Understanding Terrorist Group Funding Mechanisms
Introduction
Financing Terror
Identifying the target of terrorist funding requires the understanding of the purpose of the terrorist group. According to Bernasco (2010), the costs required is not only associated with conducting the terrorist attack but also to develop and maintain the terrorist organization and its significant ideologies. The funding encompasses militant ideology of the group, payment to the operatives and their families, travel arrangement, training of new members, paying of bribes, forging documents, acquisition of weapons, and staging of attacks. More often, the terrorist group conducts variety of higher cost services that include superficial legitimate charitable or social activities including propaganda in order to acquire a veil of legitimacy for its organization and promotion of their terrorism objectives. In contrary, Ryder, Thomas and Webb (2018) indicate that the nature of terrorist funding encompasses both the broader and operational funding activities that varies with the type of terrorist organization, such as hierarchical, quasi-static or traditional whereas decentralized, small and independently supported organizations are present on the other side of spectrum.
EVIL DONE model
The framework of EVILDONE is based on their theories of “situational criminology” that are mainly applied to violent acts such as terrorism. The primary objective of EVIL DONE is to identify the vulnerable targets by realizing the features of significant locations that makes the place more vulnerable for an attack. The key elements of EVIL DONE include the following-
Exposed
Vital
Iconic
Legitimate
Destructible
Occupied
Near and Easy
Assessment of risks in a particular location integrating the EVIL DONE factors assists the local authorities in identifying the places vulnerable to terrorist attack (Paton, 2013). Each elements of EVILDONE acting as the intelligent cycle to determine the funding are demonstrated herein,

Exposed- The amount of exposure is conditional to the type of environment, landscape style and structures surrounding the target. The example of exposed targets is mainly the high rise Twin Towers, statue of Liberty, etc.
Vitals- This includes the food and water supply sources, transportation and electric grid systems. These vital targets attract terrorists attack due to the their ability of causing chaos when they are inoperative.
Iconic- The symbols representing nation’s unity and power often attract the terrorists who attempts to impair these strength figuratively to destruct the country’s heritage. Examples of Iconic variables include White House, Statue of Liberty.
Legitimate- The legitimate targets considers the authoritative bodies that will bring positive scope from the supporters of terrorists or for the terror organization. While terrorists are rational beings, they largely seek the legitimate and governing bodies to avoid condemnation, and negative consequences (Clarke, 2018). Consequently, the terrorists seek certain targets that are viewed as legitimate such as the Charities, legitimate social businesses, orphan houses to acquire funding and also acts as a veil to their illegitimate misconduct.
Destructible- It refers to the ability required to destroy the target which can be in terms of financial or fund investment, accessibility of weapon essential to destroy the target. Hence, substantial funding is essential to destroy a person using advanced weapons that are generally expensive.
Occupied- Terrorists typically target to harm large mass in order to intensify their purpose (i.e. enhancing legitimacy and terror, etc). Hence, the locations with highest populations or large building having large number of occupants attract the terrorists to exert harm and spread fear throughout the targeted community.
Near- The theories of criminology and crime pattern models emphasized that the terrorists are prefer staying closer to the target location in order to avoid travelling long distances to commit crime.
Easy- Targets that are weakly protected or accessible to public are known as Easy. It relates to the minimum effort required to obtain access to such locations due to the lack of security measures.
Continue your journey with our comprehensive guide to Understanding Terrorist Group Funding Mechanisms.
Critical analysis
The assessment of EVIL DONE model can effectively develop risk assessment which is applied for the purpose of terrorists’ opportunity reduction. However, this model acts as the intelligent cycle to determine the potential target attack, instead of much focus on the prediction of financial exploitation of terrorists. On review, only two of the elements i.e. Legitimate and Destructible does address the financial exploitation of terrorists using the legitimate charities and financial assistant required for funding essential and advanced weapons. According to Špačková and Straub (2015), multiple methodologies does exist for vulnerability assessment, however most of these paradigms revolves around the criminology assessment instead of financial exploitation by the terrorists. Some methodologies like Quantitative Terrorism risk assessment, FIVAM (Fuzzy integrated vulnerability Assessment model), I-VAM (Integrated Vulnerability assessment model) are some of them that are used in risk assessment of the next target attack. Additionally, these models are centered on highly convoluted mathematical formulas and scientific methods that typically require master level expertise. Hence, these significant models are not applicable to the state or local jurisdictions neither are they relevant to the sector of criminal justice. Contrastingly, Freeman (2016) studied the quantitative Terrorism risk assessment model which are exclusively based on the relationship between demand and supply within the insurance market, without the basis for actuarial principles. Quantitative assessment of the terrorism risk is achievable only if it addresses the challenges of and provides the foundation for financial transaction and security for terrorism risks. This in combination with other finance based models existing provides significant guidance to measure the vulnerability of financial exploitation or potential targets, however despite of its existence, the results for analytical testing for these models is not available (Ionescu, 2015). Critically, inspite of the absence is models based testing of financial exploitation by terrorists group, few special departments have concluded generalized findings on the critical attributes and infrastructure related to financial terrorism.
The Routine Activity Approach (RAA)
The RAA is a theoretical sociological perspective which consists of “three minimal elements of the direct contact predatory violations” that was mainly built to address the crimes and violent assaults where one person is accused of damaging the property of others. These three key elements include (1) a suitable target, (2) the potential offender, (3) the nonexistence of potential guardians (Argun and Dağlar, 2016). These following elements are considered the mandatory and adequate conditions for committing the crimes, because this is the temporal and spatial convergence giving rise to the opportunity for crime. Based on this theoretical implication, the terrorist attack or crime could not be determined even if one of these elements lack in the model.
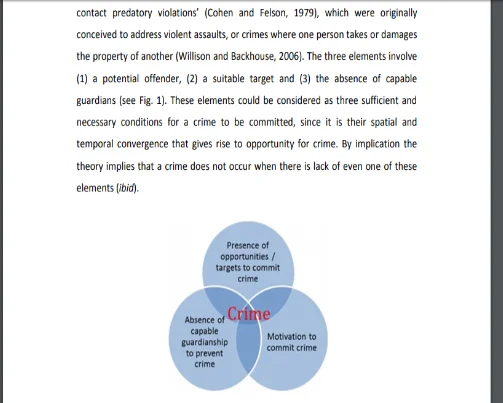
Milošević (2017) opined a concise explanation on the key assumptions of RAA stating that “at the fundamental level this theory attempts to locate the offenders, target and guardians at specific places, offers measurable relations of distance and spatial proximity pertaining between the potential offenders and target, whereas the social activities are ordered in respect to rhythms so that each of these agents are typically absent or present at specific times.
Critically, Compin (2016) enlighten the other essential aspect of RAA, assuming that the motivated offenders are always inclined towards the commitment of crime on having a favorable opportunity. Alternatively, the RAA is largely influenced by the Rational Choice theory which is assumed to motivate the offenders for carrying out risk assessment before committing a crime to determine the anticipated benefits, risks and costs involved in the act. For instance, suitability of the target is estimated in accordance to the fourfold constituent elements that are rendered through the VIVA (Value, Inertia, Visibility, Accessibility) which also refers to two specific elements of the RAA i.e. the opportunity to strike a target and lack of potential guardians.
Tudor (2014) opined that guardianship refers to the capability of objects or persons to prevent the occurrence of crime. In RAA theory, the guardians are generally crucial whose roles are either direct intervention that acts as restrictions, or by the staying in close proximity to the target thereby reminding the potential offender about the vigilant watchdog. Contrastingly, Lasley and Guffey (2017) creates a distinction between the formal, informal and technical controls deriving from the TFI model. The formal controls mainly involves following of rules, that often relates to regulatory compliance, information security policies, and compliance for approved organizational processes. The informal control refers to the provision of overall information security along with the cultivation of security culture that positively encourage incident reporting, and obedience. Lastly, the technical controls are mainly traditional in nature that addresses issues related to access management.
The application of RAA is primarily applied at the organizational and societal level with the intention to minimize crime opportunities in context of routine activities of the potential offenders. Routine activity theory offers micro and macro options for minimizing crime specifically the acquisitive crime by protecting the target and evading motivation of offenders instead of eliminating the motivated offenders (Argun and Dağlar , 2016).Critically, RAA is also criticized with facts that this theory must focus on the likely offender or a suitable target and a credible guardianship to overcome the use of dummy CCTVs. These theories does not necessarily evolve to prevent crime, instead it provides the basis for objective analysis using temporal and spatial vision in the crime patterns.
Critical analysis
The literature on financing terrorism has largely emphasized on the greater opportunism and adaptability the terrorists deploy in order to meet their funding requisitions. The terror networks employ multiple organizational structures, along with the consistent evolution of fraudulent techniques in response to the international measures and the opportunistic terrorist financing nature makes it critical for any fundamental models to identify the most common and favored method of financing. According to Lemanski and Wilson (2016), there are three key methods used by the terrorists to transfer money that include (1) use of financial systems, (2) physical movement of money through cash couriers, and (3) International trading systems. In contrary, Romyn and Kebbell (2014) opined that terrorist organizations are found to abuse the charities, ARS (alternative remittance systems), or other captive and legitimate entities to maintain the terrorist operation. In argument, Reyns et al (2016) points out that Regular funding to the terrorist groups are optimally facilitated through the traditional banking systems. In clear instincts, money is transferred from one country to another under deceptive false accounts, charity, and legitimate business, to disguise the financial trails of terrorists.
In many situations, the funds raised, transfer and utilization of funds for terrorism is challenging to determine by using these models, because it is significantly distinctive from the attributes used in the model. Precisely, disruption and identification of terrorist finance is naturally complicated when the authorities are confronted using “informal” network of financing and support that does not work for the well-structures frameworks that require clear lines and roles of accountability (Pratt and Turanovic, 2016). In such instances, the links of terrorist activity with financial activity becomes highly opaque, hence identifying the target for disruption become complex.
Raising funds from legitimate sources
The terrorists’ organization receives substantial amount of funding and support through the legitimate sources that include social businesses, charities, or self-funding by the terrorists. This relates to the phenomenon referred as “black washing” where the legal funds (money stemming from governmental subsidies, social benefit, charities) are utilized for the purpose of terrorism (Špačková and Straub, 2015). The terror networks make use of complicit and compromised charities to support their terrorism objectives. For instance, charities having global presence provide the framework for international and national operations, financial transactions across the areas that are largely exposed to terrorism.
Charity
The risk profiles of Charities include the following-
Fraudulent diversion of funds- For instance, the donors encouraged for investment in orphan, whereas the charity divert the funds to terrorists. Such activities occur alongside the otherwise legitimate charity work.
The establishment of sham or bogus organization that are represented as the front organization for terror group.
Social business as a source
The legitimate business is often used as the source of funding to support the terrorist activities. Such businesses has the risk of diverting the funds to terrorists organization particularly where the relation between reported sales and actual sales are difficult to verify specifically in the cash-intensive businesses.
Self-Funding
The Terrorists groups are often funded from the internal sources such as non-criminal or family based sources. Moreover, the amount of funds required to mount the smaller attacks are raised from individual terrorists or through their support networks using the access to credit cards, savings, or businesses (Freeman, 2016).The Terrorists organizations are self-funding and largely decentralized in which even a relatively external autonomous financial investor who is not involved in the planning and execution of terror attack directly can contribute in funding.
Critical Analysis
Hence, the terrorists groups were raising funds and support from the state sponsors or legitimate organizations of terrorism. On critical evaluation it has been found that due to the increasing international pressure and greater security measures, funding from such sources have become less reliable and in some instances, the funding has disappeared at large. Additionally, Ionescu (2015) point out that the new and decentralized cell does not have similar level of access to the foreign funding as the traditional group of expert terrorists. Consequently, the terrorists groups have largely turned towards the alternative sources of financial that mainly enlighten the criminal activities such as extortion, drug trafficking, kidnapping, and racketing. The terrorists leveraging the criminal activities to raise funds significantly ranges from lower level of fraud to the involvement in organized and serious crime. However, it often becomes difficult to determine whether the funds being raised by these criminal activities are actually intended towards terrorism, or simply to proceed the basic criminal activity (Compin,2016). Hence, in order to obtain financing for terrorism, the terrorists get involved in the following criminal activities demonstrated in the next portion.
Funds from Criminal activities
Trafficking of drugs
The most common and attractive funding source for terrorism that enable raising huge sum of money. The degree of relying on drug trafficking as the key source of financing terrorism has extensively grown with the downturn of state sponsorship or legitimate funding to terrorists groups. Both the terrorist groups and trafficking organizations continues to establish their alliances and international networks of convenient funding (Lemanski and Wilson,2016). The increasing trend of globalization has rendered opportunity to both the crime and terror organization to diversify and expand their activities by taking advantage of financial institutions and banking systems thereby proliferating scope for facilitating their activities immensely.

Credit Card Fraud
The technique of allegedly obtaining the personal details such as credit card and account numbers, full name of the credit card holder, start and expiry dates, telephone number, security number, billing address, etc to obtain illegal access and misuses for financing terrorism.
Extortion
The paramilitary groups and terrorism supporters exploit their presence within the diaspora community to raise funds through the extortion. The terrorist organization is often found to utilize contacts to tax the diaspora on their savings and earnings. According to Pratt and Turanovic (2016), extortion is generally targeted against the own communities having higher level of retribution fear further affecting the enforcement action of law. The extortion collected from the diaspora communities is a consistent and significant source of funding. Reportedly, the previous activities of extortion enabled the terrorists group to collected upto 1 million USD a month in 2001 from the expatriates of Australia, Canada, Switzerland, Britain thereby making them the highly funded terrorist group in the world (Špačková and Straub, 2015). Reportedly, there were extortion claims on expatriate businesses upto GBP 100000 in UK and CAD 100000 in Canada respectively, along with equally higher demands made to Norway and France.
Reference List
Argun, U. and Dağlar, M., 2016. Examination of Routine Activities Theory by the property crime. Journal of Human Sciences, 13(1), pp.1188-1198.
Bernasco, W., 2010. A sentimental journey to crime: Effects of residential history on crime location choice. Criminology, 48(2), pp.389-416.
Compin, F., 2016. Financing Terrorism and Money Laundering: Dangerous Liaisons or State manipulation?. L'Homme et la société, (1), pp.159-172.
Freeman, M., 2016. Sources of Terrorist Financing: Theory and Typology. In Financing Terrorism (pp. 17-36). Routledge.
Lasley, J. and Guffey, J., 2017. A US military perspective on the promise of Situational Crime Prevention for combating terrorism. Journal of Policing, Intelligence and Counter Terrorism, 12(2), pp.85-104.
Lemanski, L. and Wilson, M., 2016. Targeting strategies in single-issue bomb attacks. Security Journal, 29(1), pp.53-71.
Milošević, B., 2017. Money laundering as a form of economic crime in the role of financing terrorism. Facta Universitatis, Series: Law and Politics, pp.549-560.
Paton, S., 2013. EVIL DONE Vulnerability Assessment: Examining Terrorist Targets Through Situational Crime Prevention. Florida Atlantic University.
Pratt, T.C. and Turanovic, J.J., 2016. Lifestyle and routine activity theories revisited: The importance of “risk” to the study of victimization. Victims & Offenders, 11(3), pp.335-354.
Reyns, B.W., Henson, B., Fisher, B.S., Fox, K.A. and Nobles, M.R., 2016. A gendered lifestyle-routine activity approach to explaining stalking victimization in Canada. Journal of interpersonal violence, 31(9), pp.1719-1743.
Romyn, D. and Kebbell, M., 2014. Terrorists' planning of attacks: a simulated ‘red-team’investigation into decision-making. Psychology, Crime & Law, 20(5), pp.480-496.
Ryder, N., Thomas, R. and Webb, G., 2018. The financial war on terrorism: A critical review of the United Kingdom’s counter-terrorist financing strategies. In The Palgrave Handbook of Criminal and Terrorism Financing Law (pp. 781-806). Palgrave Macmillan, Cham.
Špačková, O. and Straub, D., 2015. Cost‐benefit analysis for optimization of risk protection under budget constraints. Risk Analysis, 35(5), pp.941-959.
Tudor, F., 2014. Role of Customs and Border Cooperation in Fighting the Terrorism Financing and Funding Proliferation. AGORA Int'l J. Jurid. Sci., p.181.
- 24/7 Customer Support
- 100% Customer Satisfaction
- No Privacy Violation
- Quick Services
- Subject Experts



