Solving Traffic with Vehicular Networks
Introduction
Background of the study
Over the last one decade, environmental pollution, accidents, and traffic congestion have become issues of concern in the transportation industry. To solve these problems, increased research has been focused on vehicular social networks (VSNs) and intelligent transportation systems (ITSs) in recent years. Vehicular social networks are a form of mobile networks, which allow nearby vehicles to communicate (Leontiadis, and Mascolo, 2007). These networks also allow for communication between vehicles and roadside infrastructure. A large number of people use the roads at the same time as they travel to and from work and other destinations. Their travel patterns are regular and predictable. Consequently, this provides an opportunity to create virtual communication networks among the travellers or their vehicles (Hua, et al., 2017). Various major automobile manufacturers are already researching how to develop inter-vehicle communication systems and protocols. The development of vehicular social networks is based on the increased use of social networks. Social networks have become an integral part of human life. For instance, millions of people use online social networks such as Facebook and Twitter. These platforms allow people to share information and discuss issues that affect them (Hu et al., 2011). The use of social networks has increased even more due to the creation of mobile social software. This has resulted in a shift of social networks from online to mobile which allows people to interact more through their interconnected mobile devices. Due to the increased social connectivity among people, automobile manufacturers want to take advantage of this development to enhance vehicular communication through vehicular social networks.
Vehicular social networks are aimed to reduce the rate of vehicle collisions by making drivers aware of other motorists as well as help drivers to select better routes. This is achieved through the active periodical beaconing of vehicles on their status (Holzer, Maaroufi and Pierre 2010). These networks facilitate exchange of information among drivers beyond efficiency and safety. They allow drivers of nearby vehicles to socialize. Unlike online social networks and majority of mobile social networks, users in vehicular social networks interact when their vehicles are within communication range physically (Han et al., 2010). Due to the high mobility of vehicles, the interaction among drivers is normally short lived. The network density also changes constantly as vehicles move and out of communication range of each other. The functioning of vehicular social networks can be understood from the interaction between humans and traditional social networks. The relationship between human and traditional social networks normally takes place in three main stages (Leontiadis and Mascolo 2007). These are: creation of a weak connection, cultivation of the weak connection to become strong, and the strong connection is maintained while the weak connection is eliminated. At the first stage, weak connections are developed from existing social networks or communities. If two individuals share a social network or community such as a dancing club, they are likely to establish a connection. People also establish connections with others through other individuals’ existing networks (Hua, et al., 2017). For example, one’s friend might introduce them to other friends. In vehicular social networks, vehicles can connect with others if they encounter then with the communication range on the road and have common interests concerning the shared information. Since vehicular social networks allow vehicles to share information, it implies that it is also possible for them to share their local social connections. It is thereby possible for vehicles to develop virtual connections that would allow them to reach out to their “friends’ friends”. The second stage involves strengthening of the weak connection established in the first stage. This is achieved when people interact and establish a relationship. In vehicular social networks, cultivation of a relationship among vehicles is achieved when two or more vehicles frequently encounter and share information among them (Hu et al., 2011). For instance, vehicles that are constantly parked in the same spot get a chance of developing a relationship with each other. The third stage involves strong relationship established in the second stage being maintained while the weak connections are eliminated. In the case of vehicular social networks, the strong relationship among vehicles is maintained only if they keep sharing information (Hua, et al., 2017). However, connection at each stage is achieved only if two individual desire to enhance their relationship.
A vehicular social network can be developed in distributed or centralized ways. In the distributed way, vehicles share their social connections with other vehicles, which are nearby through DSCRC technology. Sharing of information and social connections with others allows a vehicle to establish its vehicular social network (Leontiadis and Mascolo 2007). The centralized way of developing a vehicular social network involves uploading the social connection among vehicles to Cloud using the existing cellular technologies such as LTE and 3G. A social network is then developed from the collected connections and downloaded by vehicles. While the centralized way of establishing social connections among vehicles is quicker, reliable, and provides real-time solution, it is more expensive as compared to the distributed way since it depends on infrastructures such as Cloud. There are a number of concerns about vehicular social networks. One of them is security and privacy. Security and privacy are among the concerns that have been raised about vehicular social networks. VSNs are constructed on top of vehicular communication (VC) systems and the installation of VSN applications might hamper the security of the VC systems (Hua, et al., 2017). Security and privacy requirements of VSNs vary based on the VSN applications being used. For instance, for a safety application, accountability, integrity, and non-repudiation are important. On the other hand, the traffic management application requires the VSN to not only have a high level of integrity but also be able to verify the content that comes through it. For the entertainment application, service availability is more important. With respect to privacy, there is concern about the confidentiality of the information that vehicles share with each other. Another problem is trust (Hu et al., 2011). VSNs promote interaction among strangers. It is important to note that such individuals may be unwilling to share information because they do not trust the other road users. This might lower the applicability of the VSN thereby reducing its impact in reducing accidents and helping drivers to avoid traffic jams. This research paper is focused on how to enhance trust among vehicles in order to enhance the sharing of information among them.
Take a deeper dive into Exploring Change Resistance in Law Firms with our additional resources.
Research aim
To determine ways in which drivers can be encouraged to trust each so that they can socialize more
Research questions
What are privacy and security issues in VSNs
What are the causes of low level of trust among vehicles which use VSNs
What is the relationship between privacy, security, an trust in VSNs
What strategies can be used to increase trust among VSN users
Literature review
Trust and security of Vehicular Social Networks (VSNs)
The issue of trust has attracted significant attention in the development and use of VSNs. Huang et al (2014) indicates that trust is an important element in VSN. Trust, in the context of VSNs, revolves the relationships that exist among the nodes or participants in the network. Experts and scholars agree that trust is a particularly challenging issue in VSNs. According to Huang et al (2014), modelling trustworthiness among road users in VSNs presents some unique challenges. This is due to a number of reasons. One of them, according to Huang et al (2014), is that vehicles in a vehicular social network are highly dynamic and constantly roam around. For example, the average speed of vehicles on a typical highway is 100km/h. Huang et al (2014) indicates that at such high speeds, reaction to imminent danger is very critical because it determines the ability of a vehicle to avoid being involved in an accident. It is thereby important that the information that one gets is trustworthy and verifiable. However, this is not hard to achieve since there is limited time to verify the information and one has to rely on pure instinct on whether to react to the information received or not. The second challenge is that the number of individuals or vehicles in a VSN can become very large. The number of vehicles in dense urban areas, for instance, is very large. As such, millions of vehicles which pass through a VSN and at any particular moment, thousands of vehicles are present in the network (Minhas, Zhang, Tran and Cohen 2010). The high number of vehicles present in the network makes it hard for drivers to develop trustful relationships with others. This is because one gets a lot of information from different sources making it hard to determine which piece of information one to trust. The situation is worsened during rush hours. During this time, the number of vehicles within a network increase tenfold. This, according to Minhas, Zhang, Tran and Cohen (2010), results in other problems such as network congestion due to information overload. This is because a vehicle will be receiving a lot of information from other vehicles which are within the communication range. Ning et al (2017) points out that at this point, there is need for a vehicle to have an intelligent communication system that is scalable and can identify and respond to potentially hazardous situations which have been reported by other vehicles by deciding, effectively, which peers to communicate with or trust their information. However, this requires additional investment, which can be costly. Since most vehicles do not have these intelligent systems, it has become hard for individuals to trust information that is provided by other motorists, particularly in situations where the information is coming from a large number of peers. Another challenge in developing trust is that VSN is a decentralized and open system. This implies that vehicles may enter and leave the network any time. This implies that if a vehicle interacts with another vehicle now, there is no guarantee that there will be interaction between the two vehicles in future (Zhang 2011). There is so much uncertainty in such an environment that is hard for vehicles to develop trustworthy relationships with each other. On their part, Minhas, Zhang, Tran and Cohen (2010), point to the constantly changing road conditions as one of the reasons why it is hard for trust to be developed among vehicles within a network. For example, a road might be congested but within 5 minutes the congestion ends. Within the five minutes, a vehicle may relay information to other vehicles concerning the state of that road. However, since the situation has changed rapidly, the drivers of the other vehicles may consider this information false or malicious (Wex et al., 2008). In addition, it is hard for the drivers to determine whether this information was true or false. With a significant number of unscrupulous individuals using the roads, it is hard to determine which individual is telling the truth or lying. This challenge brings out another aspect of the information received from a vehicular social network: context. Two context elements which are crucial in a VSN are time and location. Information is relevant only within a particular time and location. For example, using the above case, the information will be relevant only within the first five minutes after which it becomes irrelevant (Zeadall et al., 2012). On the other hand, the congestion may be affecting only a small section of the road. This implies that some vehicles within the communication may not be experiencing a similar situation.
Looking for further insights on Cloud Computing: Growth and Impact? Click here.
Existing trust models
Trust models in VSNs exist in three categories based on the object of consideration. These categories are: entity-based trust models which focus on evaluating the vehicles that send information, data-based trust models which focus on evaluating the data sent by vehicles within a network, and combined trust models which evaluate both the data sent and the vehicles which send the information.
Entity-based trust models
There are two main entity-based trust models. These are multi-faceted trust management model and sociological trust model. The sociological trust model is based on trust and confidence tagging. There are various forms of trust (Pallis et al., 2009). They include: situational trust, which relies on situations only; system trust which is dependent on the system; and dispositional trust which is based on individual beliefs of peers on a vehicular system. The multi-faceted trust management model features in experience-based trust and role-based trust as assessment metrics that are used to determine the trustworthiness of vehicular entities (Yang and Wang 2015). The multi-faceted trust management model allows vehicular entities to seek for information about an event from other entities.
Data-based trust model
The data-based trust model focuses on evaluating the relevance and trustworthiness of data provided by other entities as opposed to evaluating the trustworthiness of the entities themselves. The data-based model was first proposed by Raya et al (2008). In proposing this model, Raya et al (2007) argue that the model is more appropriate for VSNs. In his model, Raya et al (2008) provide various trust metrics that are used to evaluate the trustworthiness of data. Among these metrics is a priori trust relationship among entities. Under the data-based trust model, evidences on an event are evaluated by taking in account various trust metrics that are applicable in the specific vehicular context. Finally, a verdict is passed on whether the reported event occurred or not. The model proposes the use of event or task specific trust metrics and location and time closeness in determining the validity of the data provided concerning an event. One of the limitations of the data-based model proposed by Raya et al (2008) is that it does not allow for the formation of trust relationships among vehicles since trust is based on data only. Another limitation of this model is that it does not promote establishment of long-term relationship. This is because the data evaluated at each moment is limited to one event and cannot be applied to other events. As such, the trust established is short lived. It also implies that each time an event occurs it compels one to analyse the trustworthiness of the data provided. This makes it challenging particularly in situations where there is sparsity of data.
Combined trust model
There are three combined models which have been proposed by different scholars. For example, Dotzer et al (2005) proposed the development of a distributed reputation model which is based on the concept known as opinion piggybacking. Opinion piggybacking involves a situation where individuals who forward information concerning an event provide their own opinion on the trustworthiness of the information. Dotzer et al (2005) offer an algorithm, which enables one to generate a conclusion based on the opinions given by about the data, and other trust metrics, which include sender base reputation, direct and indirect trust, and geo-situation oriented reputation level. The geo-situation oriented reputation level allows the model to have some level of dynamism by taking into consideration the relative location of the individual or node reporting the information as well as the node receiving the information. However, the model has one main problem. It does not provide detailed information about the approach that should be used to analyse the trustworthiness. In addition, the model relies on the opinions given by other nodes. Since it involves nodes also giving their opinions about the accuracy of information, it implies that those who constantly give opinion of data are considered more in future decisions as compared those who have not participated in past evaluation of data. However, just because an individual has taken part in past evaluation exercises do not make them infallible. They are likely to make mistakes. In addition, an individual might provide their assessment based on their proximity of to the event.
Empirical studies
There are a limited number of empirical studies that are focused on the issue of trust in vehicular social networks. This could be due to the limited application of the concept in the practical sense. However, there are a significant number of studies, which have been carried out on ordinary social networks. For example, in their study, Ziegler and Golbeck (2007) established that there is a strong relationship between users’ interest and trust. The data used in this study was obtained from to online communities, FilmTrust and All Consuming. For each dataset, the interest profile of a user was constructed from how they rated corresponding items such as movies or books. Ziegler and Golbeck (2007) then used the interest profiles to calculate the similarities that existed between different users. Lastly, the profile similarity was then used to measure the level of trust between two users. Users who were more similar were considered to have a higher level of trust in each other. The study by Ziegler and Golbeck (2007) provides insight on how profile interest can be used to determine the trust level among individual. However, it does not provide empirical evidence to indicate that trust level among the different users. Profile similarity and trust are two different variables and one does not necessarily denote. It is possible for people to have a high profile similarity without necessarily trusting each other. For, on social network platforms, people are likely to indicate that they like a particular book or movie yet they are not friends on that platform. This may occur when people belong to the same group on Facebook or any other social media platform. Such individuals may have minimal interaction on a personal level. Apart from user interest similarity, user interactions are also another parameter, which has been used to measure the level of trust among social network users. For example, in their study, Gilbert and Karahalios (2009) asked 35 individuals to rate how much they trust their Facebook friends. Gilbert and Karahalios (2009) then collected 74 Facebook variables for each participant and then used them to determine the trustworthiness the participants’ friends as perceived by the participants. They established that a higher level of interaction resulted in increased level of trust. The study by Gilbert and Karahalios (2009) provides insight into the role played by interaction in developing trust. The study shows that when people interact more they become more trusting of each other. This is because increased interaction allows people to learn more about each other. Learning about each other makes people to discard the misconceptions that they had before. The studies on trust in ordinary social networks show that it is possible to develop trust from the similarities and interactions among drivers in a vehicular social network. However, it is hard for trust to be established in VSNs using profile similarities since it is only messages, which are shared among drivers. VSNs do not provide an avenue for drivers to learn about their similarities. However, it is possible for trust in VSNs to be developed through increased interaction. When motorists interact more, they become more trusting. But this is challenging because of the dynamism of VSNs. As pointed out before, there is limited interaction among drivers because of movement. An interaction between two vehicles is unlikely to be repeated unless the drivers live or work in the same locality.

Broadly, VSNs are a new concept that has limited empirical research. The current literature is mainly theoretical. As indicated before, it is mostly because of limited practical application of the VSNs. Nonetheless, there is a consensus among scholars that trust is a significant challenge that is likely to hamper the practical application of VSNs. With cyberterrorism being rampant, it is highly possible that people are unlikely to trust others. The limited interaction among vehicles does not help in enhancing trust among drivers.
Privacy and security in VSNs
Apart from trust, there are privacy security concerns in VSNs. According to Minhas, Zhang, Tran and Cohen (2010), privacy and security of VSNs are among the factors which influence how peers in VSNs trust each other. Minhas, Zhang, Tran and Cohen (2010), highlights various security and privacy requirements. These include: authentication and integrity, confidentiality, accountability and non-repudiation, unlinkability and anonymity, access control, and availability. Minhas, Zhang, Tran and Cohen (2010) indicate that a node in a VSN should have the ability to authenticate the information source. Only information that comes from a trusted source should be accepted and acted upon. In addition, VSNs should be designed in such a way that it is not possible for information to be altered. The ability of authenticate the source of information is aimed to increase the level of trust among peers in a VSN. However, it should be noted that unless a system is developed that automatically verifies the authenticity of the information, then it is can be hard for peers to determine whether the information they have been provided with comes from a reputable source. The idea behind VSNs is that users eventually learn to trust each other due to constant interaction among them. However, since the likelihood of motorists constantly interacting with each through VSN is low, it is hard for one to determine whether other peers in the VSN are authentic. Zhang (2011) also indicates that information exchanged among users should be done confidentially. For example, the VSN should be designed in such a way that particular information is accessible by vehicles in a platoon or from a similar manufacturer. However, there is other information that can be broadcasted since it is not confidential. Such information includes traffic conditions on a particular road. With regard to accountability and non-repudiation, Abbani et al (2011) indicates that entities within a VSN which include vehicles, infrastructures, and smartphones need to be accountable for their actions in the system and it should not be possible for them to deny those actions. This will ensure that drivers do not engage in malicious activities by providing false information to other peers in the VSN. Unlink ability and anonymity involves making sure that user identities are not exposed. According to Ning et al (2017), there should be no link between messages and users. However, there is a problem with this condition in sense that it provides license to users to abuse this privilege. As pointed out, there is need for peers in a VSN to be accountable for their actions. This means that they need to be accountable for the messages they send to other peers in the network. Such accountability cannot be achieved if the messages sent cannot to be linked to the sources. This means that in order to ensure accountability, there should be conditional anonymity. The anonymity of a user should only be respected if they do not misbehave. If a user sends a wrong message to other peers in the network, then they should be held accountable by having their identity exposed. Wex et al (2008) also provide that a VSN should only be accessible to legitimate entities that are registered within the system. The social network system should be able to prevent illegitimate entities from taking part of the system operations. In VSNs, interactions among users could also be restricted depending on the relationships they share. For example, sharing of messages can be restricted to individuals who are considered friends in the system. However, this is a number challenging aspect to accomplish considering that the interaction among peers in a network is temporal and unlikely to be repeated unless of course there is some level of consistency in the way peers travel. The short lived nature of the interaction among peers in a vehicular social network makes it hard for individuals to develop lasting relationships. To ensure that this requirement is achieved, it means there is need to design a VSN in such a way that it incorporates only those drivers who use similar routes. Still that is hard to achieve in a practical sense. This is particularly with regard to cities where there are a high number of vehicles from different directions. The level of interaction among vehicles in such places is short lived and unlikely to be repeated in the near future. Access control is thereby a significantly hard requirement to achieve in dynamic environments such as town and cities.
With regard to availability, Zeadall et al (2012) indicates that vehicular social networks need to remain operational even in cases where there faults in the system. One of the main aspects of the network that should not be hampered by faults is the functionality of its underlying network architecture, that is, traffic efficiency and user safety. There are a number of ways in which the privacy and security of a VSN can be hampered. They include honest but curious entities, malicious participants, and selfish participants.
Honest but curious entities
Research on mobile applications such as LBSs indicates that service providers normally collect user information so that they profile users. For instance, an LBS server may collect user questions, which include locations, and user interests so that they can be able to provide customized services or design advertisements that fit a particular group of users. However, this has raised questions concerning users’ privacy (Ucar, Ergen and Ozkasap 2013). A number of individuals have raised concern, indicating that collecting of such information amounts to infringement of user privacy and jeopardizes the security of users since unauthorised individuals who, in turn, might use it to hurt users can access such information. Zhang, Boukerche and Pazzi (2011) agree with this assertion indicating that collection of user information does not only result in infringement of their privacy but also puts their security at a risk. According to Zhang, Boukerche and Pazzi (2011), this concern is also applicable to the VSN. This is because in order to profile users, there is need to seek for their private information such as location and interests. The study indicates that many organizations attempt to resolve this problem by using a Trusted Third Party (TTP). A TTP is proxy, which is introduced between users and the honest but curious entities. As such, the proxy anonymizes any request by a user before it can be forward to an entity. However, according to Wisitpongphan et al (2007), even with the introduction of a proxy, the same concern persists. Essentially, since the information that passes through the proxy is transferred wholly to the entity, then it means that entities can easily infer more information from the one that is provided. As such, it can be hard to maintain the privacy and security of users’ information.
Malicious participants
Because of the dynamic nature of VSNs, legitimate users and registered vehicles can easily disseminate faulty information thereby affecting the process. Malicious participants might also decide to pollute the information received from the provider before sharing it with others. The openness of data sharing in VSNs results in additional vulnerabilities as compared to traditional social networks. The situation can easily be exacerbated with the increased use of fake identities among users. A user with multiple fake identities can decide to sabotage the system by using all the fake identities at the same time. This can create chaos within a VSN. The use of fake identities also makes it hard to expel malicious participants since they can easily clone other identities that would allow them to continue with their malicious activities.
Selfish participants
Apart from malicious participants, there is also the case of selfish participants. Mobile applications, which are based on crowdsourcing, have been used widely to enhance safety and efficiency in transportation. These applications depend on the participation of users to measure certain phenomena such as traffic status. However, the applications cannot work without the active contribution and participation of users. In VSNs, selfish users are likely to use information from other nodes to achieve better services and then choose not share the information with others. Like any other crowdsourcing based application, VSNs rely on the participation of users and having selfish individuals in the system is will be make the networks inefficient.
The relationship between privacy, security and trust in VSNs
There is a significant relationship between privacy, security, and trust among VSN users. In their study, Vegni and Loscri (2015) established that security and privacy concerns have made users to be wary of using VSNs or sharing information one they are in the system. This situation has been exacerbated by the increased cases of malicious participants. The sharing of false information has made many drivers to have unpleasant experiences making them less trustful of the VSNs. The increased cases of malicious participants have also reduced the reputation of VSNs. The reputation of VSNs are systems which can help drivers avoid accidents and traffic jams has reduced significantly because malicious participants provide false information to other users which, in turn, make them to have poor experiences within the network. This has made hard for users to trust the system and its users (Taleb et al., 2007). This has also negatively affected the ability of the system to help in the development of relationships among users. This is because while a user might belong to a particular group, it hard for them to determine which user is using a fake identity and which one is genuine. The situation is made worse by the inability of users to verify how genuine others are. This has reduced the level trust among users. Essentially, the vulnerability of VSNs particularly to internal manipulation has made it hard for users to trust the networks and others users. This has made individuals to avoid using the systems altogether or avoid sharing information when they are in the system. The case of selfish users has, on the other hand, made VSNs to be ineffective. This has also played a significant role in reducing the level of trust among the users in the system as well as other users.
Desired trust management for VSNs
Due to the challenges faced by VSNs particularly with regard to enhancing the level of trust among users, various scholars have proposed a number of ways in which the trust level can be improved (Sha, Kwak, Nath and Iftode 2013). Some of the ways include decentralized trust establishment, coping with sparsity, focus on event, task, location, or time specific, scalability, system level security, and sensitive to privacy concerns.
Decentralized trust establishment
Trust establishment needs to be decentralized fully so that it can be easy to apply it the VSN environment, which is highly distributed and dynamic. Majority of trust models use the direct interactions among peers in a VSN as the only way to form lasting relationships and thereby trustworthiness among them. However, as pointed before, such level of interaction as proposed in the models is not achievable in the dynamic and highly distributed VSN environment (Ramdhany, Grace, Coulson and Hutchison, 2009). Other models also require peers in the VSN to determine the reputation of other users or at least the information provided by these users by seeking the opinions of other users about the source of the information. However, a user may not have knowledge about whether peers have interacted with the peer that they seek opinions about since the VSN is not a centralized system (Maaroufi and Pierre 2015). Decentralization will allow the formation of groups not based on location but particular roles assigned to users. The roles will require users to adhere to particular policies. This will ensure that they users cannot provide false information or even use false identities. Decentralization will also enable users to trust information provided by peers that they do not interact with frequently.
Coping with sparsity
Sparsity of information is also another trust concern. Many trust models require users to trust information, which has been provided and verified by many peers. However, this is not always achievable due to sparsity of information. To deal with the challenge Zhang (2011) proposes that trust establishment should not be based on a particular minimum interactions threshold. Instead, focus should be shifted to role-based trust approaches where trustworthy users are distinguished from the untrustworthy ones. Zhang (2011) also proposes that users should be allowed to send testing requests to determine the peers that are trustworthy and those who are not. This way, a trustworthy relationship can be formed among a group of peers.
Event, task, location, or time specific
Since the VSN environment is constantly changing, Zhang (2011) proposes that there is need to introduce trust metrics that take into consideration this dynamism. This will allow peers in a VSN to determine which users or information to trust depending on the situation. For example, some situations might be time sensitive that implies that a peer may be needed to react quickly. In such a situation, it can be hard for the peer to consult many users to determine whether the information they have been given is accurate or not. Zhang (2011) proposes that there should thereby be other parameters that can be used to determine whether to trust the information. For instance, information concerning life-critical events is unlikely to be false and peers should take them on the face value.
Scalability
Scalability is a crucial aspect of trust management within the VSN environment. In a dense VSN environment, the amount of information that may be passing through a system is high. This makes it hard for peers to determine which information to trust and which one not. According to Zhang (2011), it is important for peers to be able to scale information provided to determine which one to trust and which one not. For example, peers need to be allowed to keep history of their previous interactions so that they can be able to filter information quickly and act on the one they consider trustworthy.
System level security
As pointed out security is one of the factors that affect the level of trust among peers. To deal with this problem, Zhang (2011) proposes that security mechanisms should incorporated in VSNs to make sure that peers authenticate themselves before they can be accepted in the network. , Zhang (2011) also proposes the use of public key certificates and encryption to authenticate peers and make them more accountable. This will reduce the use of fake identities.
Sensitive to privacy concerns
Privacy is a big concern in the VSN environment. It is also among the main causes of lack of trust among users. To deal with this concern, Zhang (2011) proposes the use of a PKI (public key infrastructure). According to Zhang (2011), PKI allows a user to prove they are authentic without necessarily revealing personal information about themselves. PKIs do not contain sensitive information about user identities yet they allow a user to track the sender of information by using the sender’s key. This will help lower cases of false of identities increasing the security but at the same time enhance privacy of users.
Summary
The issue of trust has attracted significant attention in the development and use of VSNs. Some of the factors which influence trust include: privacy and security concerns, dynamism of the VSNs which makes it hard for peers to develop lasting relationships, and cases of malicious participants who provide false information. Trust models in VSNs exist in three categories based on the object of consideration. These categories are: entity-based trust models which focus on evaluating the vehicles that send information, data-based trust models which focus on evaluating the data sent by vehicles within a network, and combined trust models which evaluate both the data sent and the vehicles which send the information. Some of the trust management solutions that have been proposed include: improvement of security by using public key certificates and encryptions, enhancing privacy by introducing KPI, and decentralizing trust management.
3.0 Methodology
3.1 Research Methodologies
The distribution/buy in the show is alluring for VSNs because of its normal match of unknown correspondence. In this model, messages are distributed in view of the idea of their substance as opposed to route to particular recipients. Utilizing the Bar/Sub worldview, workers can distribute their messages and every single intrigued collector buy into the distributed Without the knowledge. Existing systems, Pervaho and LMA have abused area data in their proposed distribute/buy in deliberations to fabricate a few setting mindful applications. In addition, regularly add the likelihood to restrain the dissemination of messages in a specific geological territory. Nevertheless, they do not permit to distribute dynamic substance and just permit a few sorts of dynamic area based separating. In addition, they need productive and solid correspondence conventions ready to limit the overhead of the dispersed distributions/memberships. We contend that these works give an establishment to building a specific kind of distribute/ buy in reflections ready to incorporate the dynamic idea of the common data as well as the relevant data of senders and collectors with a specific end goal to facilitate the improvement of setting mindful applications that are workers'- situated. To defeat the last weaknesses, we present a dynamic informing reflection through the Dynamic Distribute/Buy in Administration (DPSS) is the focal point of the Dynamic Informing Framework (DYMES). It permits to break the worker's social disconnection out by permitting them to distribute dynamic setting and to buy in utilizing on the web setting mindful message channels. This part is sorted out as taken after. To start with, we display DPSS, we examine its Programming interface and we exhibit an arrangement of related APIs. We delineate and demonstrate their use by means of two commonplace vehicular applications. At that point, we recognize and talk about execution issues that guide the engineering decisions of DYMES. The third commitment of this proposition was a Portable Door Disclosure and Determination Technique that handled the issue of the colossal data transfer capacity utilization in vehicular systems and the critical need of suburbanites to control, all the while, the current condition of their busy drive. MGDSS depended on the result of the second commitment (DPSCS) and permits suburbanites bunched in networks to helpfully and productively control the present condition of the activation conditions and to associate with the Web. To do as such, MGDSS utilizes a proficient and solid Portable Passage Disclosure Component (MGDM) that depends on a novel setting mindful Coding Administration. The last permits every suburbanite to investigate productively and dependably its neighbourhood by communicating its relevant data utilizing a solitary message, and without flooding the system with control messages. MGDSS permits hubs grouped in congested drives to speak with the foundation, at the same time, upon the finish of the disclosure procedure. To do as such, it utilizes a Versatile Portal Determination Instrument (MGSM) that enables hubs to choose a base number of focal stable doors in view of the hubs' data they got amid the revelation methodology (MGDM). They at that point set up an association with the base station. The entryway advances the got messages/inquiries to the base station. To conquer these difficulties, we introduce a dynamic informing framework for vehicular social systems known as DYMES. The objective of our proposed engineering is to advance ongoing social associations among suburbanites amid their roadway goes through proficient and dependable disseminated and unified vehicular correspondence deliberations. DYMES adapts to the workers' namelessness in very thick systems through a Dynamic Distribute/Buy in Grouping Technique (DPSCS). It enables every worker to make its own steady and self-refreshed vehicular network via a multicast of the solitary and determined message while guaranteeing high effectiveness and dependability all through thick dispersed systems. DYMES manages the shortage of the radio assets in thick vehicular systems, the suburbanites' discontinuous network, and the broad transmission capacity utilization in infrastructure-based vehicular systems, through the presentation of a helpful and effective Versatile Portal Revelation/Determination Technique (MGDSS). The last gives every worker an opportunity to be educated about constant movement conditions and to choose a base number of versatile portals keeping in mind the end goal to guarantee an effective and dependable network with the foundation. The principal contrast between our agreeable portable door revelation/determination techniques, what's more, the current ones, is that all vehicles can control the current condition of their congested drive in the meantime. In addition, the dominant part of vehicles can get to the foundation, at the same time, without demanding any stern manipulation and control over the data, and without holding up to get answers from an officially characterized group head. Setting up a steady course to associate vehicles with the framework has been generally examined in the writing. The objective was to enable clients to download records from the Web, which is like conventional vehicular applications, for example, the GPS which associates with the server keeping in mind the end goal to give data to singular clients. Be that as it may since workers have regular interests and inclinations on parkway trips, they are enthusiastic to share/get dynamic logical data from different clients, which requires specific correspondence reflections. DYMES meets the prerequisites of suburbanites out and about and proposes a novel web-based coordinating methodology that goes for sending the workers' productions, what's more, memberships to the foundation through the chose portable door. Our on the web coordinating procedure goes for refreshing the workers' memberships and at sending the matches to the comparing clients through stable remote connections. The following test that DYMES manages is when suburbanites begin losing their remote network with their current chose portable passage. Right now, workers dispatch a proficient and solid handover component that comprises in rediscovering their new neighbourhood making sure the destination is to bifurcate another versatile entryway. The rest of this section is sorted out as takes after. Area 5.1 presents DYMES engineering, clarifies its working and subtle elements the calculations related to the proposed methodologies. Area 5.2 presents the reproduction brings about terms of unwavering quality and proficiency. Area 5.3 closes and calls attention to some future research bearings.
Proposed Dynamic Informing Design
The topology of our proposed dynamic informing design is the cross breed. The system situation thinks about three kinds of hub: normal vehicles chose versatile passages, which are going in separate two ways. GPS gadgets enabling them to acquire their areas, velocities, and bearings outfit machines. Vehicles speak to each other via V2V correspondences, they additionally convey with the foundation through chose versatile doors (V2I). By a connection, we mean an immediate connection between neighbouring vehicles, while, a course is made out of numerous connections between n vehicles. DYMES engineering that is essentially made out of two modules: the Dynamic Distribute/Buy in Bunching Technique (DPSCS) and the Versatile Door Disclosure/ Determination Technique (MGDSS).
4.0 Discussion/Analysis
Dynamic bunching in crossbreed VSNs: The past work thought that grouping is an essential system administration assignment for vehicular systems since it decreases communicate storms and enhances the handing-off of messages. Anyway, the primary testing issue in vehicle grouping is the regular topology changes. Consequently, correspondence deliberations ought to consider the dynamic idea of the common data in the outline of proficient, steady, and dynamic bunching methodologies (Nohuddin, Coenen, and Christley, 2016). Besides, existing examination works just handled the issue of workers' obscurity and their need to associate without itemizing the working of their hidden correspondence conventions. The last should consider the heterogeneous nature of vehicular systems and ought to likewise guarantee a private data sharing among clients out and about (Palazzi, Roccetti, and Ferretti, 2010). We add to the current group of research by giving a novel online distribute/buy in gathering technique that depends on a productive, solid and stable multicasting convention and that goes for building trustworthy and independently updated vehicular social networks at low expenses while protecting the namelessness of the suburbanites' characters and the security of their common data. Portable entryway administration calculations in half breed VSNs: Existing exploration works presented a VANET-3G design and a middleware for portable setting mindful applications, called Pervaho (O’Loughlin, and Payne, 2014). Messages are aimlessly sent among drivers amid the CH choice and the portal revelation/ ad components (Ranganathan et al., 2004). This activity may surge the system when numerous source vehicles want to speak with the foundation in the meantime. Additionally, Pervaho (Palazzi, et al., 2007) does not take care of the investment of customer/server interchanges while sending productions and memberships to the server. Since this cost incites an enormous transmission capacity utilization contrasted and the cost of promotion hoc interchanges, distributors and endorsers would rather need to join their messages in a specially appointed manner and send them by a base number of clients to the framework. We trust that the proposed approaches require to be consolidated in a complete middleware that permits to switch between systems administration methodologies in view of system design and on driver conduct forecasts for specific online social application situations (Paruchuri, Durresi, and Jain, 2003). To the best of our insight, regardless it appears to be difficult to give one-fits-all arrangement capable of spreading over the entire range of vehicular social frameworks. Truth be told, existing vehicular social systems are either intended for disseminated vehicular systems or concentrated ones (Ramdhany, Grace, Coulson, and Hutchison, 2009). Crossbreed vehicular social systems are not yet accessible in the writing. We add to the current assortment of research by giving DYMES, a cross breed and dynamic setting mindful informing engineering that goes for empowering ongoing social connections among workers in the mixture and thick situations (Peng, Wang, and Xie, 2017). We centre on amplifying the productivity (limit the message overhead) and the message conveyance (unwavering quality), through circulated and incorporated vehicular correspondence reflections.
4.1 Technology and standard process
To execute any project, there is a development phase where comfortable and trustworthy software and technology are used in order to get the best output of the system. A programming language is used depending on the objective and type of project. If it is a mobile application project, there would be android, if it is a web application or website, PHP, HTML and JavaScript are utilized for the best performance of the project. Vehicular Social Network that provides a seamless communication between the commuters. Hence, there is a need to develop a robust and scalable network in order to install a foundation of such a project. Such a network will allow the users to be able to present in the active network and interact with other users who are present in the same network at the same time. The idea here is to develop a secure and seamless network where people can interact and engage in a productive environment. While traveling, many issues and parameters should be covered in order to ensure an enjoyable and pleasant travel. At that time, if the traveller is connected with such a network community through a robust network, it will give the traveller a good travel experience at the end. With that being said, we will use C++ language here for the development of the project. However, C++ language is not robust enough on its own to provide modules and libraries for sustaining network requirements. There is a requirement of a network simulator in order to develop the software further. OMNeT++ is the network simulator used in this project. OMNeT++ is known as the Objective Modular Network Tested in C++. This simulator is a modular and component-based C++ framework and library file that provides the network simulation procedures. Furthermore, it also provides security measures that can be developed using C++. As introduced amid the writing survey in part 2, a few research works advocate the plan of a dynamic informing framework ready to fulfil the online suburbanites' prerequisite as far as empowering social cooperation out and about by advancing the advancement of user-oriented vehicular social applications and administrations. Truth be told, suburbanites are obscure and unknown to each other and are here and there reluctant about uncovering their private data openly. The last is one of the numerous different reasons that obliges and restrains their social cooperation out.
4.2 General Structures of Vehicular Social Network
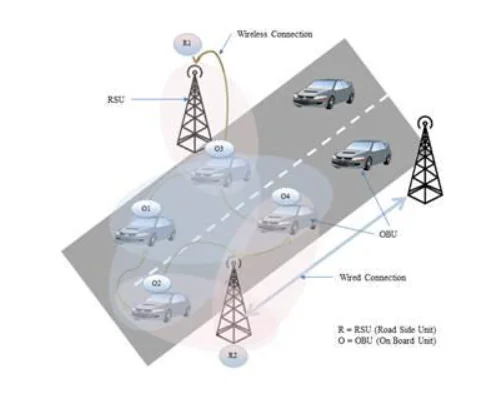
The vehicular social network is not similar to another social network that we used in our day to day lives. They have their own independent hardware and software assistance in order to execute the tasks. As mentioned in the figure above, there are basically two elements that would provide the gateway to the users and the network. One is Road Side Unit and the other one is On Board Unit. The roadside unit is considered to be large towers similar to electrical towers that we see in the roadside. These towers are the standalone routers that will not only provide the medium for the users but pass the necessary information for the users to the cloud and service provider in order to generate a flawless communication medium. The information of any user is saved in a cloud storage that is synchronized with Road Side Units and On-Board Units. Thanks to these Road Side Unit, whenever a user (a vehicle) joins the traffic and connects to the network. Its identity is authenticated. The vehicle which joined the traffic has an onboard unit which has basic information about the user. It has the IP address, location, identity of the user, etc. It also has the location tracker and might have the knowledge of where the user is heading in his journey. Now, there are other vehicles too with an independent onboard unit with the same information as rest of the else. These onboard units are connected with the roadside unit and share the information with the system. Therefore, the network knows how many people are headed to which destination and they are accompanied with how many people. The network also knows the purpose of the visit and type of vehicle through which the travellers are commuting. They know if there is an SUV, LMV, Van, Truck or a Bus. Thanks to everyone being connected with roadside units, that unit in return provide the data to the every on-board units on the road regarding the traffic. They can calculate the overall time to reach the destination, who are the other co-travellers are visiting which particular destination For example, if I am visiting Chicago from Michigan, I would know which other commuters are visiting the same destination with me. Moreover, if I came to know there are few individuals who are visiting the same place, I can connect with them, talk with them, network with them and create meaningful connections. Hence, the idea here is to get to know other people, build a trustworthy community. In addition, these onboard units are highly developed and rigorously made that can help its users the traffic analysis. They not only provide the best path but also make the users aware if there is a congestion ahead or a threat full collision happened in the next turn. What this would do is make people realize which road not to take or where to be more careful based on the traffic and accident analysis. People can talk to each other. However, the major concerns here is the security as people are sharing sensitive information with the network, which should not be breached at any cost. The attacker would have complete control of the traffic through those numbers and analysis, might manipulate the traffic, and measured anything to create a jeopardy in the system.
5. Protocol
This paper needs to use the following protocols to secure, Privacy and Trust Framework for Vehicular Social Network. These are,
Communication Protocols
Broadcasting Protocols
Counter based protocols
Address based Protocols
Network coding aided broadcasting protocols
Standards that Govern Communications:
All correspondence, regardless of whether up close and personal or over a Network, is administered by foreordained tenets called conventions. These conventions are particular to the qualities of the discussion. In our everyday individual correspondence, the principles we use to convey more than one medium, similar to a phone call, are not similar to conventions for utilizing the other medium. For example, letter sending. Consider what number of various standards or conventions oversees all the distinctive techniques for correspondence that exist on the planet today. Effective correspondence between contains the Network which needs connection of various conventions. Gathering of between related conventions that are important to play out correspondence work is known as a convention suite. These conventions are actualized in the programming and equipment, which are stacked on each host and Network device. Outstanding amongst other approaches to envision how the majority of the conventions interface on the specific host for viewing as the stack. The convention stack demonstrates how an individual convention inside the suite is actualized on the host. Conventions are seen as layered chain of command, where each one has more elevated amount of benefit contingent upon the usefulness characterized by the conventions appeared in the lower levels. Stack’s lower layers are worried about moving information over the Network, then for the upper layers it gives administration. These layers are meddled on the substance of the message that is being sent and the UI.
Utilizing layers for depicting up close and personal correspondence
For instance, consider two individuals conveying up close and personal. As illustrated in the figure, it is possible to utilize 3 layers for depicting this movement. The physical layer, at the base layer contains a couple of individuals, where each one has a voice which could express the words, so anyone might hear. Then, at the next layer, the tenets layer, contains a consent for talking about the typical dialect. Whereas, at the layer which is best, the substance layer, the words really talked on the correspondence. If the discussion is observed, it is noted that we will not really observe the "layers" skimming in the space. It must be understood that the utilization of layers refers to a model and, all things are considered. It provides an approach for helpfully breaking the perplexing assignment into the parts and depicts how the function actually takes place.
Protocols of the Network
At human level, certain correspondence rules are considered as formal and the others are just comprehended, or certain, in view of custom and practice. For the devices to effectively impart, the Network convention suite has to portray exact necessities as well as the collaborations. Networks administration convention suites depict procedures, for example,
The organization or the message’s structure.
Strategy that organizes the devices shares the data related to the pathways with different Networks.
When and how the blunder and the framework messages are passed among the devices.
The information’s setup and end exchange sessions.
Singular conventions in a convention suite might be merchant particular and exclusive. Restrictive, in such a unique situation, implies the one organization or the merchant controls which shows the meaning of the convention and it capacities. Various associations with authorization from the proprietor could utilize certain restrictive conventions. The others must be actualized on hardware fabricated by an exclusive seller.
Protocol design
A->B: Enc(m; K_B), Sign(m; k_A)
A->B: Enc(m; K_B), Sign(H(m); k_A)
SO/IEC 11770-3 Key Transport Mechanism 2:
A -> B: B, tA,Enc(A,kAB; K_B),Sign(B, tA, Enc(A,kAB; K_B); k_A)
A ->B:Enc(A,B,kAB,tA,Sign(A,B,kAB,tA;k_A;K_B)
The Protocols’ Interaction
A case of utilization of the convention suite in an arranged correspondence refers to a collaboration between the web server and the internet browser. Such an association utilizes various conventions and gauges during the time spent trading data between them. The diverse conventions cooperate to guarantee that the messages are gotten and comprehended by the two gatherings. Precedents of such conventions include:
Application Protocol
The Hypertext Transfer Protocol (HTTP) denotes the typical convention, which oversees the method that the web server and the web client cooperates. The HTTP characterizes the substances and arranges the solicitations and reactions traded between the client and the server. The client and the web server programming actualize the HTTP as a major aspect of the application. HTTP convention depends on the different conventions for overseeing the process of transporting the messages between the client and the server.
Transport Protocol
The Transmission Control Protocol (TCP) refers to a vehicle convention, which deals with individual discussions between the web server and the web client. The TCP isolates the messages of HTTP into smaller parts known as sections, for sending it to the client’s destination. Likewise, it is in-charge to control the rate and the size, at which the messages are traded between the client and the server.
Internetwork Protocol
The Internet Protocol (IP) is the well-known internetwork convention. It is in-charge to take the designed sections from the TCP, typifying them into bundles, appointing the fitting addresses. Then it chooses the best way for meeting the destination.
Network Access Protocols
Network get to conventions portrays a couple of important capacities as follows, the administration of information interface and on the media the information’s physical transmission. From the IP, the Information interface administration convention take the parcels and arranges them to be transmitted over the media. Norms and conventions for the physical media administer how the signs are sent over the media and how they are deciphered by the accepting clients. For the media, on the Network interface cards, the handsets execute proper norms which are being utilized.
Communication Process
TCP/IP display depicts the usefulness of conventions, which makes TCP/IP convention suite. Such conventions are actualized on both sending the host and for accepting the hosts, then it collaborates to give end-to-end conveyance of the uses over the Network.
An entire correspondence process incorporates which means the following:
At the application layer, the Information production, the starting source of the end device.
Division and exemplification of information as it goes down the convention stack in the source end device.
At the Network, the information’s Age on the media gets to the stack layer.
The information transportation via, internetwork comprises of media and any go-between devices.
Information gathering at the Network gets to the destination layer of the end device.
De-capsulation and reassembly of the information as it leaves behind the stack in the destination device
Passing this information to the destination application at the Application layer of the destination end device
While the system’s messages are being sent, the convention stack on a host’s work starts to finish it. In the web server precedent, the TCP/IP model is utilized for showing the way toward sending the HTML page to the client. Application layer convention, HTTP, starts the procedure by conveying the HTML arranged site page information to the Transport layer. There, the application information is split into the TCP portions. Every TCP section is provided a mark known as, header, where it contains the data of which is the running process on the destination PC that must receive the message. It likewise contains the data to empower the destination procedure to reassemble the information back to its unique arrangement. The Transport layer exemplifies the site page HTML information inside the fragment and sends it to the Internet layer, where the IP convention is executed. Here the whole TCP section is epitomized inside an IP bundle, which includes another mark, called the IP header. The IP header contains source and destination have IP addresses, and also data important to convey the bundle to its relating destination process. Next, the IP parcel is sent to the Network Access layer Ethernet convention where it is exemplified inside a casing header and trailer. Each casing header contains a source and destination physical address. The physical address interestingly distinguishes the devices on the neighbourhood arrange. The trailer contains mistake-checking data. Lastly, the bits are encoded onto the Ethernet media by the server NIC.
5.1 TYPES OF ATTACK:
Here I had discussed about the different types attack could possible in the Vehicular social network and also protocols to stop those attacks.
Replay attack
A replay assault happens when an aggressor duplicates a flood of messages between two gatherings and replays the stream to at least one of the gatherings. Except if moderated, the PCs subject to the assault will process the stream as authentic messages, bringing about a scope of awful outcomes, for example, excess requests of a thing. Replay assaults are utilized for access or change assaults. This can likewise happen security testaments from frameworks, for example, Kerberos. The assailant resubmits the endorsement, wanting to be approved by the confirmation framework, and go around whenever affectability.
V1= Vehicle1
V2= Vehicle2
Here, when two vehicles in the road communicate between them to share their location.
V1V2: HI
V2V1: Hello
V1 V2: (REQUEST LOCATION, Kv1, v2) (Vehicle1 request vehicle2’s location with their public key)
V2V1: ENC (LOCATION, V1), Kv1, v2) (Vehicle2 replay encrypted location with the public key)
In this situation replay could be possible, because the attackers could send the previous shared location to the Vehicle1 to misguide.
To avoid replay attack in this situation N random number can use. Random number is used to prove the freshness of the message.
V2 V1: SIGN (LOCATION, NV2) Kv1, v2)
Here V1 to checks the message is new or old, if it is new the Vehicle1 can trust the Vehicle2).
Man in middle attack
A man-in-the-middle assault is a sort of digital assault where a noxious on-screen character embeds herself into a discussion between two gatherings, imitates the two gatherings and accesses data that the two gatherings were attempting to send to one another. A man-in-the-middle assault enables a malignant on-screen character to capture, send and get information implied for another person, or not intended to be sent by any means, without either outside gathering knowing until the point that it is past the point of no return.
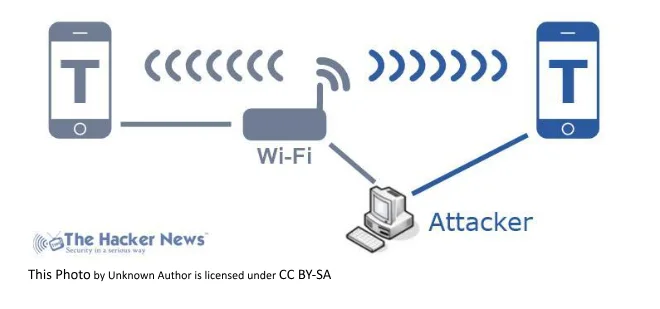
A MITM assault happens when a correspondence between two frameworks is blocked by an outside element. This can occur in any type of online correspondence, for example, email, internet-based life, web surfing, and so forth. In addition to the fact that they are attempting to listen in on your private discussions, they can likewise focus on all the data inside your gadgets.
Assume that two cars waiting in the exit of the car parking to pay the parking fee.
PS = Parking server
PS V1: (Parking Receipt, Requesting card details, Nps) V1. (Here parking server send the receipt of v1 and requesting for card details with random number)
V1 V2: (Parking Receipt, Requesting card details) V2. (V1 sends the same request to V2)
V2 Ps :( card details, V2, NV2) Kv1, Ps).
After this parking server charge the vehicle2 user card and let the Vehicle1 to go out. Even though the receipt is send with Random number, still Nonce is vulnerable to the Man in the middle attack. Therefore, to avoid this Timestamp is one of the best option available. The freshness of the message is shielded better than Nonces. V2PS: ENC ((Card details, V2, T) (KPs, V2) (V2 ID is sending to avoid reflection attack) The parking server will set some time for response, If the Timestamp is more the threshold time the sever will ignore the message.
Reflection attack
Reflection assault is a technique for assaulting a test reaction verification framework that uses a similar convention in the two bearings. That is, a similar test reaction convention is utilized by each side to confirm the opposite side. The basic thought of the assault is to trap the objective into giving the solution to its very own test. In a road when a vehicle wants to connect to another vehicle in the road to know the traffic information, during that the attacker can intercept the connection and start communicating with the vehicle in the name of another vehicle to misuse them.
V1V2:V1 (HI) (Attacker intercept the connection)
AV1:V2(HELLO)
V1V2: Nv1
AV1:Nv2
V1 ENC (Nv1, Kv1, v2)
A ENC (Nv2, Kv1, v2)
Here v1 believes attacker is V2 and start communicating with that and attacker can get the information which it wants from V1. To avoid this attack, need protocol used in both the direction, should not the one used in same way. Here it will be solved by adding the vehicle Id.
V1 ENC ((V1 Nv1) (Kv1,v2) ( Vehicle1 shares its ID)
A ENC (V1,Nv2, Kv1,v2) (Attacker replied with same ID)
So, V1 decrypt the message and it will find out its own ID in it and it will stop the connection. This how connection will be secured against Reflection Attack.
Impersonation attack
Impersonation assaults are propelled by utilizing other hub's character, for example, MAC or IP address. Impersonation assaults in some cases are the initial step for most assaults, and are utilized to dispatch further, more advanced assaults. In all actuality remote systems need proper security framework and give potential assailants simple transport medium access. Maverick remote passageways merit specific consideration since they are not approved for activity. They are normally introduced either by representatives or by programmers. Consideration has been paid to discovering mavericks by utilizing: Wireless sniffing instruments, strolling through offices and searching for passages that have approved Medium Access Control (MAC) addresses, seller name, or security design. A focal comfort joined to the wired side of the system for observing, a free Transmission Control Protocol (TCP) port scanner that distinguishes empowered TCP ports. Exactly when source send any message to particular focuses inside the structure then that debilitating focus additionally recoup that rub and misused all the data Impersonation strike is key driver of plotting assault in which exchanged off centre imbued toxic centre point into the framework likewise make number of imitated copy of vindictive centre for doing future attacks all in all framework. When a communication server requesting the vehicle users mobile number, there is a chance of Impersonation attack happening, when the attackers tries to impersonate the user.
Synopsis of the Theory
Vehicular interpersonal organizations have as of late drawn the consideration among scientists. They are making ready for an engaging sort of vehicular applications and administrations which are user-oriented furthermore, that go for encouraging social associations among workers out and about amid their day by day feared drives. Numerous specialists have been centring after concocting either disseminated or incorporated vehicular social frameworks that handle the particular needs of workers out and about. Be that as it may, and to the best of our insight where neither of them have offered a half and half vehicular social framework that underpins the advancement of brought together and circulated vehicular social applications and administrations while giving careful consideration to the hidden cross breed vehicular correspondence layers. In this proposition, we handled the issue of the absence of cross breed vehicular social correspondence reflections in the writing. We presented a novel, proficient, solid, half and half and Dynamic Informing Framework (DYMES) that empowers continuous social collaborations among workers amid their long drives utilizing an arrangement of effective, dynamic, appropriated and unified correspondence reflections. The main commitment of this postulation was to construct DYMES. To do as such, we initially recognized a meta-procedure to manage the outline of the appropriated and concentrated correspondence reflections on which it depends. We found that the distribute/buy in the show is an appealing answer for versatile processing and that it matches with the suburbanites' correspondence necessities, in a way that it enables them to distribute and buy into the data shared without even have the knowledge of everyone’s identity. We at that point outlined an arrangement of cross breed dynamic distribute/buy in reflections that permit workers to proficiently and dependably speak with each other in light of their logical data and without uncovering their personalities while considering the dynamic nature of the common data.
Our proposed dynamic distribute/buy in deliberations were then subdivide into a few unique commitments, all coming in the same compartment of the DYMES design. They were assessed furthermore, contrasted with the already proposed components and are abridged as takes after. The second commitment of this proposal was a Dynamic Distribute/Buy in Grouping Technique (DPSCS) that breaks the workers' social confinement out and about and enables them to be sorted out in stable intrigue based networks, without flooding the system. DPSCS presented a novel unique distribute/buy in a system that gives the chance to each suburbanite to assemble a steady and self-refreshed network in light of its own enthusiasm through the engendering of a solitary and dynamic distribution around him, for a decided term, leaving the web-based coordinating procedure to endorsers. Second, the proliferation of this industrious distribution all through the system was accomplished utilizing a novel two Shot-Stable Directing Administration (2S-SRS) that enhances the productivity and the dependability of the suburbanite's single distribution dispersed over the system through sending it utilizing hubs that have a stable availability of the one who sends, and are more distant from the sender's area, and closer to two limit focuses. DPSCS-2S-SRS stops the working of every worker's locale one the TTL of the worker's distribution lapses. Our outcomes demonstrated that DPSCS-2S-SRS prevails to assemble self-refreshed, proficient and dependable networks in under once second furthermore, that it beats its next equivalent approach by 27% to 28%, for any system measure, what's more, any thickness, and furthermore guarantees 100% unwavering quality for all investigated hub densities. The fifth commitment of this theory was SocialDrive, an online distribute/buy-in procedure for vehicles traveling in detachments. It handled the issue of spreading dynamic relevant refreshes in exceptionally thick and disseminated units, through expanding BroadTrip and utilizing it as a basic convention in the DYMES's engineering. SocialDrive permits workers to distribute their dynamic tenacious updates all through the system and to buy in utilizing an online setting mindful channel. Upon the conveyance of industrious updates, every endorser makes a membership and utilization the time at which he made its membership in the coordinating channel so as to contrast it and the time at which they got refreshes were issued. A match is sure, if and just if; timespan at which the diligent refresh was offered is close to the timespan at which the membership is made. SocialDrive-BroadTrip enhances the nature of social correspondence among suburbanites grouped in thick units and increments their driving solace by enabling them to get the most recent issued dynamic logical updates that goes with their hobbies and likings. Our outcomes demonstrated that SocialDrive outflanked the next best equivalent methodologies by 26% to 58% contingent upon settings.
By and large, the empowering comes about we acquired demonstrated that the DYMES' dynamic, effective, dependable, steady and mixture correspondence reflections can be utilized as a building obstruct for the advancement of any sort of vehicular social applications. Our outcomes likewise demonstrated that DYMES is the best half-and-half informing framework that productively and dependably meets the assorted suburbanites' necessities in half breed and thick vehicular conditions.
Constraints
In spite of the above promising outcomes, our discoveries are additionally presented to a few restrictions such as: In the previous chapter has a confinement that can prompt a fascinating future venture. It must be reviewed the offered broadcasting convention, BroadTrip permits to proficiently and dependably spread messages among vehicles traveling in companies. In actuality, in certain scanty settings where the separation between vehicles is over 50 meters, the unwavering quality of BroadTrip could definitely diminish due to the unique transmission abilities of a few hubs that may choose to retransmit a message and drop the timetable of their neighbors without achieving any new hubs. In the previous chapter proposed a Dynamic Distribute/Buy in Grouping Procedure in view of the two Shot Stable Steering Administration, (DPSCS-2S-SRS), that enables every worker to make a steady and self-refreshed intrigue based network through the engendering of a solitary dynamic and relentless production which flies all through the system utilizing steady and more distant hubs. Coordinating is performed by supporters in view of the distributer's current area, course and speed. The execution assessment of DPSCS system demonstrated that the match rate, which speaks to the number of suburbanites that match the source's distribution, diminishes as long as the thickness of hubs increments. This is because of the vehicles' developments dispersion produced by SUMO. We trust that this result would change on the off chance that we utilize a genuine development follow. Security remains a major worry of our work. The upsides of building nearness and intrigue based social networks keeping in mind the end goal to empower ongoing social collaborations among workers and to advance client arranged administrations in VSNs may prompt unwanted outcomes, for example, the spread of falsehood through data merchants to a few networks. In addition, albeit discharging data about area empowers numerous valuable area based administrations, it might raise numerous protection issues about the noxious utilize of area data. Also, and in spite of the way that anonymization (Hara et al., 2014) and obscuring (Shin et al., 2015) components guarantee and improve the client's protection by limiting the entrance to the character and to the area, there is as yet a need of vital examination on the protection and the security issues in VSNs.

Future Work
Our future research headings, for the most part, expand on the previously mentioned constraints. We diagram some of them as takes after. We intend to actualize DYMES in a genuine tested that will coordinate diverse remote advancements, for example, IEEE 802.11, 4G, LTE, among others, so as to evaluate DYMES's execution in genuine situations. Such tested investigations will make ready for further changes and will give suburbanites consistent remote network. It will likewise advance the multiplication of a plenty of continuous vehicular social applications, for example, web-based conferencing and gaming that will unquestionably shape the fate of the web of autos. We expect to enhance our proposed handover instrument with a specific end goal to enable hubs to set up an association with another BTS through a base number of new stable versatile doors. We likewise plan to research thoughts to help social trust systems keeping in mind the end goal to lessen the nearness of malevolent suburbanites over the system. The last may irritate the message scattering process amid social interchanges. It might likewise lead to unfortunate outcomes, for example, the spread of deception to a few social networks. Empowering social collaborations among suburbanites amid their roadway voyages makes them create a colossal measure of ongoing geosocial information, which changes VSNs to a Major Information issue. We intend to outline sufficient procedures and structures utilizing Enormous information dispersed innovations, with a specific end goal to find out about the dynamic sociological examples of workers out and about and to plan choice strategies ready to separate suburbanite driven administrations as indicated by their dynamic needs. We trust that examining these issues speaks to a noteworthy research road and we trust that the discoveries in this proposition may help fortify further work around there.
Conclusion
Over the last one decade, environmental pollution, accidents, and traffic congestion have become issues of concern in the transportation industry. To solve these problems, increased research has been focused on vehicular social networks (VSNs) and intelligent transportation systems (ITSs) in recent years. Vehicular social networks are a form of mobile networks, which allow nearby vehicles to communicate. Trust models in VSNs exist in three categories based on the object of consideration. These categories are: entity-based trust models which focus on evaluating the vehicles that send information, data-based trust models which focus on evaluating the data sent by vehicles within a network, and combined trust models which evaluate both the data sent and the vehicles which send the information. There are two main entity-based trust models. These are multi-faceted trust management model and sociological trust model. The sociological trust model is based on trust and confidence tagging. The data-based trust model focuses on evaluating the relevance and trustworthiness of data provided by other entities as opposed to evaluating the trustworthiness of the entities themselves. However, the adoption of VSNs has raised a number of concerns among which are: security and privacy, malicious participants, and selfish participants. There are a number of findings from this study.
One of them is existing systems, Pervaho and LMA have abused area data in their proposed distribute/buy in deliberations so as to fabricate a few setting mindful applications. As such, they regularly add the likelihood to restrain the dissemination of messages in a specific geological territory. They do not permit to distribute dynamic substance and just permit a few sorts of dynamic area based separating. In addition, they need productive and solid correspondence conventions ready to limit the overhead of the dispersed distributions/memberships. It was also established that the VSN system is also vulnerable to various types of attack. These include: replay attack, man in the middle attack, reflection attack, and impersonation attack. A replay assault happens when an aggressor duplicates a flood of messages between two gatherings and replays the stream to at least one of the gatherings. A man-in-the-middle assault is a sort of digital assault where a noxious on-screen character embeds herself into a discussion between two gatherings, imitates the two gatherings and accesses data that the two gatherings were attempting to send to one another. Impersonation assaults are propelled by utilizing other hub's character, for example, MAC or IP address.
Reflection assault is a technique for assaulting a test reaction verification framework that uses a similar convention in the two bearings. To deal with these challenges, there are a number of proposals were made. One of them is introduction of a dynamic informing framework for vehicular social systems known as DYMES. The objective of this proposed engineering is to advance ongoing social associations among suburbanites amid their roadway goes through proficient and dependable disseminated and unified vehicular correspondence deliberations. DYMES adapts to the workers' namelessness in very thick systems through a Dynamic Distribute/Buy in Grouping Technique (DPSCS). It enables every worker to make its own steady and self-refreshed vehicular network via a multicast of the solitary and determined message while guaranteeing high effectiveness and dependability all through thick dispersed systems. The topology of proposed dynamic informing design is the cross breed. The system situation thinks about three kinds of hub: normal vehicles, chose versatile passages which are going in separate two ways.
Another proposed solution in this study is the implementation of SocialDrive. SocialDrive permits workers to distribute their dynamic tenacious updates all through the system and to buy in utilizing an online setting mindful channel. To increase the privacy and trust of VSNs, it has been proposed in this paper that there is need to use the various protocols: Communication Protocols, Broadcasting Protocols, Counter based protocols, and Address based Protocols.
Despite these solutions, there are still constraints that make it hard for a high level security and privacy to be achieved in VSNs. For example, where the separation between vehicles is over 50 meters, the unwavering quality of BroadTrip could definitely diminish due to the unique transmission abilities of a few hubs that may choose to retransmit a message and drop the timetable of their neighbors without achieving any new hubs. Security also remains a major concern. The upsides of building nearness and intrigue based social networks keeping in mind the end goal to empower ongoing social collaborations among workers and to advance client arranged administrations in VSNs may prompt unwanted outcomes, for example, the spread of falsehood through data merchants to a few networks. Due to these persistence challenges which make it hard for VSNs to be totally secure and private, more work needs to be done in future.
References
Abbani, N., Jomaa, M., Tarhini, T., Artail, H. and El-Hajj, W., 2011, September. Managing social networks in vehicular networks using trust rules. In Wireless Technology and Applications (ISWTA), 2011 IEEE Symposium on (pp. 168-173). IEEE.
Alhajj, R. and Memon, N., 2011. Introduction to the second issue of Social Network Analysis and Mining journal: scientific computing for social network analysis and dynamicity.
Alpcan, T. and Başar, T., 2010. Network security: A decision and game-theoretic approach. Cambridge University Press.
An, W., 2015. Multilevel meta network analysis with application to studying network dynamics of network interventions. Social Networks, 43, pp.48-56.
Barbara, Ś., Barbara, K., Maciej, J., Justyna, KP, Alicja, JR, Małgorzata, T., Marek, B., Diana, J. and Andrzej, M., 2012. Publications of Employees Institute Mathematics I Informatics of Wrocław University of Technology in 2012. Endocrinology Polska ,
Basu, P., Khan, N. and Little, T.D., 2001, April. A mobility based metric for clustering in mobile ad hoc networks. In Distributed computing systems workshop, 2001 international conference on (pp. 413-418). IEEE.
Behrisch, M., Bieker, L., Erdmann, J. and Krajzewicz, D., 2011, October. Sumo–simulation of urban mobility. In The Third International Conference on Advances in System Simulation (SIMUL 2011), Barcelona, Spain (Vol. 42).
Bhat, P.T., Thankachan, R.V. and Chandrasekaran, K., 2015. Sharding distributed social databases using social network analysis. Social Network Analysis and Mining, 5(1), p.31.
Bhattacharjee, P.K., 2010. A four entities mutual authentication technique for vehicular ad hoc network. International Journal of Computer and Electrical Engineering, 2(4), p.617.
Braun, T., Diaz, M., Gabeiras, J.E. and Staub, T., 2008. End-to-end quality of service over heterogeneous networks. Springer Science & Business Media.
Breiger, R.L., Schoon, E., Melamed, D., Asal, V. and Rethemeyer, R.K., 2014. Comparative configurational analysis as a two-mode network problem: A study of terrorist group engagement in the drug trade. Social Networks, 36, pp.23-39.
Buch‐Hansen, H., 2014. Social network analysis and critical realism. Journal for the Theory of Social Behaviour, 44(3), pp.306-325.
Dotzer, F., Fischer, L. and Magiera, P., 2005, June. Vars: A vehicle ad-hoc network reputation system. In World of Wireless Mobile and Multimedia Networks, 2005. WoWMoM 2005. Sixth IEEE International Symposium on a (pp. 454-456). IEEE.
Dudek, A., 2016. Social Network Analysis as an Exhibition of Multi-Dimensional Statistical Analysis Social Network Analysis as A Branch of Multidimensional Statistical Analysis.
Eugster, P., Garbinato, G., Holzer, A. and Luo, J., 2009. Effective location-based publish/subscribe in manets. In IEEE International Conference on Pervasive Computing and Communications (PerCom’09).
Fei, R., Yang, K. and Cheng, X., 2011, April. A cooperative social and vehicular network and its dynamic bandwidth allocation algorithms. In Computer Communications Workshops (INFOCOM WKSHPS), 2011 IEEE Conference on(pp. 63-67). IEEE.
Force, U.T.T., 2012. The high cost of congestion in canadian cities. Council of Ministers Transportation and Highway Safety.
Freeman, L.C., 1978. Centrality in social networks conceptual clarification. Social networks, 1(3), pp.215-239.
Friesz, T.L. and Bernstein, D., 2016. Foundations of network optimization and games. Springer.
Garbinato, B., Holzer, A. and Vessaz, F., 2008, November. Six-shot broadcast: A context-aware algorithm for efficient message diffusion in manets. In OTM Confederated International Conferences" On the Move to Meaningful Internet Systems" (pp. 625-638). Springer, Berlin, Heidelberg.
Geurts, J., 2010. Simulation of distributed storage using OMNET++. Auckland, N.Z.: Engineering Science, School of Engineering, University of Auckland.
Gilbert, E. and Karahalios, K., 2009, April. Predicting tie strength with social media. In Proceedings of the SIGCHI conference on human factors in computing systems (pp. 211-220). ACM.
Hamidi, A., Ganti, S. and Wu, K., 2008, November. An aggregative approach for scalable detection of DoS attacks. In Global Telecommunications Conference, 2008. IEEE GLOBECOM 2008. IEEE (pp. 1-5). IEEE.
Han, L., 2013. Social caching and vehicular social networks: two contributions to the theory and practice of online social networks (Doctoral dissertation, Rutgers University-Graduate School-New Brunswick).
Hua, L.C., Anisi, M.H., Yee, L. and Alam, M., 2017. Social networking-based cooperation mechanisms in vehicular ad-hoc network—a survey. Vehicular Communications.
Huang, Z., Ruj, S., Cavenaghi, M.A., Stojmenovic, M. and Nayak, A., 2014. A social network approach to trust management in VANETs. Peer-to-Peer Networking and Applications, 7(3), pp.229-242.
Hussain, F., 2017. Internet of things: Building blocks and business models (No. 978-3, pp. 319-55404). Springer International Publishing.
Kadushin, C., 2005. Who benefits from network analysis: ethics of social network research. Social Networks, 27(2), pp.139-153.
Litman, T., 2016. Smart congestion relief: Comprehensive analysis of traffic congestion costs and congestion reduction benefits.
Liu, H., Han, J. and Motoda, H., 2014. Uncovering deception in social media.
Mavromoustakis, C.X., Mastorakis, G. and Batalla, J.M. eds., 2016. Internet of Things (IoT) in 5G mobile technologies (Vol. 8). Springer.
Meghanathan, N., 2017. Randomness Index for complex network analysis. Social Network Analysis and Mining, 7(1), p.25.
Minhas, U.F., Zhang, J., Tran, T. and Cohen, R., 2010. Towards expanded trust management for agents in vehicular ad-hoc networks. International Journal of Computational Intelligence: Theory and Practice (IJCITP), 5(1), pp.03-15.
Miranda, H., Leggio, S., Rodrigues, L. and Raatikainen, K., 2006, September. A power-aware broadcasting algorithm. In Personal, Indoor and Mobile Radio Communications, 2006 IEEE 17th International Symposium on (pp. 1-5). IEEE.
Ning, Z., Xia, F., Ullah, N., Kong, X. and Hu, X., 2017. Vehicular Social Networks: Enabling Smart Mobility. IEEE Communications Magazine, 55(5), pp.16-55.
Nohuddin, P., Coenen, F. and Christley, R., 2016. The application of social network mining to cattle movement analysis: introducing the predictive trend mining framework. Social Network Analysis and Mining, 6(1), p.45.
O’Loughlin, E. and Payne, D., 2014. Building rich social network data: a schema to assist in designing, collecting and evaluating social network data. Social Network Analysis and Mining, 4(1), p.198.
Palazzi, C.E., Roccetti, M., Ferretti, S., Pau, G. and Gerla, M., 2007. Online games on wheels: Fast game event delivery in vehicular ad-hoc networks. Proc. of Vehicle-to-Vehicle Communications.
Pallis, G., Katsaros, D., Dikaiakos, M.D., Loulloudes, N. and Tassiulas, L., 2009, September. On the structure and evolution of vehicular networks. In Modeling, Analysis & Simulation of Computer and Telecommunication Systems, 2009. MASCOTS'09. IEEE International Symposium on (pp. 1-10). IEEE.
Peng, S., Wang, G. and Xie, D., 2017. Social Influence Analysis in Social Networking Big Data: Opportunities and Challenges. IEEE Network, 31(1), pp.11-17.
Raya, M., Papadimitratos, P., Gligor, V.D. and Hubaux, J.P., 2008, April. On data-centric trust establishment in ephemeral ad hoc networks. In INFOCOM 2008. The 27th Conference on Computer Communications. IEEE (pp. 1238-1246). IEEE.
Scott, J., 2011. Social network analysis: developments, advances, and prospects. Social network analysis and mining, 1(1), pp.21-26.
Susanto, B., Lina, H. and Chrismanto, A.R., 2012. Penerapan Social Network Analysis dalam Penentuan Centrality Studi Kasus Social Network Twitter. Jurnal Informatika, 8(1).
Taleb, T., Sakhaee, E., Jamalipour, A., Hashimoto, K., Kato, N. and Nemoto, Y., 2007. A stable routing protocol to support ITS services in VANET networks. IEEE Transactions on Vehicular technology, 56(6), pp.3337-3347.
Tseng, Y.C., Ni, S.Y., Chen, Y.S. and Sheu, J.P., 2002. The broadcast storm problem in a mobile ad hoc network. Wireless networks, 8(2-3), pp.153-167.
Vo, B. and Bellovin, S., 2014, September. Anonymous publish-subscribe systems. In International Conference on Security and Privacy in Communication Systems (pp. 195-211). Springer, Cham.
Wex, P., Breuer, J., Held, A., Leinmuller, T. and Delgrossi, L., 2008, May. Trust issues for vehicular ad hoc networks. In Vehicular Technology Conference, 2008. VTC Spring 2008. IEEE (pp. 2800-2804). IEEE.
Wilson, A.G., 2014. Complex spatial systems: the modelling foundations of urban and regional analysis. Routledge.
Yang, Q. and Wang, H., 2015. Toward trustworthy vehicular social networks. IEEE Communications Magazine, 53(8), pp.42-47.
Zeadally, S., Hunt, R., Chen, Y.S., Irwin, A. and Hassan, A., 2012. Vehicular ad hoc networks (VANETS): status, results, and challenges. Telecommunication Systems, 50(4), pp.217-241.
Zhang, J., 2011, March. A survey on trust management for vanets. In Advanced information networking and applications (AINA), 2011 IEEE international conference on (pp. 105-112). IEEE.
Zhao, Y. and Wu, J., 2010, April. Socially-aware publish/subscribe system for human networks. In Wireless Communications and Networking Conference (WCNC), 2010 IEEE (pp. 1-6). IEEE. DOI: 10.1109
Ziegler, C.N. and Golbeck, J., 2007. Investigating interactions of trust and interest similarity. Decision support systems, 43(2), pp.460-475
- 24/7 Customer Support
- 100% Customer Satisfaction
- No Privacy Violation
- Quick Services
- Subject Experts



