Enhance Security Against Escalating Threats on Web Applications
Literature Review
The threat on web applications has escalated and comprises 60% of the overall attacks on web apps, with 60% of all attacks being carried out in the web applications being the most insecure feature of the internet. (Babiker, Karaarslan, and Hoscan, 2018). It is mandatory and appropriate for web applications to implement sweet pots on all networks to devise counter-measures and to provide security against Cross-Site Scripting, SQL injection, Local File Inclusion, etc. Many portals are used in the industry that provides smooth online customer support to consumers. According to the "Communication Pattern Report," companies focused on the use of social interaction and web apps could exponentially develop. Companies around the world use Secure Sockets Layers (SSL), Firewalls, and other networking systems to defend themselves from attacks. According to the information (IPA), 75% of attacks on the web application occur from the Information Technology Promotion Agency. However, these steps are much of the time not sufficient to guard against cyber threats (Jia et al., 2018). The researchers have established many methods to improve the protection of Web applications through input and output validation. Online apps with different flaws, depending on time. Consequently, each year and then, insecurity varies more and more than the previous year. If you need data analysis dissertation help, these strategies can help bolster your approach to cybersecurity.

Recent security trend in a web application perspective
According to the PTsecurity report, high-risk vulnerabilities decreased substantially last year, 2019. In contrast to 2018, the decline can be as high as 17 percent.
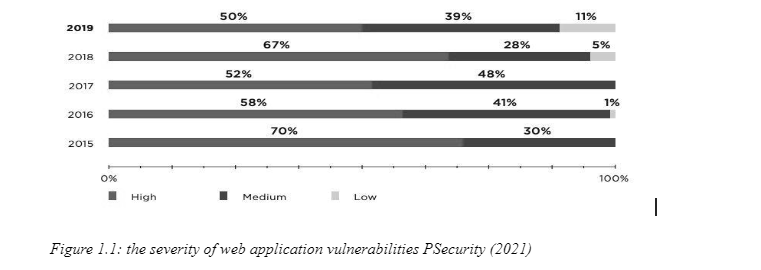
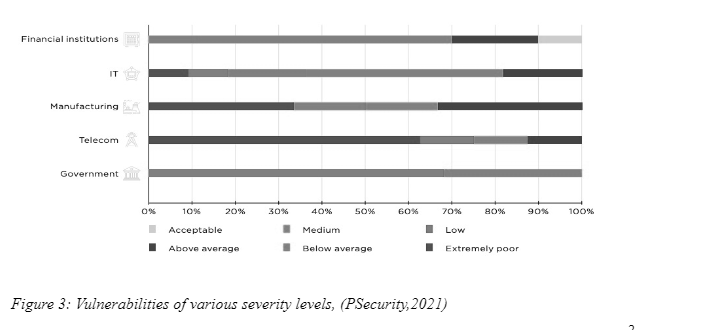
Understanding of vulnerabilities in the different organization:
In different markets, the gap in security risks continues. The PSecurity (2021) study found that the networks of the network and the government are likely to be targeted and more vulnerable. As described below, in various industries only financial institutions have an adequate standard of protection.
PSecurity (2021) reported that security setup is a thousand times the most common web application limitation in 2019. One in five apps has found bugs that cause attackers to target the user's session and in the meantime, the attackers impersonate the program. The attackers perform the process, including Cross-Site Scripting (XSS), to capture the specified user session. 45% of mobile apps find that the PSecurity (2021) study found issues with broken authentication. The organizational fault is responsible for one-third of these vulnerabilities. The attacker can take advantage of passwords and use brute-force attacks to enter the web application (Huang et al., 2019). For instance, a brute force attack is also known as a dictionary attack that allows an attacker to search the username or password of the dictionary and one program may have access to administrator privileges after 100 attempts (Danchenko et al., 2017). The 'password only' authentication is one of the most important considerations in the web application. The complexity and password requirements were considered to be unbreakable, but are now ready to be ruptured. If NIST has not already started its security protocols, companies should move from a 'password only' system to a multifactor authentication system. In 2019, Broken Access Control was observed in one of three applications (Wafi et al., 2017).
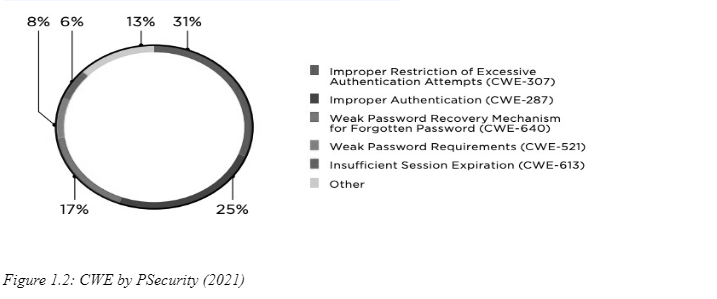
Theoretically, bypassing usability constraints may lead to the release of sensitive data or kill data (2020). One program was allowed to change the user profile and to cause inconvenience to the assailant. Positive Technologies experts proposed that an email address would alter the username of the administrator and that it would be possible to substitute the address at will. The regular password is then used to be reset so the user privileges can be accessed. SSDLC may be used to reduce the flaws in permitting web application creation by minimizing the use of the Secure Software Development Life Cycle. SSDLC may be used to reduce the flaws in permitting web application creation by minimizing the use of the Secure Software Development Life Cycle (Ng et al., 2018).
Different Web application vulnerabilities:
OWASP 2021, aside from the top 10 bugs in 2017, has found weaknesses. Another root of the attacker's weapon, clickjacking, is a vulnerability to the web application. Another vulnerability to the web application is the Cross-Site Request Forgery (CSRF). The intruder cleverly manipulates the user's mess scripts by acting as a user (Baykara, and Das, 2018; Hamada et al., 2018). When an individual logs on to a CSRF website, the user receives a phishing message containing a connection to a website. When the attacker clicks on this page, the user is asked for the website according to the wishes of the attacker. The user would not be able to differentiate between positive links and bad links with a phishing message or malware connection. If the user has no CSRF protection, the user would be vulnerable (Vetterl, and Clayton, 2018). CSRF tokens (one-time key), authentication prerequisite (multifactor password) and the request proceed from the source are part of the security the user can take (confirmation with CAPTCHA). In the event of an attack, the victim appears to click on a particular ad where the click connects to the attacker's location. The malefactor is put on that particular icon, for instance, a transparent HTML frame, iframe. When you press the mouse, the user leads him/her to a vulnerable site where 'likes' can be requested in photographs or videos. This phenomenon is quite depriving and can be avoided if X-Frame-Options are available To alleviate the problem effectively, use the HTTP header (Baykara and Das, 2018). In addition to the list of OWASP top ten vulnerabilities, there are more below:

PSecurity (2021) has always been the challenge to web apps in 2019, including threats on customers. Cross-Site Scripting (XSS) is one of the main influences in this regard. Attackers can conduct various malicious activities such as infecting ransomware on machines, phishing so that authentic users can use their accounts, serve as the primary user, and so on. The dangerous characters which can be conveniently used in the formatting of the page are recommended for removal. Modified web browser firewalls are also advised as they will block all cross-site scripting. Research shows that 78% of the attacks are on the collection and processing of personal data (Vetterl, and Clayton, 2019).
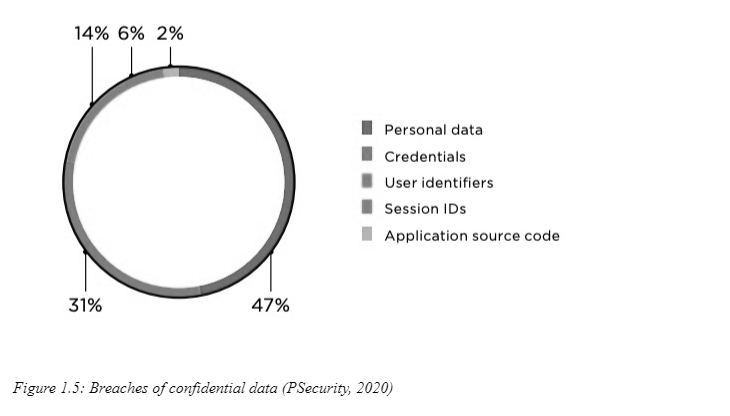
47% of all violations of the personal data are being searched, while the user data is not that far behind 31%. The hackers concentrate on users' knowledge. A research study found that 16 percent of all online apps have serious bugs, enabling them to monitor the operating environment of the website and the program. For instance, accessibility to the web application may be used to include a JavaScript sniffer in code. The sniffers will rob personal and credentials material (Yamin et al., 2019). In addition, card details can also be collected by the sniffers. In 2018-2019, sniffers from JavaScript are considered one of the vicious people attacks. When a hacker targets an organization, web-based applications may acquire data from the server, such as ports, network segments, and services. If the hacker is highly skilled, he or she can reach and provide sensitive information about the internal network of the organization (Negi et al., 2020).
Web apps are not very sophisticated in terms of encryption. Half of all mobile app pages have high-risk vulnerabilities. Nevertheless, since last year, the proportion of highly vulnerable individuals has declined. One-third of all vulnerabilities occurred in 2018, which decreased in 2019. Furthermore, online apps are now more conservative by firms. The architectural honeypot with a low interaction system was seen in the production system both by (Dahiya, and Srivastava, 2018) and various researchers. "Honeyd-WEB" is the name for the delicious pot. The honeypot's characteristics can include lightweight to provide intensive safety. In addition, it means that contact with the hacker is even less possible. Contrary to certain other applications, there is no risk of a honeypot being insecure and in the end, compromised. In addition, the honeypot can also be used for user interface management. The simulation of the HTTP server is one of the features of the "honeyd-web." The web server that is insecure in the network can also be imitated. In this diagram, for instance, Microsoft IIS 5.0 could be imitated as a web server with a danger. The web framework for honeypot is considered to be one of the low-level (Guarnizo et al., 2017).
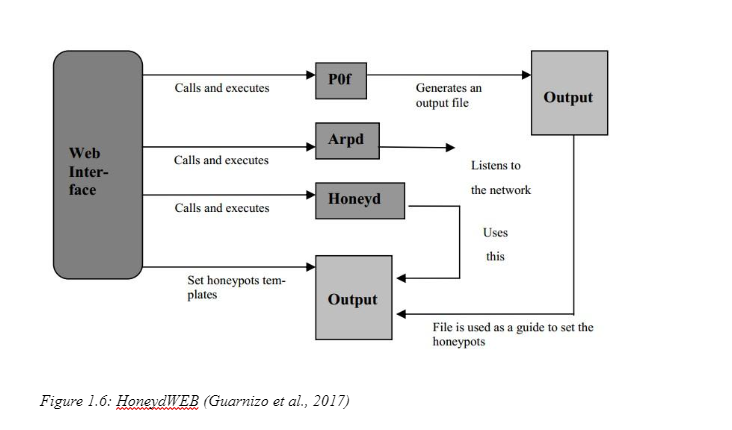
The GUI on the site is regarded as the honeypot's main feature. The P0F tool allows information to be collected on networks that will install all honeypots in the production network structure. In the meantime, the arpd will be called via the web interface and IP address assignment, along with a reply from ARP. Linux/UNIX is the basis for the complete collection of motions. One of the key characteristics that distinguish P0F from other systems is that it can detect minimum TCP/IP variations between various kinds of systems such that fingerprint generations are similar to other insecure operating systems (Bhagwani et al., 2019). The failure to mimic the insecure web application could be one of the bottlenecks for honeypots. Only a web server with a custom script to be used conveniently by an expert hacker is fitted with imitation. Moreover, this text has a lack of intensity to compensate for shifts within the network. Therefore, "honeyd-online" is viewed as an interactive honeypot of low level with the basic output capability. for the Web application honeypot.

Honeypots were used by the Sherif Khattab team to meet (DDoS). The way the network system was secured was employed. In the web framework that works against denial of service attack the architecture suggested can contribute. It was discovered that Amazon and Paypal were in receipt when DDoS attacks were involved. The attacks on Amazon and Paypal targeted the companies' web applications while other servers of the businesses concerned have respectively not been targeted (Negi et al. 2020).
Dig deeper into Digital Records and Ethical Challenges in Healthcare with our selection of articles.
Reference
Babiker, M., Karaarslan, E. and Hoscan, Y., 2018, March. Web application attack detection and forensics: A survey. In 2018 6th International Symposium on Digital Forensic and Security (ISDFS) (pp. 1-6). Ieee.
Baykara, M. and Das, R., 2018. A novel honeypot based security approach for real-time intrusion detection and prevention systems. Journal of Information Security and Applications, 41, pp.103-116.
Baykara, M. and Das, R., 2018. A novel honeypot based security approach for real-time intrusion detection and prevention systems. Journal of Information Security and Applications, 41, pp.103-116.
Bin Sulaiman, R. and Ahmed Rahi, M., 2019. A Detailed Study on Web-Based-Honeypot To Propose Mitigation Framework in Web Application. Masud, A Detailed Study on Web-Based-Honeypot To Propose Mitigation Framework in Web Application (December 2, 2019).
Dahiya, P. and Srivastava, D.K., 2018. Network intrusion detection in big dataset using spark. Procedia computer science, 132, pp.253-262.
Danchenko, N.M., Prokofiev, A.O. and Silnov, D.S., 2017, February. Detecting suspicious activity on remote desktop protocols using Honeypot system. In 2017 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (EIConRus) (pp. 127-128). IEEE.
Guarnizo, J.D., Tambe, A., Bhunia, S.S., Ochoa, M., Tippenhauer, N.O., Shabtai, A. and Elovici, Y., 2017, April. Siphon: Towards scalable high-interaction physical honeypots. In Proceedings of the 3rd ACM Workshop on Cyber-Physical System Security (pp. 57-68).
Hamada, A.O., Azab, M. and Mokhtar, A., 2018, November. Honeypot-like moving-target defense for secure iot operation. In 2018 IEEE 9th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON) (pp. 971-977). IEEE.
Huang, C., Han, J., Zhang, X. and Liu, J., 2019. Automatic identification of honeypot server using machine learning techniques. Security and Communication Networks, 2019.
Jia, Z., Cui, X., Liu, Q., Wang, X. and Liu, C., 2018, June. Micro-Honeypot: using browser fingerprinting to track attackers. In 2018 IEEE Third International Conference on Data Science in Cyberspace (DSC) (pp. 197-204). IEEE.
Negi, P.S., Garg, A. and Lal, R., 2020, January. Intrusion detection and prevention using honeypot network for cloud security. In 2020 10th International Conference on Cloud Computing, Data Science & Engineering (Confluence) (pp. 129-132). IEEE.
Ng, C.K., Pan, L. and Xiang, Y., 2018. Honeypot frameworks and their applications: a new framework. Springer Singapore.
OWASP 2017, https://owasp.org/www-project-top-ten/OWASP_Top_Ten_2017/ (accessed on March 2021)
PSecurity (2021), web Applications vulnerabilities and threats: statistics for 2019
Vetterl, A. and Clayton, R., 2018. Bitter harvest: Systematically fingerprinting low-and medium-interaction honeypots at internet scale. In 12th {USENIX} Workshop on Offensive Technologies ({WOOT} 18).
Vetterl, A. and Clayton, R., 2019, November. Honware: A virtual honeypot framework for capturing CPE and IoT zero days. In 2019 APWG Symposium on Electronic Crime Research (eCrime) (pp. 1-13). IEEE.
Wafi, H., Fiade, A., Hakiem, N. and Bahaweres, R.B., 2017, May. Implementation of a modern security systems honeypot honey network on wireless networks. In 2017 International Young Engineers Forum (YEF-ECE) (pp. 91-96). IEEE.
Wang, K., Tong, M., Yang, D. and Liu, Y., 2020. A Web-Based Honeypot in IPv6 to Enhance Security. Information, 11(9), p.440.
Yamin, M.M., Katt, B., Sattar, K. and Ahmad, M.B., 2019, March. Implementation of insider threat detection system using honeypot based sensors and threat analytics. In Future of Information and Communication Conference (pp. 801-829). Springer, Cham.
What Makes Us Unique
- 24/7 Customer Support
- 100% Customer Satisfaction
- No Privacy Violation
- Quick Services
- Subject Experts



