System Design and Java EE Architecture Evaluation
Part 1
You should start from the system design and related implementation code you produced for TMA 02
Include your detailed class diagram at the start of your TMA, together with a brief summary of any substantial changes you may have made compared with your TMA 02 submission.
i.Based on a use case you defined previously for your system model a possible event-driven interaction to link presentation and business logic -using UML state machine diagrams whenever appropriate.
Justify your choices.

include the use case in your answer (the use case is not included in the word count).
(i): appropriate design choices as well as appropriate use of UML state machine diagrams
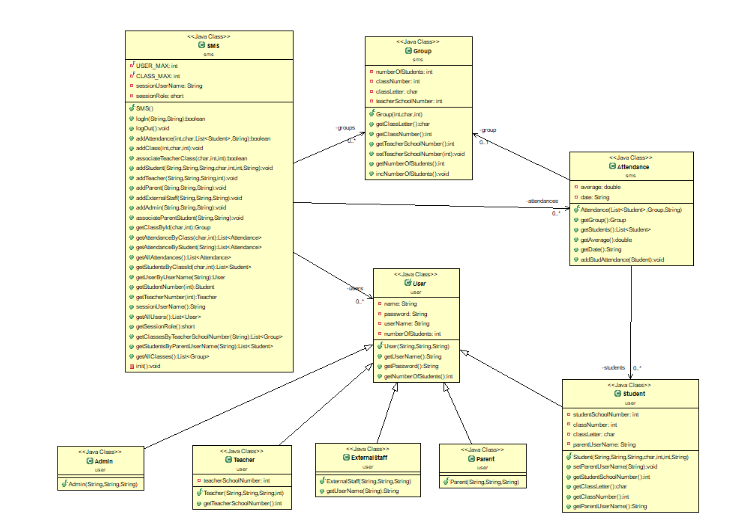
Name, identifier, version: Register student, SMS 01, Version 1.0
Initiator: Admin.
Goal: to register a new student;
Assumptions: Student is not registered
Main scenario:
1. the actor selects to register a new user;
2. the system asks for the name;
3. the actor inserts the new user’s name;
4. the system asks for a username;
5. The actor inserts a username;
6. The system asks for a password;
7. The actor inserts a password;
8. The system asks for what type of user to create;
9. The actor selects – student;
10. The system asks for student number;
11. The actor inserts the student number;
12. The system asks for class number;
13. The actor inserts class number;
14. The system asks for class letter;
15. The actor inserts class letter;
16. The system asks for the parent username;
17. The actor inserts the parent username;
18. The system records all details and confirms the user was successfully created;
Extensions:
3.1 The actor does not insert the new user’s name;
5.1 The actor does not insert a username;
5.2 The username inserted is already registered
7.1 The actor does not insert a password;
10.1 The actor does not select to register a student;
11.1 The actor does not insert a student number;
11.2 The student number is already registered;
13.1 The actor does not insert a class number;
15.1 The actor does not insert a class letter;
17.1 The actor does not insert a parent username;
Following (OU, 2021), in order to build a state machine model of the system behaviour for this use case. There is the need to identify the states, particular events and specific actions from the scenario and extensions, referring to Table 1. Looking for further insights on Kano's Product Satisfaction Model? Click here.
Following the described triggers, actions and state in Table 1, a possible model for this interaction is illustrated in the state machine diagram in Figure 1.

The process of registering a new student starts with the initial ‘pseudostate’ (OU, 2021): - ‘actor selects to register a new user’. This means that, it is assumed that the actor is an Admin and is logged in. From here, the system transitions to collect all the personal details of the new user. These first three Events are: - Collecting user name; username; password and corresponding States and Transitions (OU, 2021). Belong to the <
ii. Describe a possible tiered/layered architecture for your systembased on an application model such as Java EE
identifying possible uses of the specific technologies within your system
Justify your choices.
(ii): a good understanding of the application model and how it can be contextualised to your development problem, with appropriate justifications also provided
As described by (OU, 2021), a possible tiered/layered architecture for the presented system, that follows Java EE. Would adopt a four-tier structure, implementing Java EE components, such as:
An ‘Application client’, this is a Java application that runs in the client container/tier and has access to components in the business tier. For the present system, in functional terms, (Rozanski and Woods (2005), cited by (OU, 2021) this refers to the client’s web browser.
A ‘Java Server Pages’ (JSP) that run in the web container/tier and combine dynamic content, as Java code, with static web mark-up content.
An ‘Enterprise JavaBeans (EJB) which run in the business tier and are part of the EJB container.
For the presented system, the web and EJB container/tier are provided by adopting a platform as GlassFish Enterprise Server. This means that the developer/student can only focus on the definition and development of the system’s business functionality.
In terms of layers, and following Java EE as an Enterprise Information System. The system presented will employ a three-layer common architecture:
A ‘Presentation layer’, that will bridge between the users and the system; generating the system’s user’s interface and capturing user’s events; in functional terms, for the present system, this layer will allow the user to register a new user-student, execute attendance and view attendance record;
A ‘Business layer’, where the business functionality is set; this is where, different entities are created, where the relation and multiplicity between them defined;
A ‘Data layer’, where the persistence data (Java Persistence AP - JPA), will be stored and managed. This layer will hold the entity classes (Attendance; Student Attendance; Groups; User), stored as a relational database table.
The presented system is in line with Java EE, by implementing JavaServer Faces, EJBs and JPA within a tiered/layered architecture. This will further allow a separation of concerns, which will promote low coupling, reuse and increase flexibility to make changes in the system.
iii. Consider your previous design for a system operation;
consider how such a design should change in the context of an implementation which makes combined use of those technologies;
reflect on similarities and differences.
Make use of UML models whenever appropriate to compare the two designs.
include the system operation specification in your answer (the operation specification is not included in the word count).
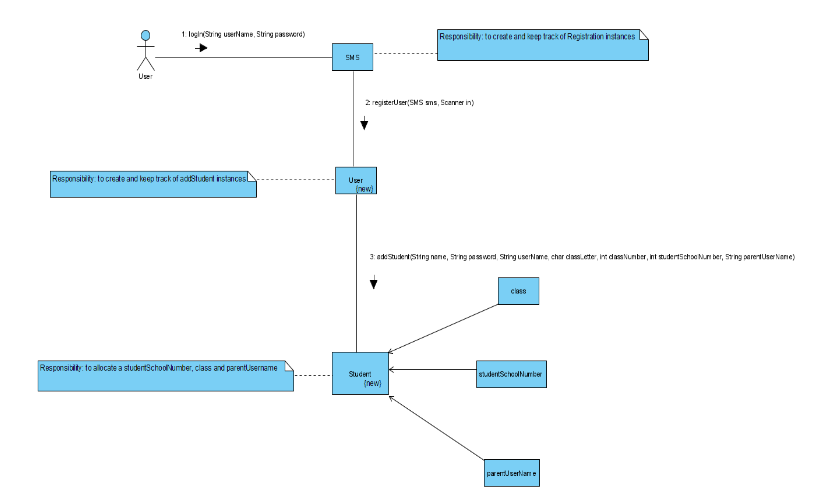
Regarding the system operations ‘addStudent’:
Identifier, version: SMS 01, Version 1.0
Context: SMS
Signature: addStudent (String name, String password, String userName, char classLetter, int classNumber, int studentSchoolNumber, String parentUserName)
Invariant: true
Precondition:
-- Student username is not registered
-Student number was not allocated
Post condition:
-- New Student Registration is created
-- A new student School Number is allocated to the new student
--student is allocated to a new class
--a parentUserName (if already registered in the system) is allocated to the new student
-a new User-student is created
--it is possible to record the student attendance
Following the approach taken in the module (OU, 2021), the previous design expressed the responsibilities, illustrated in figure 1 (SMS – Class diagram).
In the new design bellow, figure 2, the responsibilities are assigned as follows:
Entity classes are employed to keep hold of information about Groups, this is school classes; Users, Attendance and StudentAttendance;
As mentioned by (OU, 2021), Façade session beans add persistence logic, by using the entity managers for creating and keeping track of persistent data such as users’ role; and user personal details such as password, username, name, etc.
The controllers – JSF beans – deliver business logic to bridge between presentation and persistence layers. For the present, Java EE based system, for each controller corresponds a façade session bean. This means, that these controllers coupled with their views (xhtml pages), will be the new entry point to the system for the user.

iv. Carry out a proof-of-concept implementation that exemplifies the combined use of the technologies in (iii).
You should briefly describe the aspect of your system covered by the implementation
explain your design decisions and include relevant code for your entity classes and their relations (the code is not included in the word count)
Your implementation should be consistent with the approach taken in the module.
(iii) and (iv): an appropriate design which makes good use of the three named technologies (JavaServer Faces, EJBs and JPA), and a thorough comparison between the two designs
v. Explain how your architecture model in (ii)
could be modified to integrate RESTful services alongside other program components.
Make use of UML models whenever appropriate.
vi.For one of the RESTful services in (v),
carry out a proof-of-concept implementation, explaining how this integrates with other implemented components in your system You should include related code in your answer (the code is not included in the word count). Your implementation should be consistent with the approach taken in the module
(v) and (vi): a proof-of-concept implementation which makes good use of the relevant technologies for a specific aspect of your system; there’s no expectation of a sophisticated implementation, so feel free to simplify things as you feel appropriate – but do include a note for your tutor of any simplification made
vii.Reflect on the pros and cons of using an enterprise framework for the development of information systems.
(vii): a critical reflection of what you see as the pros and cons of using such frameworks in practice, based on what you’ve learnt in this module and any other professional experience you may have.
Part 1 word limit: 1400 words; 70 marks. Use case, operation specification and code are not included in the word count.
Part 2
Discuss enterprise systems integration as an approach to software development.
You should focus on:
what is meant by ‘enterprise system integration’
different ways in which integration can be achieved
key technologies for integration
acknowledged benefits and difficulties.
You should also reflect on how all this may relate to your own professional practice, and to knowledge and techniques you have acquired through studying the module.
Part 2 word limit: 500 words; 20 marks.
Following the definition by Panian (2006), ‘Enterprise System Integration’ (EIS), denominates the task of integrating applications, data, software products and frameworks, with the intend to simplify and automate business processes and operations. Qi et al. (2006), cited by (Li Da Xu, 2015), defines EIS, as a system that aims at integrate all the business processes in a holistic way by using a single information technology architecture.
EIS has emerged in the past decades due to the rise of the global economy, intense competition and fast development of information technology (Li Da Xu, 2015). EIS have become widely used, because traditional custom-built systems were developed to address a single specific need (Panian, 2006). EIS on their turn are able to support and improve the different stages of a typical business cycle, such as:
Product life cycle;
Engineering project;
Customer order and inventory;
Distributor–reseller;
Supplier and procurement;
Demand planning;
Warehouse management and freight;
Panian (2006), also pointed out four major reasons for the organisations to develop and implement EIS:
New systems have not replaced legacy systems;
The need to consolidate and globalise;
The search for increased productivity;
Raised expectations from web experiences;
EIS offers a platform to integrate these distributed systems, allowing a single view of the organisation’s enterprise data and infrastructure (Panian, 2006). Considered ground-breaking in terms of computer applications for business and industries, EIS is now one of the most fastest growing and profitable areas in the software industry (Li Da Xu, 2015).
EIS are developed within several categories. Most EIS can be classified in one (or more than one) of the following four main categories, (Panian, 2006):
Data coordination/data consistency – It moves transactional data between applications to improve consistency, having core technology, a message broker or integration server;
Business process management/orchestration – It models and coordinates the workflow between the individual functions in separate applications, with the aim to automate and streamline previously independent business processes;
Business activity monitoring – It supports the management with instant feedback of changing events across the enterprise, ensuring improving this way business decision-making.
Composite applications development – It mainly combines the data and functionality of an enterprise, to build new applications and/or functionalities, levering up business processes within back-end operational systems.
Concerning benefits, EIS allows cost savings due to streamline business processes, resulting in improved efficiency. EIS also enables a “forward-looking”, this is, organisations gain a real-time view of their data and operations, which can lead to better and well informed decisions (Panian, 2006). Adding up the flexibility to adapt business processes is effective to support growth and new businesses challenges.
There are seven “favourable characteristics” of an EIS (Panian, 2006):
Connection – It provides communication between the integration platform and the applications integrated, by applying an adapter (piece of code), that will translate the native protocols of the target resource by connecting them to the EIS.
Abstraction – The process of representing the data and functionality in a consistent way, easing the need to understand the different protocols, etc., by each of the applications integrated. Some of the technology approaches to abstraction can be:
. J2EE;
. XML and Web services;
. ‘Canonical’ form;
Coordination – the capacity to manage the flow of messages in the EIS;
Storage – EIS require a way to store, retrieve, manipulating and analysing data;
Orchestration – Modelling and automating businesses processes;
Development – Building composite applications, by introducing new business logic and user-facing front ends to the abstracted services and business processes;

Management – EIS have as management features:
. Configuration management;
. Queue and process monitoring;
. Detailed event logs;
. Usage histograms;
Some of the disadvantage regarding EIS, pointed out by (techvera, 2021), can be:
Security – System integration makes the system more vulnerable to data leak due to the interconnected channels through which data flows;
Upgrading – All the applications integrated need to be upgraded separately, adding complexity and time consumption;
Cost – Every program integrated had an individual cost that added up to the final sum. This final sum can be higher than developing a custom-made solution;
The author of the present paper hasn’t had the opportunity of developing and implementing EISs. However, due to the main interest of the author being ‘technology enhanced learning’, EISs are a fundamental part for developing ‘technology enhanced learning tools’.
Part 3
Identify a contribution you’ve made to the ‘Tracking the leading edge’ forum in which you provide some insightful comment and reflection related to a specific topic under discussion. Briefly summarise your contribution and any insights you’ve shared with your fellow students. You should include a sample posting in your answer.
Regarding the ‘Tracking the leading edge’ forum, the author contributed with a post with the title: “AI in Education” – appendix 1. The aim of the post was not to describe the potential of AI in Education, but to question if Ai can be creative following a podcast by https://aipodcast.education/is-ai-creative. The author started with a brief description of what is commonly understood by ‘creativity’, A ‘human unique capacity’; ‘thinking outside the box’; ‘being original’ in terms of music and visual arts creation, problem solving, etc. Having in mind that AI is also a product of the human creative nature, the author then sets the question: ‘How can AI be considered creative?’
The author points out that, when human beings create, they do so because they ‘love it’. The author now realises that, the word ‘love’ didn’t bring any clarity to the question. The aim of such statement was to highlight the difference between the human that ‘feels’ and is self-aware, and the machine that lacks such capacity, being only able to follow an algorithm. However, as the presenters described, when AI learned how to play the game GO by watching humans playing. It came out with moves not played by the humans’ players. One of the presenters stated then that if creativity is the ability to find new ways to solve problems. Then, this AI capacity must be considered ‘creative’.
In terms of arts and digital visual arts in particular, the presenters also debate the situation when AI is employed by humans to complete an image. Is it the human that employed AI as a tool or AI by itself that is being creative?
The interest of the author in this theme rises from the main aim of computer science in general that is to replicate the human cognitive nature. This is, as the author described: “in the process of creating this great tool that a computer can be. We also understand what makes us humans”.
Appendix 1
Appendix 2
One of my main interests in software development is Technology Enhanced Learning/Assessment tolls; Learning Analytics; Data mining; AIED. This is, the potential that digital technologies can have in education by disrupting traditional learning and teaching methods.
The podcast that I’ve chosen to share is about AI in Education (AIED). The podcast assumes a quite informal and light approach, making it very easy to follow, and the question that is discussed is:
Can AI be creative?
Creativity can be understood as a human unique capacity. Thinking outside the box, being original as in music, visual arts, problem solving, maths, etc., are all a core part of human nature.
AI though, is known as a sequence of algorithms generated by machine. So, the question is: “How can AI be considered creative?”.
If in one side humans create things because they love it. On the other AI as a machine can’t do that. The presenters then take the board game GO as an example and how AI has learned to play just by watching humans playing the game. The interesting point here, highlighted by the presenters is that when AI was playing by itself, it came out with moves that were not played by any human and so observed by AI. So, the question is: Can this AI behaviour be considered “creative”? One presenter (Dan – I think), says that if “creativity” is (also) to find novel ways to solve problems, then we have to accept that AI in this case was/is creative. Dan presents another AI creativity example when using Photoshop 3D. AI can complete on its own a picture (jpg) that was previously edited by a human. Dan’s question is then: Is AI or the human that have applied AI to the picture, which is being creative?
The presenters then turns out to the question: What is art? Lee says that art is “the expression of human creative skills”. From here, Lee points out that art are generally considered a human endeavour. However, as it is possible to understand from a technology perspective. The same way that art makes use of tools such as brushes, paint, stone, musical instruments, etc. It can also make use of AI as a tool.
Personally, this is a subject that I find very interesting. After all, what computers (computer scientists) try to do (in some way) is to replicate the human cognitive process and replicate it artificially, enhancing it with the help of digital technology. So, in the process of creating this great tool that a computer can be. We also understand what makes us humans – humans.
Dig deeper into Securing Big Data in the Cloud with our selection of articles.
- 24/7 Customer Support
- 100% Customer Satisfaction
- No Privacy Violation
- Quick Services
- Subject Experts



