHR, on an outreach portal system, in an in-office EHR, on a mobile device, or on a hard copy via mail or fax, each of which carries its own set of cautions and idiosyncrasies
Use-Case Diagram for Specialist doctor:

Scenario Analysis:
The data transmission from one healthcare body to other is a commonly observed task specially after the advent of electronic data. But in some cases, the patients may have different point of views. Such as, providing the same data again at one hand and on the other hand if the data is accessed from any previous resource (i.e. doctor/GP) then they might become concerned about why their data is accessed from the other sources [23]. Therefore, all such matter has to be very keenly considered in the light of rules and regulations.
Research Challenges:
As per guidelines of [11] article7-3, the data subject shall have the right to withdraw his or her consent at any time. In this scenario the personC does not want to use the same previous consent form of revealing her tests reports and other sensitive health issues to the son. Moreover, according to principle5.2 [12] personC must be aware of sharing her data to other prior.
Scenario 5: Radiologist
PersonC (from the Scenario 3) was advised to undergo some blood tests and x-rays from the specialist doctor. The son took personC to the pathology unit of the specialist doctor’s clinic for the tests. These continuous activities of visiting doctors and fulfilling their requirements of specialists visit and laboratory tests made personC anxious and distressed.
Different Levels of Health Information:
Private health record
Unique patient identifier
Contact Details: Home, Work, Mobile, Email
Residential Address: Street, Suburb, Town, State, Postcode, Country
Personal health information record
Name, Family name, Title (Mr, Mrs, Ms, Miss, Prof, Dr etc.)
Emergency Contact: Name, Phone no., Relationship
Sensitive health information record
Medicare no. and expiry date (if any), Pension/ Health Care Card (HCC) no. and expiry date (if any), Department of Veterans’ Affairs (DVA) no. and expiry date (if any)
Tests result transmission,
Other types of health record
Doctor’s name by whom tests are advised by
Test order name, that is, STST, ASAP, routine, timed, Standing or recurring, future
Elements of test repost (Reference ranges (normal ranges), Abnormal flags, Units of measure, Explanatory footnotes or comments, Name and address of performing laboratory, Corrected, amended, and addended reports)
Use-Case Diagram for Laboratories / Medical Imaging Facilities:

Scenario Analysis:
If the laboratory / imaging facility coordinates with the same health unit, then the data would be shared automatically. Somehow the outside laboratories / imaging facilities are also linked to various health units or clinics and get the patients data from there. This could be for the smooth functioning of the system but at some points this thing results into serious matter in case of privacy specially when it comes to some medical reports results.
Research Challenges:
According to [11] article13-2a, one of the key challenges here is to know the time period for which personal data will be stored, or if that is not possible, the criteria used to determine that period. As personC is concerned about this data keeping. Therefore, according to article13-1 and article 30-1b [11] personC should be notified about the purposes for which the collected data will be processed. In the principle6.1a [12], the information may only be forwarded if the individual has consented to the use or disclosure of the information.
Scenario 6: Patient – Pharmacist
PersonD has just become father for the first time after seven years of marriage. His wife has undergone a caesarean section with lot of complications like excessive bleeding, severe stomach pain and high-grade fever. PersonD’s newborn also have some breathing difficulty and therefore placed into incubators for continuous monitoring. These things drive personD into depression. When his wife was discharged from the hospital, he was given a list of prescribed medicines. After two days of discharge from the hospital his wife notices some body rashes which she thinks is possibly because of the medicines she is taking. PersonD then goes to the pharmacy to discuss about the medicine.
Different Levels of Health Information:
Personal health information record
Name, family name, age, weight
Sensitive health information record
Past medical history
Any other allergies
Current medical and physical condition
Other types of health record
Doctor’s name by whom medicines are advised by
Chemical constitutions of taken medicines and dose
Travel distance from hospital to home
Scenario Analysis:
Because of the current situation of his wife and the newborn, personD is already depressed and not in a mood to talk much. But at pharmacy personD was told by the pharmacist that he will take him to a private discussion room where he can discuss the whole matter. The pharmacist further added that everything they discuss will be private and confidential. PerosnD was confused why pharmacist is enquiring the details (mentioned above) like a doctor. But it is necessary to investigate all this to check whether the reaction/ body allergy is due to the medication constitutions or other previous allergies/condition of the patient. Moreover, when the pharmacist refers personD to see the doctor for his wife recent allergy condition. PersonD become more afraid of visiting the doctor again and lose confidence on the pharmacist that why he is not suggesting the alternate medicine.
Research Challenges:
PersonD is upset and not in a state of mind to share his wife’s severe health situation in detail with anyone other than the doctor due to the severity of the case and privacy. But pharmacists is already familiar with the obligation of maintaining the confidentiality of patient data [24]. According to GDPR, pharmacists are at a risk of severe penalties for non-compliance [11]. The regulation provides data must not be kept for longer than necessary for the specified purpose. Further processing sensitive personal data is also prohibited unless personD has given explicit consent.
Use case Scenario 7: Researcher
PersonE is a 46 years old woman and undergone radiotherapy on the left side due to breast tumour. She has an uncontrolled blood pressure of 138/79 mmHg. She is concerned about her health because of the family history because her mother also died of brain haemorrhage. She asked her GP about how many people have such histories on average or if such relevant cases have been recorded in the National Health Services. The GP think about this and talk to the research team about such clinical trials if they have been recorded before.
Different Levels of Health Information:
Personal health information record
Name, family name, age, weight
Sensitive health information record
Blood pressure
Past medical history
Previous surgery
Other types of health record
Family health history
Current medications prescribed by doctor
Research oriented data/document record
Laws, regulations and privacy policies
Scenario Analysis:
According to the Australian Bureau of Statistics (ABS) [25], 2017-18 National Health Survey (NHS) show that 1 out of 5 women have uncontrolled high blood pressure. The personE’s concern about her current condition and family history make her think about other people with same conditions. The GP involve the research team to talk about clinical guidelines for such cases. When personE is involved in the research, she is required to share her personal and private data and as well as the family background and medical histories. PersonE is also required to know the ethical and policy guideline while involving in clinical research.
Research Challenges:
Whenever a person/patient is involved in any research, there need to be a prior consent to avoid any later dispute. World Health Organization (WHO) has developed a formal written consent form to be filled by the involved research participants [26]. In the patient-researcher scenario, personE is asked multiple questions (mentioned above), but she need to be aware of; where this data will be stored and for which purpose her data will be utilized that is; investigations, ordered informatics, disease management programme, and for comparisons with other patients’ data. According to the article 3(2) of the Clinical Trials Directive 2001/20/EU [11], personE feels reluctant to get her personal data stored for later studies and the article 6 [11] also mentions that a lawful basis must be established before processing the personal data. One more point of following the EUGDPR and the personE data privacy is the flow of data and the consent. This is because EUGDPR facilitate the free flow of personal data; but on the contrary, it also makes it subject to conformity with legal requirements of the right to privacy and the right to the protection of personal data of individuals [27]. Hence, these are generic guideline for dealing with data. But the question to transfer of data to any other source later on is still there, hence leaving some gates opened to the complete privacy of personE’s personal data.
Conceptual Privacy Model
This section introduces the proposed privacy model. Figure 2 shows the necessary steps to define the privacy model, following a bottom-up approach. From the model, the first step is analysing the healthcare scenarios to get the core variables, issues, patient’s health conditions, problems identification, and mapping steps that need to be taken. This step is essential in strategic decision making and planning [28]. Depending on the scenario, the stakeholders in step 2 include physicians (GP, nurses), vendors (pharmacists), patients, caregivers, financiers (insurance companies), medical leaders, and laboratory and researcher teams. The decision on which stakeholder to be involved should exclusively scenario-based. These is done to reduce risk associated with data handling, negligence, and safety [29]. The subsequent steps (step 3 and 4) outlines MHR data identification and classification the followed by identifying, designing, and validating privacy requirement and ontology. Principally, the guide into maintaining confidentiality, privacy, and ensuring preparedness to external system breach is based on systematic and logical process [30].

Identifying and Categorising Stakeholders from Healthcare Scenarios
We already covered MHR scenarios earlier, that included doctor, nurse, receptionist and so on. Based on the identified healthcare scenarios, we have different types of stakeholders which are as follows:
Roles: Stakeholders
Senior Roles: 5 types (scope of our research)
Junior Roles: under those 5 types of senior roles, we categorise relevant junior roles.

Using mathematical Set Theory;
Roles = {Primary Stakeholders, Secondary Stakeholders}
Roles = {Senior Roles, Junior Roles}
Senior Roles = {Primary & Secondary}
Junior Roles = {Primary & Secondary}
Mutually Inclusive and/or Mutually Exclusive
The following combinations are derived
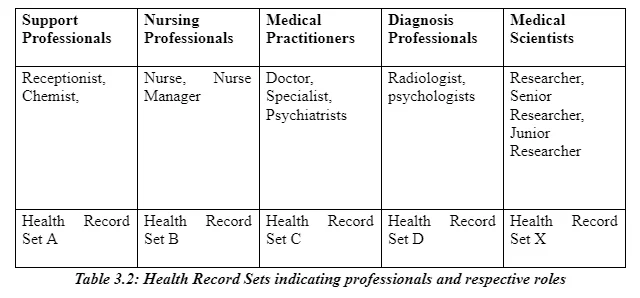
Support Professionals (SProfessionals) = {Receptionist (SRec), Chemist (SChe)}
Nursing Professionals (NProfessionals) = {Nurse Manager (NNM), Nurse (NN)}
Medical Practitioners (MPractitioners)= {Doctor / GP (MD), and Specialist Doctor (MSD)}
Medical Scientists (MScientists) = {Senior Researcher (MSR), and Junior Researcher (MJR}
Where, Chemist and Receptionist are the elements of support professionals. Similar for nurse manager and nurse being under nursing professionals. The diagnosis professionals can either be mutual inclusive or exclusive where a patient can be referred to radiologist, psychologist or both. Depending on a health care scenario, more than one set can intersect or form a union. For instance, Scenario 4 where a patient is referred to a psychologist (DProfessionals) has more than 1 set: MPractitioners and DProfessionals
Therefore,
MPractitioners ∪ DProfessionals = {x : (x ∈ MPractitioners) ∨ (x ∈ DProfessionals )}
Similarly, in a scenario where a patient meets with a receptionist the proceed to discuss their health with a nurse, the intersection set would incorporate individuals not exclusively but who interacted with the patient.
SProfessionals ∩ MPractitioners = {x : (x ∈ SProfessionals) and (x ∈ MPractitioners)}
Classifying MHR Data
Analysing all the MHR scenarios, we identify the following types of health information:
Sensitive health information
Historical health information
Define different types of health information, following the standards, e.g., APP, GDPR…
Health information comprises the patients’ personal information (name, age, gender, and income), medical history, diagnoses, symptoms, procedures, and laboratory report. A health report includes records that include demographic information, laboratory results, clinical notes, reception notes, and health history. Personal information is identifier allowing a patient to be identified, contacted, or located. According to GDPR article 4, the personal information relate to identifying a person whether directly or indirectly that include name, address, date of birth, contact information (phone number, house address, and employers contact number) email address, social security number, biometric IDs, and any other individual identifying characteristics [11]. Sensitive information, on the other hand, captures those that require safeguarding for security and privacy of the patient. Such information as sexuality, political opinions, cultural views, racial background, and religious beliefs carries highest risks in case of disclosure. Under GDPR, sensitive data encompasses information that require additional protection due to possibility of discrimination and violation of fundamental rights if it falls into wrong hands [11]. Patients with mental status and AIDs may want such information kept confidential. The information is deemed private. The Privacy Act protects interests of the patients including confidentiality and personal information [12]. Whereas, historical information captures record about a patient health including illnesses, surgeries, tests, laboratory exams, medications taken, and family health history. Using Mathematical Set Theory, the following defines the elements of sets. For instance, Set A has element ‘personal health information’
Health Record Set A = {Personal health information}
Health Record Set B = {Personal health information, Private health information}
Health Record Set C = {Personal health information, Sensitive health information, Private health information, Historical health information}
Health Record Set X = {Health Record A, Health Record B, Health Record C, Health Record D}
An intersection of Sets A and B
Health Record Set A ∩ Health Record Set B = {x : (x ∈ Personal health information) ∧ (x ∈ Personal health information, Private health information )}
Health Record Set A ∩ Health Record Set B = {Personal health information}
While union of the Sets B and C, we have;
Set B ∪ Set C = {x : (x ∈ Set B) ∨ (x ∈ Set C )}
= {Personal health information, Sensitive health information, Private health information, Historical health information}
Identify Privacy Policies
Based on the stakeholders and different type of health information, we identify the following privacy policies:

Implementation of Privacy Ontology
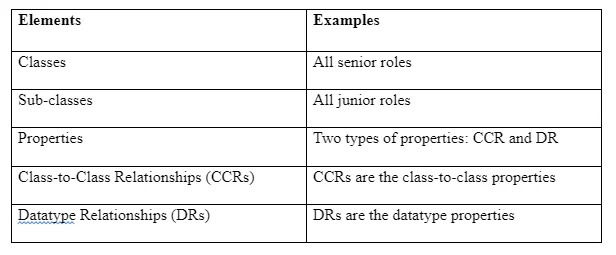
We use Protégé OWL 5.5 tool to build the privacy ontology. Web Ontology Language (OWL) is an object-oriented concept defining ontologies in terms of classes, properties, and characteristics of the objects. The approach will be use represent the health records in a simplified object oriented manner that include classes, sub-classes, and properties. Classes (S): Senior Roles Sub-Classes (SC): Junior Roles Properties: two types of properties; CCR and DR Class-to-Class relationships (CCR): has, is-a (sub-class-of), Datatype relationships (DR): classID

Our privacy ontology has three major parts: Role ontology, Health record ontology, and Privacy policy ontology.
Classes, Sub-classes and Properties Related to Stakeholders
The privacy Ontology has the following key elements which are shown in the Table 4.2.
Classes
Based on the scope of this researcher privacy ontology has 5 key classes:
Support Professionals Nursing Professionals Medical Practitioners Diagnosis Professionals Medical Scientists
This ontology is set limited to five classes. Other necessary classes can be incorporated as well.
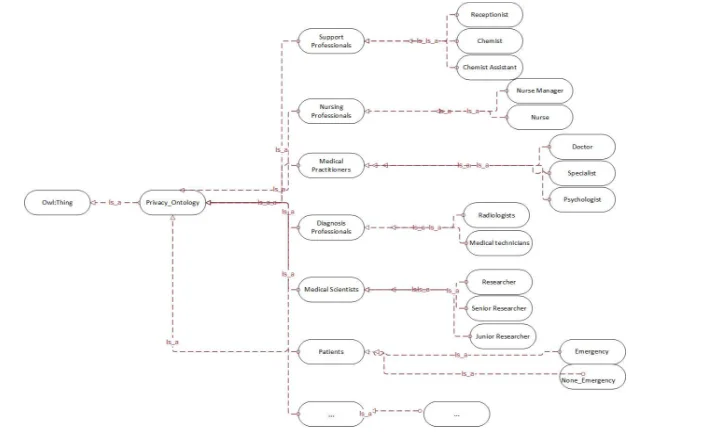
Sub-Classes
The classes support Professionals has the 2 Sub-key Classes

Stakeholders

Primary Stakeholders
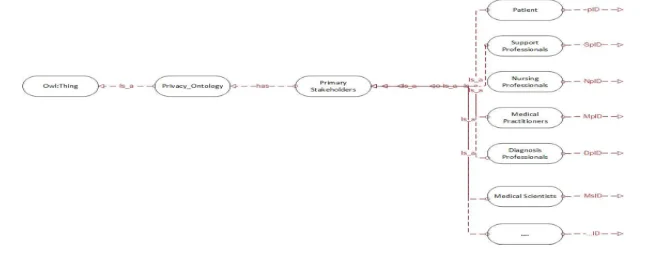
Secondary Stakeholders
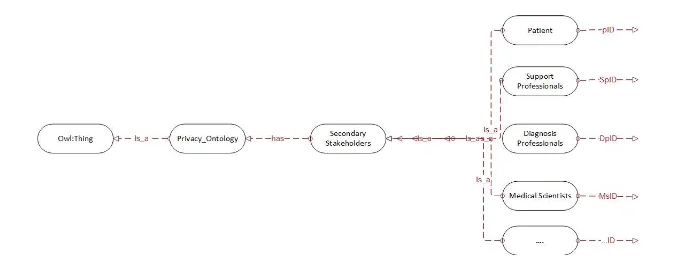
Properties
The properties have the relationships between the properties such as:
Class-to-Class Relationships (CCRs)
Datatype Relationships (DRs)

Classes, Sub-Classes and Properties Related to Health Information

For example:
Personal Health Information: Primary address will only release: Lysterfield. However, Patients actual address is: 5 Somewhere Street Lysterfield 3156. All primary stakeholders can have access/see of patients Personal Health Information, however they do not have access of Private Health Information. For any emergency, some of primary stakeholders can access patients Private Health Information. For example, where patient have considered to be in a very critical condition and is in need to admit to hospital, medical practitioner should have access of patients exact home address for emergency treatments.
Privacy Policies/Rules
Based on the DL (description logic) and/or SWRL (semantic web rule language) rules, the decidability on patient’s data access is guided by sound and tractable reasoning [31]. The data access is classified based on policy. Primary policy 1: as shown in Figure 15, all medical professional can access patients Health Information based on policy 1 and policy 2. Primary policy 2: as shown in Figure 15, all support professional can only access patients Health Information based on policy 2.
DL (description logic) and/or SWRL (semantic web rule language)


Evaluation of Privacy Ontology
We evaluate some PR rules using three procedures, namely;
Java or Python (performance)
Ontology performance is evaluated using dynamic object model, a high level Python module manipulating classes and performing closed world reasoning.
Ontology correctness
The mechanism checks the attainment of the intended semantics. In this case, the correctness captures the relationship between the ontology structure and its axiomatization model [32].
Ontology extensibility
To preserve the ontology metadata and privacy standardisation, it is essential to have representation and integration upheld for future expansion. The ontology will not be limited to the sub-classes outlined but have capability of accommodating elements
Related Work
Personally Controlled Electronic Health Record (PCEHR) System
The proposed approach uses fully homomorphic encryption (FHE) to encrypt patient’s data. The decryption key is held by the patient therefore no other person can access the data without his/her authorisation [32]. In attempt to advance the reliability and privacy, the approach uses verification technique such as cryptographic ensuring only authorised person can access corresponding records [33]. However, the challenge with this approach is when a patient is admitted in unconscious state (Scenario 2).
Privacy by Smart Contracts- Healthcare Blockchain System
Several scholars have propose using Blockchain technology in enhance accuracy, security, and privacy preservation [34] [35] [36] [37]. The Blockchain-based data preservation systems ensure reliability in access and retrieval of the data through primitiveness and verifiability framework. However, being relatively new technology, challenges such as cultural shift, several open access nodes, implementation of a distributed system, and having a centralised system have been reported [38] [39] [40]. Research has explored such approaches as MedRec, MediBloc, OmniPHR, and MedVault, which are Blockchain-based. MedRec [41] is a blockchain-based decentralized record management system to handle EHRs. MediBloc [42] also has the performance, scalability and energy consumption issues. Our model also uses the meta-data, however, the operations are different. OmniPHR [43] uses blockchain idea (linking the blocks) to store data which is broken into small pieces as blocks. The system only emphasized on interoperability, limited storage and scalability issues. In the UK, customised hybrid blockchain solutions have started to gain interest by healthcare organisations who have had significant issues with established EHR vendors. Some open projects including openEHR and FHIR also aim to facilitate the generation of openly adopted EHR standards and protocols to facilitate data exchange between vendors [1].
Conclusion and Future Research
This research proposes a secure data sharing framework for Australian MHR system. Using this framework, the different healthcare stakeholders can communicate with each other and share their personal and sensitive information. In order to build the framework, we first explore the research challenges with a literature review to identify existing research gaps. We then present different motivating scenarios from healthcare sector, analyse them and finally identify the associated research issues. The privacy and security policies will be modelled and implemented for the Australian MHR environment. Following the privacy and security policies, we will build and evaluate the framework through different case studies and quantitative/qualitative analysis. We finally highlight several research directions for future scholars to improve this framework further. For the future works, key area is investigating the efficacy of the model in line with handling patients’ privacy and confidentiality. The intercommunication and coordination among various stakeholders might be a challenge particularly in an industry traditionally slow in technology uptake. Hence, a recommendation of ways in improving the framework to accommodate this will be made.
References
D. Akarcac, P. Xiu, B. Ebbitt, B. Mustafa, A. Al-Ramadhani and A. Albeyatti, “Blockchain Secured Electronic Health Records: Patient Rights, Privacy and Cybersecurity,” 2019 10th International Conference on Dependable Systems, Services and Technologies (DESSERT), pp. 108-111, June 2019.
A. H. Omar, “The Effect of Electronic Health Records on Undergraduate and Postgraduate Medical Education: A Scoping Review,” Doctoral Dissertation University of Toronto , Canada, 2019.
N. Kshetri, “Blockchain's roles in strengthening cybersecurity and protecting privacy,” Telecommunication Policy, vol. 41, no. 10, pp. 1027-1038, 2017.
F. Rezaeibagha and Y. Mu, “Distributed clinical data sharing via dynamic access-control policy transformatio,” International Journal of Medical Engineering and Informatics, vol. 89, no. 4, pp. 25-31, 2016.
H. Wang and Y. Song, “Secure Cloud-Based EHR System Using Attribute-Based Cryptosystem and Blockchain,” Journal of Medical Systems, vol. 42, no. 8, 2018.
C. S. Krus, B. Smith, H. Vanderlinden and A. Nealand, “Security Techniques for the Electronic Health Records,” Journal of Medical Systems, vol. 41, no. 8, pp. 1-9, 2017.
M. Farhadi, H. Haddad and H. Shahriar, “Static Analysis of HIPPA Security Requirements in Electronic Health Record Applications,” 2018 IEEE 42nd Annual Computer Software and Applications Conference (COMPSAC), pp. 474-479, 2018.
G. G. Dagher, J. Mohler, M. Milojkovic and P. B. Marella, “Ancile: Privacy-preserving framework for access control and interoperability of electronic health records using blockchain technology,” Sustainable cities and society, vol. 39, pp. 283-297, 2018.
THE EUROPEAN PARLIAMENT AND THE COUNCIL OF THE EUROPEAN UNION, “Regulation EU 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free,” Official Journal of the European Union., April 2016.
A. S. Kayes, W. Rahayu, T. Dillon, E. Chang and J. Han, “Context-aware access control with imprecise context characterization for cloud-based data resources,” Future Generation Computer Systems, vol. 93, pp. 237-255, 2019.
A. Spencer and S. Patel, “Applying the data protection act 2018 and general data protection regulation principles in healthcare settings,” Nursing Management, vol. 26, no. 1, 2019.
P. Vimalachandran, Y. Zhang, J. Cao, L. Sun and J. Yong, “Preserving Data Privacy and Security in Australian My Health Record System: A Quality Health Care Implication,” in International Conference on Web Information Systems Engineering, Springer, Cham, 2018.
W. Varndell, A. Hodge and M. Fry, “Triage in Australian emergency departments: Results of a New South Wales survey,” Australian Energency Care, vol. 22, no. 2, pp. 81-86, 2019.
M. L. Wilkerson, W. H. Henricks, W. J. Castellani and M. S. S. J. H. Whitsitt, “Management of Laboratory Data and Information Exchange in the Electronic Health Record,” Archives of Pathology and Laboratory Medicine, vol. 139, no. 3, pp. 319-327, 2015.
H. C. Vollmar, T. Ostermann and M. Redaelli, “Using the scenario method in the context of health and health care – a scoping review,” BMC Med Res Methodol, vol. 15, no. 1, pp. 1-10, 2015.
M. A. Sujan, I. Habli, T. P. Kelly, A. Guhnemann, S. Pozzi and C. W. Johnson , “How can health care organisations make and justify decisions about risk reduction? Lessons from a cross-industry review and a health care stakeholder consensus development process,” Reliability Engineering & System Safety , vol. 161, pp. 1-11, 2017.
Q. Mamun, “A conceptual framework of personally controlled electronic health record (pcehr) system to enhance security and privacy.,” in International Conference on Applications and Techniques in Cyber Security and Intelligence, Cham, 2017.
A. Zhang and X. Lin, “Towards Secure and Privacy-Preserving Data Sharing in e-Health Systems via Consortium Blockchain,” Journal of Medical Systems , vol. 42, no. 8, pp. 1-18, 2018.
T.-T. Kuo and O.-M. L. Kim Hyeon-Eui, “Blockchain distributed ledger technologies for biomedical and health care applications,” Journal of the American Medical Informatics Association, vol. 24, no. 6, pp. 1211-1220, 2017.
C. Esposito, A. De Santis, G. Tortora, H. Chang and K.-K. R. Choo, “Blockchain: A Panacea for Healthcare Cloud-Based Data Security and Privacy?,” IEEE Cloud Computing , vol. 5, no. 5, pp. 31-37, 2018.
K. Fan, S. Wang, Y. Ren, H. Li and Y. Yang, “MedBlock: Efficient and Secure Medical Data Sharing Via Blockchain,” Journal of Medical Systems , vol. 42, no. 8, pp. 1-11, 2018.
Y. Ji, J. Zhang, J. Y. C. Ma and X. Yao, “BMPLS: Blockchain-Based Multi-level Privacy-Preserving Location Sharing Scheme for Telecare Medical Information Systems,” Journal of Medical Systems , vol. 42, no. 8, pp. 1-13, 2018.
- 24/7 Customer Support
- 100% Customer Satisfaction
- No Privacy Violation
- Quick Services
- Subject Experts



