Network and Cloud Security
Introduction
Cloud computing security denotes the broad set of applications, policies, controls and technologies used in protecting the virtualized IP, services, data applications as well as any infrastructure linked to cloud computing. Apparently, cloud security is largely regarded as a sub-domain of network security and computer security. One of approaches used in ensuring cloud security is cryptography, commonly referred to as cipher. The latter denotes the algorithm meant for performing either encryption or decryption. Cryptography is largely regarded as a science engaged in securing digital data through make it unintelligible as far as the unauthorized access especially during storage and transmission. In the pursuit of security measures, cryptographic ciphers are thought to play a significant role in developing security schemes for a long period of time.
Improvements have always been introduced to bolster the existing techniques. Notably, development of security schemes would essentially rely on the available resources. Currently, robust security measurement and high processing power are two properties that are consistently observed in most of the schemes. In this context, a number of ciphers will be reviewed included the block ciphers, shift ciphers and stream ciphers among others. More attention is given to the proposed cipher, which will be explored and implemented at the same time. For students pursuing their studies in cloud computing and related fields, seeking data analysis dissertation help can provide valuable insights into these complex cryptographic principles.

Existing ciphers
A number of ciphers have been floated over the years in response to security mechanism and gaps noted in the available schemes. First, a stream cipher is regarded as a symmetric key cipher in which the plaintext digits are essentially combined with the relevant pseudorandom cipher digit commonly referred to as the keystream. Every plaintext digit in the stream cipher is commonly encrypted one at every time in correspondence to the keystream. Essentially, the stream cipher algorithms would peruse the intelligible message as well as convert or translate symbols of the relevant plaintext into a cipher text symbol (De Cannière 2006). The symbol is commonly regarded as a both with performed transformation covering exclusive OR. As a result of the bit by bit encoding, the schemes are faster and lighter. Stream ciphers carry with them random structures, which are also easier to implement on the hardware. The common stream ciphers include the Rivest Cipher 4, or RC-4, and the second one is ChaCha 20. Stream ciphers have their own areas of strengths and weaknesses as well. First, stream ciphers are said to be faster and lighter when compared to block ciphers. They are also advantageous in terms of low error propagation as the encryption process would not affect the subsequent symbols. Besides, stream ciphers are best for instances where the quantity of data is either continuous or unknown (Singh and Deshpande 2018). The limitations of stream ciphers include its failure in provision of authentication or the integrity protection. Stream ciphers are also susceptible to insertions as well as modifications, which makes it difficult to implement properly.
The second cipher constitutes the block ciphers, which are commonly known for converting the block of the plaintext into the block of the cipher text. Block ciphers are known to be slower and bulkier as well as due to the fact that they entail division of the entire plaintext into blocks. At the same time, block ciphers depend on the confusion as well as diffusion concepts. The ciphers are associated to simpler software implementation and carry with them separate modes of operations (Rubinstein-Salzedo 2018). Most of the block ciphers are said to run on either the fastest or simplest modes which include the Electronic Code Book Mode and Cipher Block Chaining. Common block ciphers applied in many scenarios include the Advanced Encryption Standard (AES), which is said to have been developed by the Belgian cryptographers Joan Daemen and Vincent Rijmen. Development of AES basically relied on the principle associated to substitution-permutation network as well as a combination of substitution as well as combination. Another type of block ciphers is the Data Encryption Standard (DES), which is confirmed to have been developed in the year 1970 by the commonly known IBM. DES takes in a 64-bit plaintext and eventually converts it, after considering a series of operations, into a relevant 64-bit cipher text. The cipher is regarded to be symmetric and utilizes a key across its operations characterized by 64-bits.
Notably, 56 bits of the total 64 bits are used in encryption and decryptions while the remainder 8 bits are utilized in checking parity. The last type of the block ciphers includes the Triple-Data Encryption Standard (3DES). The latter runs over the DES algorithm three times on a relevant plaintext. This type makes use of the 168 bit key as well as operates on the 64-bit block size. Generally, block ciphers have their own areas of strength and weaknesses (Schneier 2015). First, block ciphers experience high diffusion with information from the plaintext symbol being diffused into a range of the cipher text symbols. Secondly, block ciphers are immune to tampering, which makes it difficult to introduce symbols without detection. Apart from the areas of strength, some of the limitations of block ciphers include the fact that they need more memory given that they involve huge chunks of data. In addition, block ciphers are susceptible to noise in the course of transmission (Tiessen 2017). This implies that when one tamper with one side of data, then the rest remains unrecoverable.
Take a deeper dive into Hardware Configuration for Virtual Machines with our additional resources.
The third type of ciphers is the shift ciphers, or the Caesar ciphers. The latter entails replacement of every letter in a given message by a significant letter, which is a fixed number of some positions. The number is largely denoted as the encryption key. If the encryption key is 3, then the encoded text is FRRNLH. However, when shift cipher encryption is performed, then the text “Pizza” is likely to translate into SLCCD with letter Z being replaced with C. Essentially, the shift cipher is normally incorporated in the most complex schemes like Vigenere cipher and the ROT13 system, which is considered as part of the modern applications. The single-alphabet substitution is rarely recommended given that it can easily be broken and this would offer no communications security. The advantage with shift ciphers is that they can easily be adopted due to their simplicity (Holden 2018). However, shift cipher can still have limitations because it presents the most conspicuous scenarios for breaking the cipher. In the first case scenario, an attacker understands simple substitution the cipher applied but may not necessarily know the Caesar scheme. With frequency analysis, an attacker would easily take note of the pattern words and regularity. In the second case scenario, the attacker understands the scheme in use but rarely knows the shift value. With only limited range of possible shifts, the brute force attack can be applied in testing each turn.
Transposition cipher is another cipher method where positions taken by the units in the plaintext are shifted based on a regular system. This implies that the involved cipher text comprises of the permutation seen across the plaintext. A bijective function is essentially used in the positions of the character for the purposes of encrypting, and the inverse function is applied for decryption. The transposition ciphers are advantageous in the sense that it makes use of the secret key ciphers due to similarity between the decryption and encryption key. Besides, transposition ciphers would take a long time for one to break in case the encryption is done twice. The method still has a number of limitations including the fact that the cipher can easily break when compared with other techniques. Again, both keys should be kept secretly because when one is identified, then chances are that the one would obviously be found.

Specification of the proposed encryption/decryption algorithms
The proposed encryption constitutes the modified version of block ciphers. The latter constitute the deterministic algorithm known for operating on the fixed length of the group of bits known as the blocks. The proposed is known for operating as elementary components across the design with a range of the cryptographic protocols (Chakraborti et al. 2017). The encryption algorithms involved in the block cipher commonly takes fixed sizes of the input b bits and subsequently yields a cipher text of the same bits. The proposal of this approach was essentially based on a range of modes of operations that aid almost same outcomes.
Before establishing the mode of operation, the design principles needed to be observed. Three critical aspects of the design include number of rounds, key scheduling and the design of function F (Chakraborty and Sarkar 2016). Significantly, the higher the number of rounds, the harder it becomes to perform the crypto-analysis. Constantly, the number of round would be considered for known cryptanalytic efforts, which would call for a greater effort as preferred against the simple brute force. Designing function F would depend on the S-boxes (Ferguson et al. 2015). The function F can be nonlinear in the course of the design. Avalanche properties would be preferred, which is the same case with the bit independence criterion. The key schedule algorithm is essential in generating the sub-keys for every round. However, no general principles have been produced in determining the key schedule algorithm.
Product Development
The principles applied to the modes of operations, with the first mode being the electronic code book, which is considered the easiest mode. Direct encryption of the block attached to the plaintext is considered with the output shown in terms of the blocks of the encrypted cipher text.
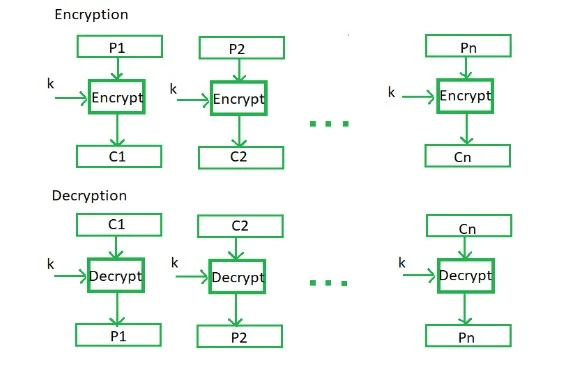
Figure 1: The ECB mode of the Block Cipher
Further details could be added or adjusted on the Cipher Feedback Mode. Vector IV is applied in the first encryption as well as the output bits are essentially divided in a set of sand b-s bits. The output feedback mode subsequently observes the same process as the one applied in the cipher feedback model with exceptions noted in the encrypted output that is send as a feedbac k. The mode is said to be suitable in putting up a better resistance against the bit transmission errors while decreasing the relationship or dependency (Baksi et al. 2018). The finalized mode is the counter mode where the counter initiated value is essentially encrypted as well as expressed as an input to XOR that yields the ciphertext block. The mode is considered to be independent of the use of the feedback and can therefore be implemented separately as indicated below.
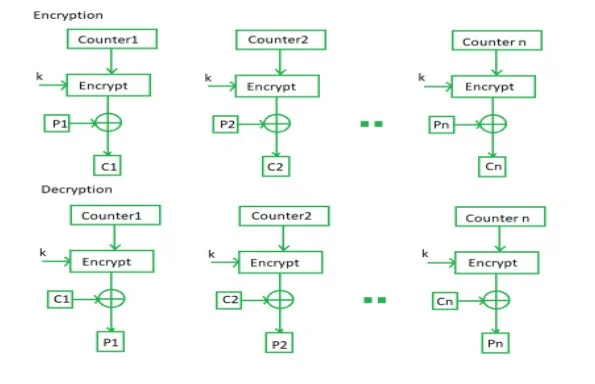
Figure 2: The CTR mode of the block cipher
Conditions for the design indicate that no output bit should be close to the linear function linked to the input bits. Every row of the S-box needs to indicate 16 possible combinations of the output bit. In cases where two inputs differ in 1 bit, then it folllows that the outputs need to differ in two or more bits. For non-zero 6 bit difference in terms of the inputs, then a maximum of 8 of the 32 bits should exhibit the difference, which may again yield significant output difference.
Evaluation of the proposed cipher
A combination of the ECB and CTR mode of operations in the proposed model is likely to yield a number of strengths and limitations. First, the parallel block encryption is made possible through the proposed model, which makes it the fastest means of encryption. Secondly, this can be one of simplest ways of block cipher. In addition, there might be no scenarios or limited scenarios of data loss as a result of the shift register. The approach is more robust compared to the modes of stream cipher as discussed before. A number of weaknesses can still be encountered in the proposed model. First, the system can be vulnerable to cryptanalysis as a result of the direct connection between the cipher text and the plaintext. Blocks can be slower due to the fact that they consume more memory.
Ethical Issues
Development of block ciphers would be regarded as a software development process, which should equally pay attention to ethical issues and concerns at the same time. The first ethical issue put into consideration regards software accuracy and complexity. The design and product development team will at all times show the ability of knowing and predicting every states and ensure that the erroneous rate is relatively low. The team shall document the assumptions, develop the test conditions as well as perform system verification and validation using the well-established approaches (Gotterbarn 2017).
The project also acknowledges the intellectual property rights in which it defines the communication media via which the team delivers the block cipher to the users. The team also filters the knowledge that need to be possessed by people as well as organizations regarding the software development process. Under property considerations, the project observes authorship and therefore pursues patent rights which shall approve the legal ownership of the project or idea under consideration. This implies that no other party shall be required to take the idea without seeking necessary permission from the legitimate owners (Eskerod and Jepsen 2016). Protection of an idea or project is always ethical for the purposes of avoiding fraud, malice and blackmailing propagated by the ill-interested parties.
Project management
Developing the block cipher is regarded as a software development project, which also calls for the attention of project management. In this context, the project pursues Software Development Project Management (SDPM), which is a model that integrates software development life cycle and the scope of project management. The lifecycle parades the organizational constraints attached to the project with defined phases of planning, analysis, designing, implementation, testing and integration and maintenance. SDPM is advantageous to the project because it provides the clear view of the whole project in terms of the personnel involved, timeline, and the objectives of the project and resource requirements for every phase (Eskerod and Jepsen 2016). SDPM also sets the costs as well as integrates the staffing decisions in the course of project development as far as concrete prioritization and information are put into consideration. The tool also produces significant deliverables that can meet both the design and the development standards established at every step. It is worth noting that the tool gives room for developers to measure as well as control the output while performing operations iteratively.
Project Evaluation
The project adopts the integrative indicators in determining the success or failure of the project before introducing control measures. Some of the observable parameters in the integrative parameters include the costs, complexity, quality, duration, cross platform and suability. The project shall weigh the integrative indicator based on the degree of success. If the degree falls above the mean but never hits unit, then control measures can be introduced to perfect the system (Niazi et al. 2016). However, when the average falls below the mean mark, then no compensation would be considered and the project would be considered to have failed.
Conclusion
First, the discussion focused on different types of ciphers and pointed out the strengths and weakness in each case. More attention was given to the ECB and CTR mode of operation of block ciphers, as preferred over the stream cipher, shift cipher and transposition ciphers. Advantages of the proposed model include its robustness, simplicity in the context of simplicity and limited scenarios of data loss. However, the approach can be slower due to consumption of memory.
Continue your exploration of Navigating the Fashion Landscape with our related content.
References
- De Cannière, C., 2006, August. Trivium: A stream cipher construction inspired by block cipher design principles. In International Conference on Information Security (pp. 171-186). Springer, Berlin, Heidelberg.
- Singh, P. and Deshpande, K., 2018. Performance Evaluation of Cryptographic Ciphers on IoT Devices. arXiv preprint arXiv:1812.02220.
- Rubinstein-Salzedo, S., 2018. Other Types of Ciphers. In Cryptography (pp. 63-73). Springer, Cham.
- Schneier, B., 2015. Algorithm Types and Modes. Applied Cryptography, Second Edition: Protocols, Algorthms, and Source Code in C, pp.189-211.
- Tiessen, T., Rechberger, C. and Knudsen, L.R., 2017. Secure Block Ciphers-Cryptanalysis and Design.
- Holden, J., 2018. The mathematics of secrets: cryptography from caesar ciphers to digital encryption. Princeton University Press.
- Ferguson, N., Schneier, B. and Kohno, T., 2015. Block Ciphers. Cryptography Engineering: Design Principles and Practical Applications, pp.41-62.
- Baksi, A., Bhasin, S., Breier, J., Khairallah, M. and Peyrin, T., 2018, April. Protecting block ciphers against differential fault attacks without re-keying. In 2018 IEEE International Symposium on Hardware Oriented Security and Trust (HOST) (pp. 191-194). IEEE.
- Chakraborti, A., Iwata, T., Minematsu, K. and Nandi, M., 2017, September. Blockcipher-Based Authenticated Encryption: How Small Can We Go?. In International Conference on Cryptographic Hardware and Embedded Systems (pp. 277-298). Springer, Cham.
- Chakraborty, D. and Sarkar, P., 2016. On modes of operations of a block cipher for authentication and authenticated encryption. Cryptography and Communications, 8(4), pp.455-511.
- Gotterbarn, D., 2017. The use and abuse of computer ethics. In Computer Ethics (pp. 57-62). Routledge.
- Eskerod, P. and Jepsen, A.L., 2016. Project stakeholder management. Routledge.
- Niazi, M., Mahmood, S., Alshayeb, M., Riaz, M.R., Faisal, K., Cerpa, N., Khan, S.U. and Richardson, I., 2016. Challenges of project management in global software development: A client-vendor analysis. Information and Software Technology, 80, pp.1-19.
Discover additional insights on The Importance of Cyber Security in Modern Internet Age by navigating to our other resources hub.
- 24/7 Customer Support
- 100% Customer Satisfaction
- No Privacy Violation
- Quick Services
- Subject Experts



