Passwords and Authentication in the Digital Landscape
Passwords
A password is a series of characters used to validate the identity of a user during the authentication process. Passwords are usually used in conjuncture with a username; they are intended to be revealed only to the user and allow the user to obtain access to a computer, program or website. Passwords can range in length and can contain letters, numbers and special characters. Other words that can be used interchangeably are passphrase for when the password uses more than one letter, and passcode and passkey for when the password uses only numbers instead of a combination of characters, such as a personal identifying number (Khamis et al., 2017). For students seeking assistance with such topics, data analysis dissertation help can provide valuable support in understanding and implementing secure authentication methods.
Structure (input)

The storage of passwords or records essentially often takes place according to established organisational frameworks. The module allows arbitrarily complex constructs to be described, which later form the basis for the hierarchical storing of data. It is also possible to describe them based on already defined organigrams for the organization or the agency. Of note, it is also possible to use other parameters, such as the role/task done, as the basis for constructing hierarchies. It is still up to the consumer itself to determine which arrangement is more useful for the intent of the application (Sulavko, 2020).

Scenarios
Creating an account for the related website or the site you want to use. The first most critical move in building your account is to make sure you're on the right URL of the company. In this case, we are going to use scenarios of making an account on the Qualtrics website.
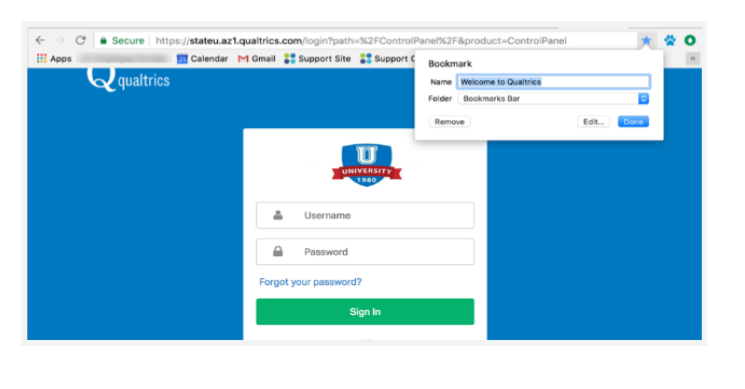
SIGN UP WITH AN ORGANIZATION YOU BELONG TO
If your boss, school, or any company you belong to has a license with Qualtrics, you will also get an account with lots of premium features, at no cost to you!
However, you first have to make careful to sign up at the right URL, or else Qualtrics won’t know what company you’re part of.
In this case, We are attempting to sign up for a State University Qualtrics account. Typically colleagues, teachers, your IT team, and other members of your company are responsible for giving you this connection. Otherwise, it can be listed on your company’s employee portal or your school’s home page.
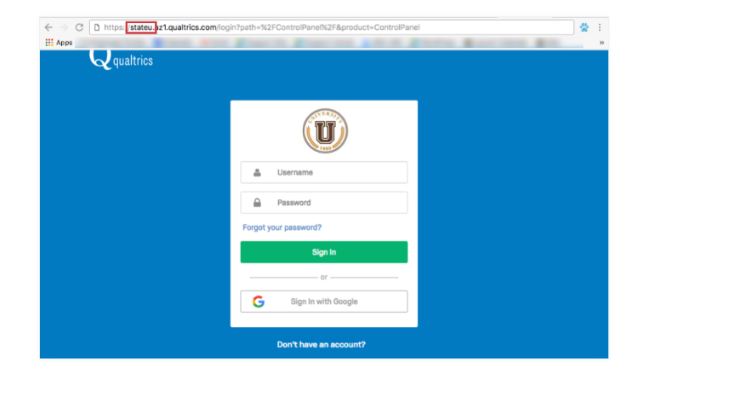
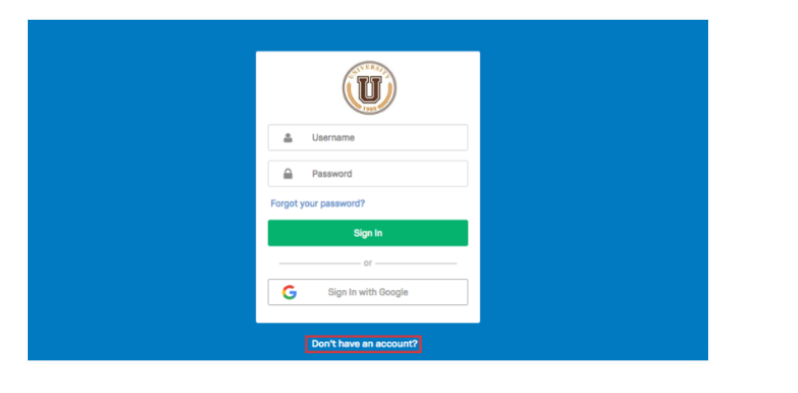
2. To sign up for an account, press the Don’t Have an Account? the link at the bottom of the page.
3. Fill out the form. Usually, you have to use your school or business email address to sign up
Then from there, you will be expected to set up a strong password, you will build and repeat the password, password retype is intended to make sure that you keyed in the right characters in the
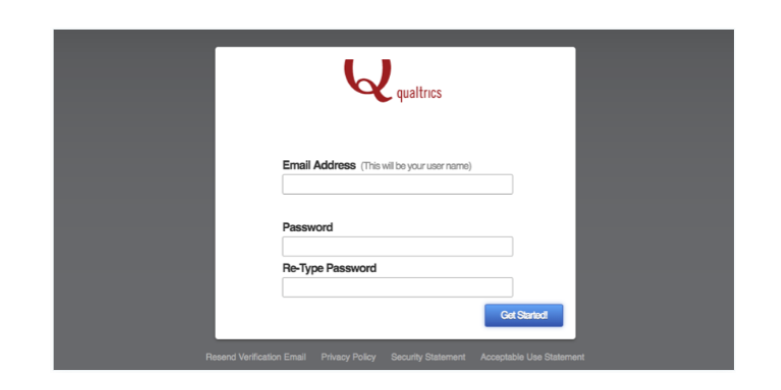
elements of type password provide a means for the user to easily enter a password. The feature is displayed as a one-line plain text editor control in which the text is blurred such that it cannot be interpreted, typically by replacing each character with a symbol such as an asterisk ("*") or a dot ("•"). This character can differ depending on the user agent and OS.
Specifics of how the entry mechanism operates can vary from browser to browser; mobile devices, for example, often display the typed character for a moment before obscuring it, to allow the user to make confident they pressed the key they wanted to press; this is useful considering the limited size of keys and the ease of which the wrong one may be pressed, particularly on virtual keyboards.
The Value
The value attribute includes a DOMString whose value is the current contents of the text editing control being used to enter the password. If the user hasn't entered anything yet, this attribute is a null string ("). If the necessary property is defined, then the password edit box must contain a value other than an empty string to be true. If the pattern attribute is defined, the content of a password control is only considered true if the value passes validation (Babkin, & Epishkina, 2019, January).
After the user input the password according to the structure where it is saved in the system so later it checks the validity of the password.
Validating and authenticating users to a program is one of the main fields of cryptography. Storing passwords correctly are of extremely crucial significance, but it is a field in which many developers struggle. Partly because this field can be very scientific, mathematical and incredibly easy to do wrong, and partly tragic as it is out of sheer laziness (Hundlani et al., 2017).
So, you’re creating a login scheme for your website, and you need to efficiently save the password. The most naive solution is, of course, the really easy one: Just store it. You have a database with a table for all the accounts, and it will possibly look anything like (id, username, password) (Briotto Faustino & Girouard, 2018, October).On user development, you store the username and password in these fields as plaintext, and on login, you remove the row associated with the inputted username and compares the inputted password with the password from the database. If it suits, you let the user in. Perfectly straightforward and fast to execute (Taufiq & Ogi, 2018, September).
Obviously, this is a tremendously poor and vulnerable way of saving passwords. If you would be so unlucky that your account would be compromised, every single of the user's keys would be revealed straight to the naked eye. Let’s highlight the importance of this tragedy with some facts: Most people use the same password for all (or at least multiple) services (Bhana & Flowerday, 2020). So not only did you jeopardize the access to your website but you have theoretically exposed the keys that your customers are using elsewhere; for their personal addresses or internet banks (Ussatova & Nyssanbayeva, 2019). Moreover, if you wanted to store your user's passwords in plaintext, you didn't care much about sanitizing your inputs or using prepared statements to avoid SQL injections. The odds of your website being compromised may not even be that slim (Schechter et al., 2017).
There's a simple way that you can check whether your password is stored in plaintext. Try using the 'recover password' feature of the website. When you get an email asking you what your password is, that's because the website is storing it in plaintext, and this will be an immense red flag! The first solution to introducing a layer of authentication on top of the passwords in your database would be to use encryption (Razvi et al., 2017).
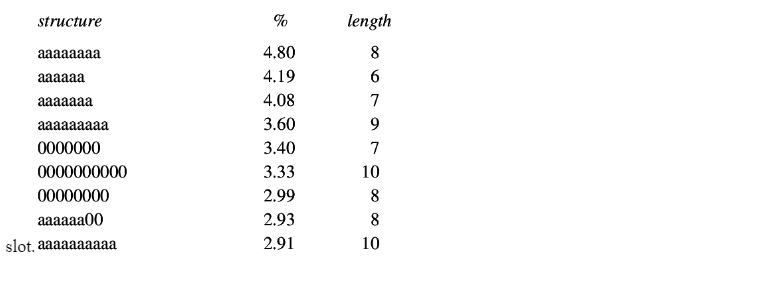
In almost all Linux distributions (and commercial *nixes as well), user information is stored in /etc/password, a text file which contains the user's username, their encrypted password, a specific numerical user-id (called the uid), a numerical group id (called the gid), an optional comment field (usually containing such things as their real name, phone number, etc.), their home directory, and their preferred shell (Nizamani et al., 2017). A standard entry in /etc/password looks anything like this:

Validity :( Compare)
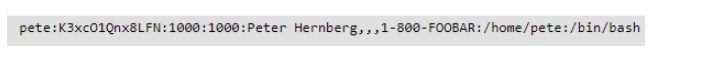
Password checker software essentially checks whether the password is correct or not depending on password policies mention below:
• Password does not include any space.
• Password should contain at least one digit(0-9) (0-9).
• Password length should be from 8 and 15 letters.
• Password can contain at least one lowercase letter(a-z) (a-z).
• Password can contain at least one uppercase letter(A-Z) (A-Z).
• Password should contain at least one unique character ( @, #, percent , &, !, $.
Example
Approach:
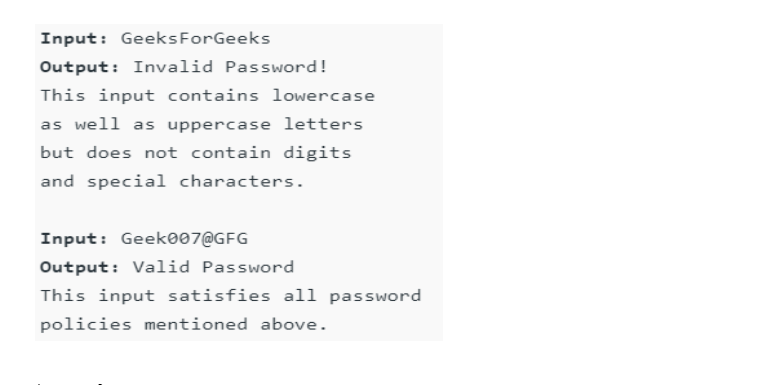
• Create a User-defined exception called “InvalidPasswordException” as explained below.
• Then search for the authenticity of the password on the necessary criteria.
• If every parameter is not met, then throw the InvalidPasswordException.
Scenario



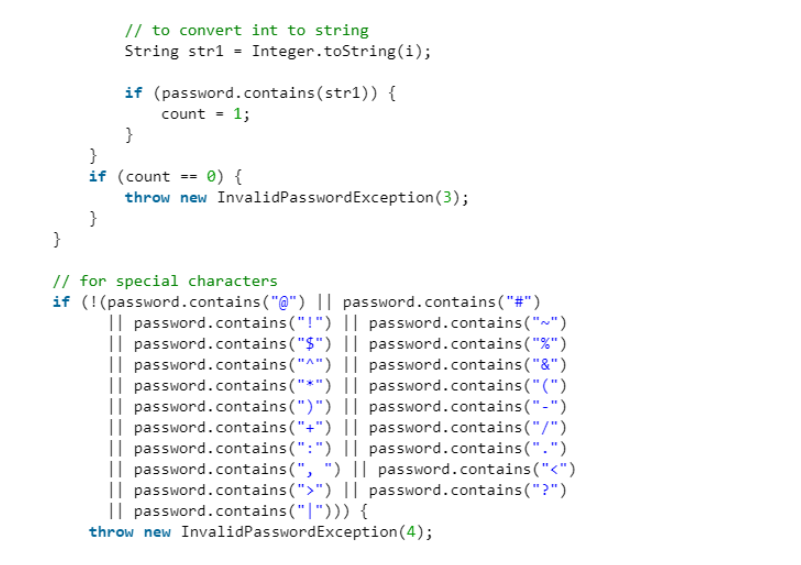
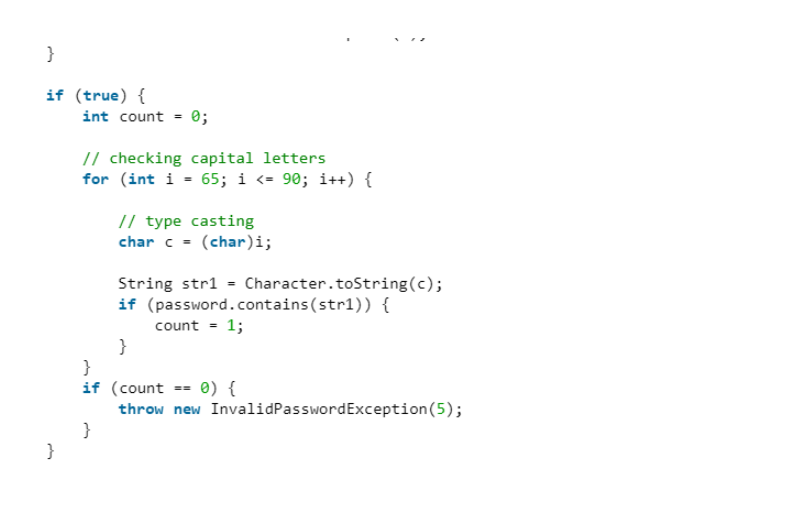
How it reads the inputted password and how it compares if it follows the structure.
The login or Sign Up of every website often needs a confirm password entry and it must be the same as the password. That is simply to guarantee that the user enters the password full of his meaning and there is no misunderstanding occurs. This feature can be applied anywhere in our code like in index file or route file but this comes under the validation component. So we generally choose to code this logic where all the other validations are coded. Here we use ‘express-validator’ middleware to enforce this feature (Dagvatur et al., 2017).
Strength: (Output)
Generally speaking, the strength of a password is determined by three things: the length of the character set used, the length of the password itself, and to a lesser degree, the variation of characters used. Next, let's address the duration of the character collection. A character collection in this way is essentially what it looks like: a set of characters from which you can draw to build your password (Salles-Loustau et al., 2018). Most passwords allow you to use all characters on your keyboard so the character collection in most cases will be all lowercase letters, uppercase letters, numbers, and special symbols such as asterisks and ampersands (Shen et al., 2017). Longer character sets allow for better passwords when properly used. Think about it this way: say someone wants you to pick a number from 1 to 10 and another number from 1 to 100. What will be easier to guess correctly? The solution, of course, is the number from 1 to 10 so there are fewer available numbers to pick from. The same principle applies when picking a password (Zimmermann et al., 2018).
Second, the length of the password is another very significant criterion for evaluating password power. And if you are constructing a password from a broad character set, if it is just a few characters long, attackers can always guess or break this password reasonably quickly (Hadjidemetriou et al., 2019). We suggest a minimum length of 8 letters. This is a very critical part of password strength. eg, a 12 character password can be quite a bit better than an 8 character password.

Lastly, make sure to use a decent combination of characters in your password. A lengthy character collection with a lengthy password is no use if you have the same character replicated over and over as a password. The majority of websites would encourage you to use most (if not all) characters on your keyboard, but it is up to you to use a good range. An ideal password would contain a combination of lowercase letters, uppercase letters, numbers, and symbols. Here’s a map that shows the relative strength of passwords, measured against current brute force attacks. It’s worth noting that as technology progresses and brute-force abilities improve, these passwords get weaker. As shown by the measurements, password character length is the main factor that determines password power.

Although an ideal password consists of several different types of characters and is very long, there, of course, has to be a compromise between protection and how easily you can remember the password. A common method to better reconcile these two is to substitute letters for numbers/symbols that look like certain letters. This is usually a safe practice as long as the password is lengthy, but attackers already know about these methods and can look for those passwords as well. Finally, tacking on a few extra numbers/symbols to the end of the password will go a long way to hold attackers at bay. Just make sure to have a sort of mnemonic system in your brain to better recall these extra characters.
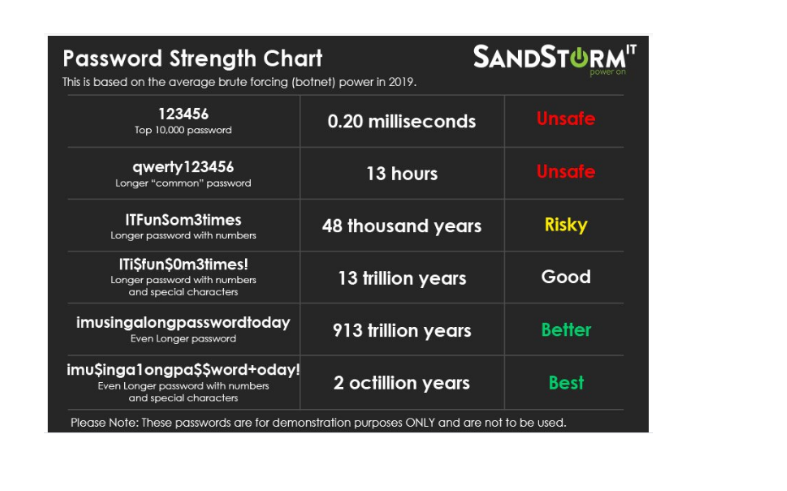
Password-security meters use a scoring feature to judge the strength of a password, showing this score by visual elements. We awarded passwords a score using heuristics like the password’s length and the character classes it included (Bhana & Flowerday, 2020). Although alternate approaches to scoring have been introduced, as described in Section 2, evaluating a password only on heuristics obviates the need for a wide, current dataset of passwords and can be applied easily in Javascript. These heuristics are based on those we found in the wild. In our scoring system, a score of 0 points indicated a null password area, while a score of 100 points filled the meter and showed the text “excellent.” We declared our only password-composition regulation in bold text to the participant as an "8-character minimum" prerequisite. However, we built our scoring algorithm to give passwords containing eight lowercase letters a score of 32, displaying "bad." To achieve a score of 100 in most situations, participants required to meet one of two policies described as better in the literature, which we call Basic16 and Comprehensive8 (Constantinides et al., 2018). Unless otherwise stated by the condition, passwords were allocated the greater of their Basic16 and Comprehensive8 ratings (Ussatova & Nyssanbayeva, 2019). Thus, a password matching any regulation will fill the meter. Each keystroke resulted in a recalculation of the score and updating of the meter.
Take a deeper dive into Parenting and the Role Governments Play In Providing Support for Parenting with our additional resources.
Reference
Babkin, S., & Epishkina, A. (2019, January). Authentication protocols based on one-time passwords. In 2019 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (EIConRus) (pp. 1794-1798). IEEE.
Bhana, B., & Flowerday, S. (2020). Passphrase and keystroke dynamics authentication: Usable security. Computers & Security, 96, 101925.
Briotto Faustino, D., & Girouard, A. (2018, October). Bend passwords on bendypass: A user authentication method for people with vision impairment. In Proceedings of the 20th International ACM SIGACCESS Conference on Computers and Accessibility (pp. 435-437).
Constantinides, A., Belk, M., Fidas, C., & Samaras, G. (2018, July). On Cultural-centered Graphical Passwords: Leveraging on Users' Cultural Experiences for Improving Password Memorability. In Proceedings of the 26th Conference on User Modeling, Adaptation and Personalization (pp. 245-249).
Dagvatur, Z., Mohaisen, A., Lee, K., & Nyang, D. (2019). Secure human authentication with graphical passwords. Journal of Internet Technology, 20(4), 1247-1259.
Hadjidemetriou, G., Belk, M., Fidas, C., & Pitsillides, A. (2019, May). Picture passwords in mixed reality: Implementation and evaluation. In Extended Abstracts of the 2019 CHI Conference on Human Factors in Computing Systems (pp. 1-6).
Hundlani, K., Chiasson, S., & Hamid, L. (2017, September). No passwords needed: The iterative design of a parent-child authentication mechanism. In Proceedings of the 19th International Conference on Human-Computer Interaction with Mobile Devices and Services (pp. 1-11).
Khamis, M., Hasholzner, R., Bulling, A., & Alt, F. (2017, June). GTmoPass: Two-factor authentication on public displays using gaze-touch passwords and personal mobile devices. In Proceedings of the 6th ACM International Symposium on Pervasive Displays (pp. 1-9).
Nizamani, S. Z., Khanzada, T. J., Hassan, S. R., & Jali, M. Z. (2017). A Text based Authentication Scheme for Improving Security of Textual Passwords. International Journal of Advanced Computer Science and Applications, 8(7), 513-521.
Razvi, S. A., Neelima, S., Prathyusha, C., Yuvasree, G., Ganga, C., & Kumar, K. M. (2017, June). Implementation of graphical passwords in internet banking for enhanced security. In 2017 International Conference on Intelligent Computing and Control Systems (ICICCS) (pp. 35-41). IEEE.
Salles-Loustau, G., Le, T., Najafizadeh, L., Zonouz, S., & Javanmard, M. (2018). Cytocoded passwords: BioMEMS based barcoding of biological samples for user authentication in microfluidic diagnostic devices. Biomedical microdevices, 20(3), 1-9.
Schechter, S., Tian, Y., & Herley, C. (2019, June). StopGuessing: Using guessed passwords to thwart online guessing. In 2019 IEEE European Symposium on Security and Privacy (EuroS&P) (pp. 576-589). IEEE.
Shen, S. S., Kang, T. H., Lin, S. H., & Chien, W. (2017, May). Random graphic user password authentication scheme in mobile devices. In 2017 International conference on applied system innovation (ICASI) (pp. 1251-1254). IEEE.
Sulavko, A. E. (2020). Highly reliable two-factor biometric authentication based on handwritten and voice passwords using flexible neural networks. Computer Optics, 44(1), 82-91.
Taufiq, M., & Ogi, D. (2018, September). Implementing One-Time Password Mutual Authentication Scheme on Sharing Renewed Finite Random Sub-Passwords Using Raspberry Pi as a Room Access Control to Prevent Replay Attack. In 2018 International Conference on Electrical Engineering and Informatics (ICELTICs) (pp. 13-18). IEEE.
Ussatova, O., & Nyssanbayeva, S. (2019). Generators of one-time two-factor authentication passwords. Informatyka, Automatyka, Pomiary w Gospodarce i Ochronie Środowiska, 9.
Zimmermann¹, V., Gerber, N., Kleboth¹, M., von Preuschen¹, A., Schmidt¹, K., & Mayer, P. (2018, September). The quest to replace passwords revisited–rating authentication schemes. In Proceedings of the Twelfth International Symposium on Human Aspects of Information Security & Assurance (HAISA 2018) (p. 38). Lulu. com.
What Makes Us Unique
- 24/7 Customer Support
- 100% Customer Satisfaction
- No Privacy Violation
- Quick Services
- Subject Experts



